Invented by Jun Wu, Xiaodong Zeng, Huanmi Yin, Feng Lin, Advanced New Technologies Co Ltd
Traditional methods of identity verification, such as passwords, PINs, and even biometrics like fingerprints or facial recognition, have proven to be susceptible to hacking and fraud. Cybercriminals have become increasingly adept at bypassing these security measures, leading to a surge in identity theft and fraud cases. As a result, businesses and organizations are seeking more robust and innovative solutions to protect themselves and their customers.
Virtual reality identity verification leverages the power of VR technology to create a secure and immersive environment for identity verification. By combining biometric data with VR simulations, individuals can authenticate their identity in a more foolproof manner. This technology can be used in various industries, including banking, e-commerce, healthcare, and even government agencies.
One of the key advantages of VR identity verification is its ability to provide a multi-factor authentication process. Instead of relying solely on a password or a fingerprint, VR identity verification can incorporate multiple biometric factors, such as voice recognition, hand gestures, and even eye movements. This multi-factor authentication significantly reduces the risk of identity theft and fraud, as it becomes nearly impossible for cybercriminals to replicate all these factors simultaneously.
Moreover, VR identity verification offers a more user-friendly and convenient experience for individuals. Instead of remembering complex passwords or carrying physical identification documents, users can simply put on a VR headset and authenticate their identity through natural gestures and movements. This not only enhances security but also improves the overall user experience.
The market for VR identity verification is expected to witness significant growth in the coming years. According to a report by MarketsandMarkets, the global market for biometrics in VR is projected to reach $3.8 billion by 2024, growing at a compound annual growth rate (CAGR) of 30.2%. This growth can be attributed to the increasing adoption of VR technology across various industries and the growing need for secure identity verification methods.
Several companies are already capitalizing on this emerging market. For instance, companies like EyeVerify and Sensory are developing VR-based biometric authentication solutions that leverage eye movements and voice recognition. These solutions have gained traction in the financial industry, where secure identity verification is crucial for preventing fraudulent transactions.
However, challenges still exist in the widespread adoption of VR identity verification. The cost of VR hardware and software, as well as the need for user education and acceptance, are some of the barriers that need to be overcome. Additionally, concerns regarding privacy and data security must be addressed to gain trust from individuals and regulatory bodies.
In conclusion, the market for virtual reality identity verification is poised for significant growth as businesses and organizations seek more secure and reliable methods to verify individuals’ identities. VR technology offers a unique and immersive solution that combines multiple biometric factors, enhancing security and user experience. While challenges exist, the potential benefits of VR identity verification make it a promising market for innovation and growth in the coming years.
The Advanced New Technologies Co Ltd invention works as follows
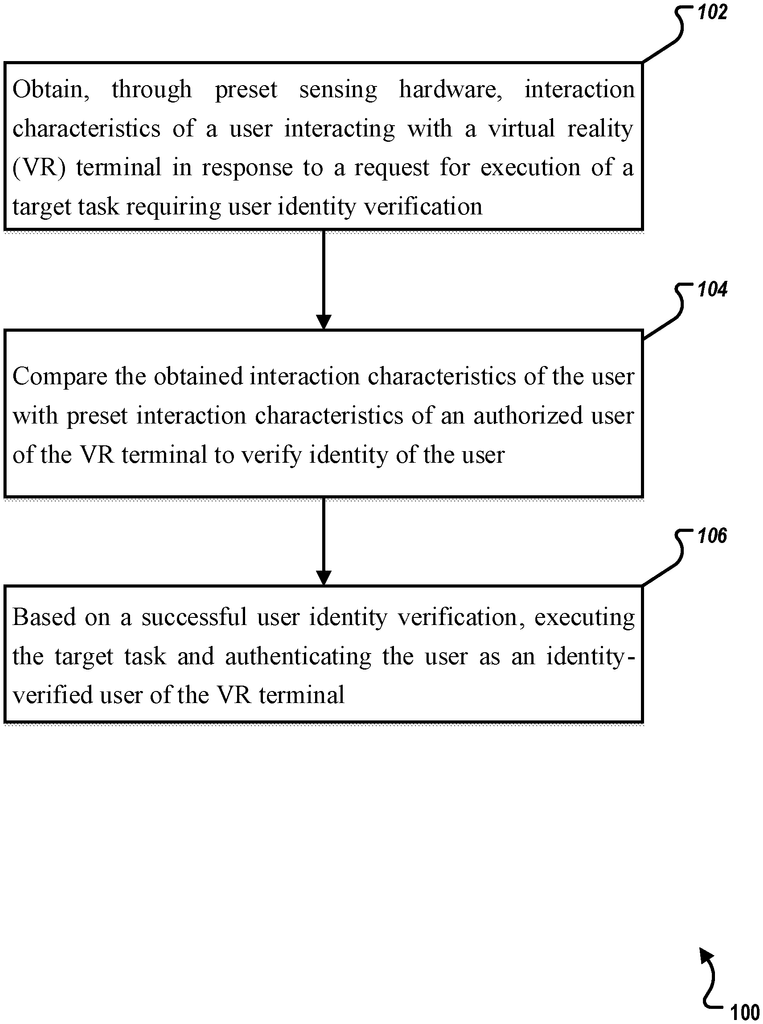
Interaction characteristics are obtained by preset sensing hardware of a user who interacts with a VR terminal in response to an execution request of a target job requiring verification of user identity. To verify the identity of the VR user, the obtained interaction characteristics are compared to preset interaction features of authorized users of the VR terminal. “The target task is completed and the user is verified as an identity-verified VR terminal user based on successful user identification verification.
Background for Virtual reality identity verification
Virtual Reality (VR), a technology that creates an interactive 3D environment on a PC using computer graphics and a variety of control interfaces to provide a user an immersive experience, is a new way of presenting a virtual world. VR terminals can include a headset and glasses. VR terminals and applications are growing in popularity as VR hardware and technology matures.
The present disclosure describes systems and methods, including computer-implemented systems, computer program products and computer systems, for verifying the identity of an user of a VR terminal.
In one implementation, the interaction characteristics of a VR terminal user are obtained by preset sensing equipment in response to an execution request of a target job requiring verification of user identity. To verify the identity of the person, the obtained interaction characteristics are compared to preset interaction features of authorized users of the VR terminal. “The target task is completed and the user is authenticated based on successful identity verification as an authorized user of the VR Terminal.
Implementations can be made of the described subject matter using a computer, a nontransitory computer-readable medium that stores computer-readable instructions to execute the computerimplemented methods; and a computer, implemented system consisting of one or more computer memory device interoperably coupled together with one or several computers. The tangible, nontransitory media contains instructions that when executed by one or more machines, execute the computerimplemented methods/the nontransitory computer-readable media.
The subject matter described herein can be implemented into specific implementations to achieve one or more of these advantages. The disclosed approach can first be used to confirm an identity of a wearer of a VR terminal. User identity verification can facilitate VR tasks that rely on the verification of user identity. After the initial user identification verification, the verification can continue on a regular basis. This can add an extra layer of security to protect against fraud. Third, additional identity verification processes are possible to improve user security during a VR session. “Those with ordinary skill will also be able to see other advantages.
The Claims and Detailed Description contain details about one or more implementations for the subject matter in this specification. The Claims and the accompanying drawings will reveal other features, aspects and benefits of the subject matter.
DESCRIPTION of Drawings
FIG. “FIG.
FIG. “FIG.
FIG. “FIG. According to a particular implementation of the disclosure, FIG.
FIG. “FIG.
Like references numbers and designations in various drawings indicate like components.
The following detailed description is intended to allow anyone skilled in the art, to use and make the disclosed subject matter within the context of one, or more, particular implementations. The disclosed implementations are capable of being modified, altered, or permuted in a variety of ways that will be obvious to anyone with ordinary skill. Furthermore, the general principles can be used to implement and apply to other applications and implementations without departing the scope of this disclosure. Details that are not necessary to understand the subject matter described can be omitted in some cases, as long as they do not obscure the implementations described and as long as the details are within the scope of a person of ordinary skill. The present disclosure does not intend to limit itself to the implementations described or illustrated, but rather to encompass the broadest scope possible consistent with the principles and features described.
A VR terminal” is a device that implements VR technology. It provides the user with a 3D immersive experience. The VR terminal generally outputs different VR scenario models that are developed to represent different VR environments. VR scenarios are developed for an operating system, such as a Virtual Reality Operation System.
In general a VR model can be made by a developer with a VR modeling program (such as UNITY, 3DS Max, or PHOTOSHOP). In some cases, both the VR model and texture map can be developed or derived from a real-life scene (such as a landscape, interior of a building, storefront and so on). Texture can be created by using photographs of an existing scenario. A 3D model can then be recreated with the VR modeling tools.
Once textures and 3D models of the VR scenarios have been created, they are imported into a VR engine such as UNITY 3D PLATFORMER. The U3D platform renders a VR scenario in multiple sensory dimensions (such as sound effects, plug-ins and lighting effects), including a GUI. After the VR scenarios sensory aspects have been created, interaction codes that govern the rules of interaction between the VR and the user are written. This completes the VR model.
Users can perform a variety of activities, which may require the verification of their identity. These tasks are called “target tasks”. The target task could include, for example, unlocking the VR terminal, performing fast payment transactions, or logging into an online account. “As such, maintaining the integrity of the VR terminal’s user identification verification process is a crucial issue.
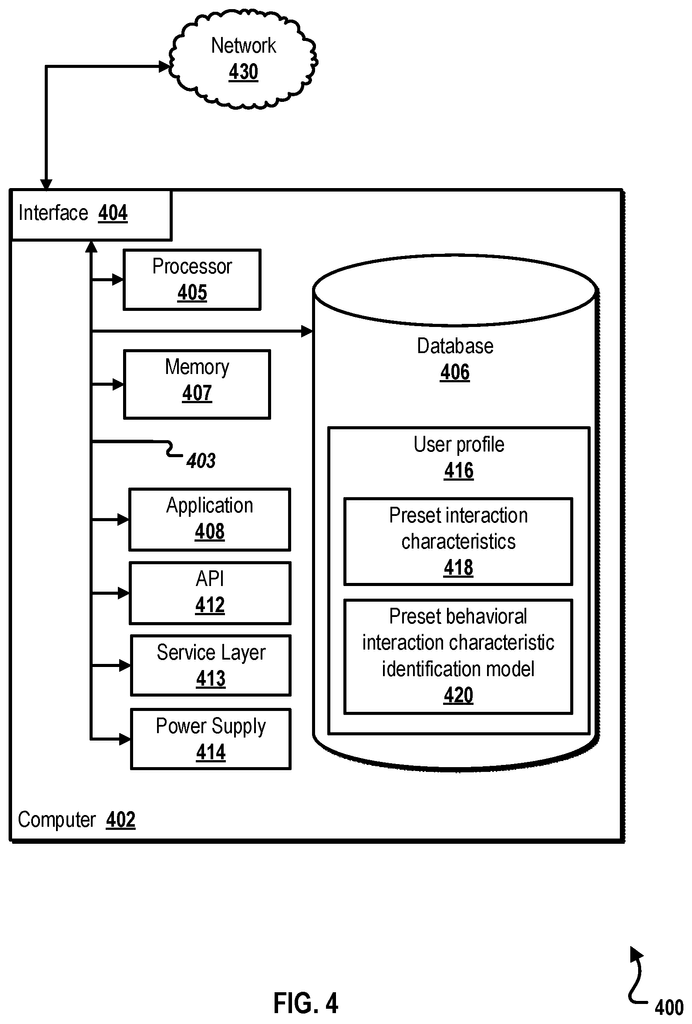
Interaction characteristics” refers to the way in which a user interacts during a VR experience. Interaction characteristics include, for example, the typical head position of a user, 3D gestures with a hand or a displacement tracking. These interaction characteristics may be used to verify the identity of a VR terminal user. Certain interaction characteristics between a user and a VR terminal may reflect unique behavioral traits of the user. In this way, the interaction characteristics of a user can be used in order to improve the security of the ID verification process during the VR session.
VR terminals may include various sensing equipment that can be used to obtain different interaction characteristics from the user. Sensing hardware can include an infrared camera, a radar, a laser, a gyroscope and an accelerometer. “The interaction characteristics of the users can be used to identify behavioral factors that are unique to each user.
FIG. The flow chart 1 illustrates an example of how to verify the identity of an user of a virtual-reality terminal according to a particular implementation of this disclosure. To make the presentation clearer, the following description will describe method 100 within the context of other figures. It is understood, however, that method 100 may be performed by any combination of software, hardware, systems, environments and software. In some implementations the method 100’s steps can be performed in parallel, combination, loops or any order.
In response to an execution request of a target action requiring user identification verification, “At 102”, interaction characteristics of the user interacting with a VR terminal are obtained by preset sensing equipment. In a VR session the user may trigger various target actions requiring user identification verification (such unlocking the VR Terminal, performing a quick payment transaction and logging in to an account).
Click here to view the patent on Google Patents.