Invented by Srinivas Kumar, Atul Gupta, Ruslan Ulanov, Shreya Uchil, Digicert Inc
The system and method for recording device lifecycle transactions as versioned blocks in a blockchain network using a transaction is a process that involves recording every transaction related to a device on a blockchain network. The blockchain network is a decentralized, distributed ledger that records all transactions in a secure and transparent manner. The system and method for recording device lifecycle transactions as versioned blocks in a blockchain network using a transaction is designed to provide a tamper-proof record of all transactions related to a device.
The market for this technology is growing rapidly, as more and more companies are realizing the benefits of using blockchain technology to track the lifecycle of devices. The system and method for recording device lifecycle transactions as versioned blocks in a blockchain network using a transaction is particularly useful for companies that deal with large numbers of devices, such as manufacturers, distributors, and retailers.
One of the main benefits of using this technology is that it provides a secure and transparent way of recording transactions. The blockchain network is designed to be tamper-proof, which means that once a transaction is recorded on the blockchain, it cannot be altered or deleted. This provides a high level of security and ensures that all transactions related to a device are recorded accurately.
Another benefit of using this technology is that it provides a transparent record of all transactions related to a device. This means that all parties involved in the lifecycle of a device can access the same information, which can help to reduce disputes and improve communication between parties.
The market for the system and method for recording device lifecycle transactions as versioned blocks in a blockchain network using a transaction is expected to continue to grow in the coming years. As more companies adopt blockchain technology, the demand for this technology is likely to increase. This is particularly true for companies that deal with large numbers of devices, as the system and method for recording device lifecycle transactions as versioned blocks in a blockchain network using a transaction can help to streamline their operations and improve efficiency.
In conclusion, the market for the system and method for recording device lifecycle transactions as versioned blocks in a blockchain network using a transaction is growing rapidly. This technology offers a secure and transparent way of recording transactions related to devices, which can help to improve efficiency and reduce disputes between parties. As more companies adopt blockchain technology, the demand for this technology is likely to increase, making it an exciting time for the industry.
The Digicert Inc invention works as follows
The method consists of sending, by the plurality of devices management services, a record of a transaction over a transaction connector to the blockchain broker service. Receiving, by the blockchain broker service, is a record of a transaction. The method consists of sending a transaction record to the Blockchain Broker Service via the transaction connector, receiving the record by the Blockchain Broker Service, filtering the information in the record using the transaction filters by the Blockchain broker service and adding the versioned blocks to the network by the Block Chain Broker service.
Background for System and Method for Recording Device Lifecycle Transactions as Versioned Blocks in a Blockchain Network Using a Transaction Connector and Broker Service
Cybersecurity is a major concern in the new field of Operation Technology, which includes IoT devices that are widely used across industries such as automotive, industrial and home automation. Certificate-based enrollment is required for tamper resistant devices throughout the supply chain. Update services need high-assurance cryptographic signatures to ensure secure delivery of updates via the air or network. Device registration and management services require Zero Touch Provisioning. Device registration is currently done manually using web portals, using a digital digest (digest) generated by the user of an endorsement key (X.509) or certificate (X.509) or using a proprietary JSON Web Token from the service provider based on device identifiers. Automating batch processing is done using scripts to scale the operation. A new approach involves the use of private/permissioned blockchain technology for enrolment based on decentralized verification and public key infrastructures (PKIs) to generate cryptographic signatures. Alternative methods using Blockchain technology provide strong protections from data tampering and decentralized control to increase scalability. Public key cryptography and digital signings are also used to protect digital assets and transactions.
These methods are vulnerable because they only deal with the device enrollment case and then must deal secure keys/storage, certificate management and vendor lock-in. Other approaches use group membership-based key pairs to provide a signature-based, secure change of ownership throughout the supply chain. This requires a central broker to be involved in the workflow, outside of the IT and OT domains. “Blockchain-based approaches do not provide non-repudiable identity for devices in communications, nor can they be used to enroll devices with authoritative proofs of identity. They also lack scalability when dealing with large volumes of transactions.
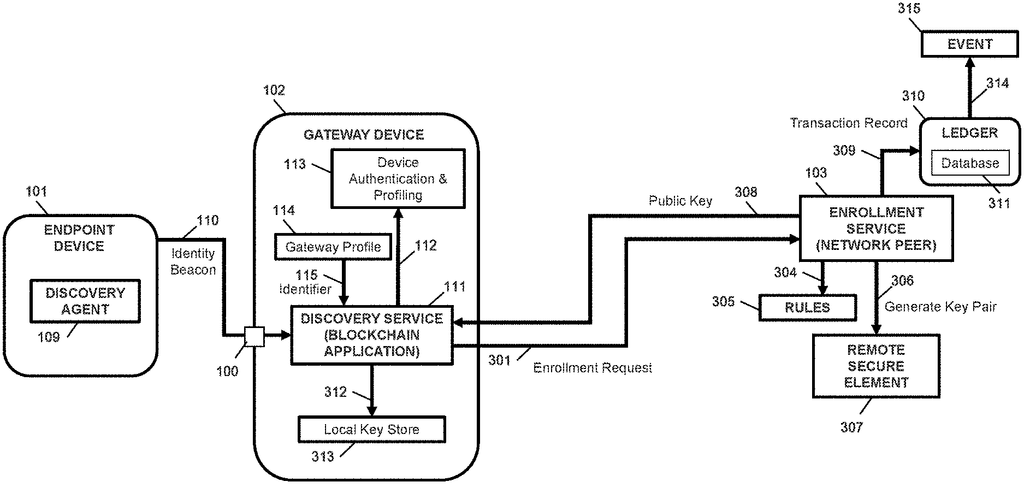
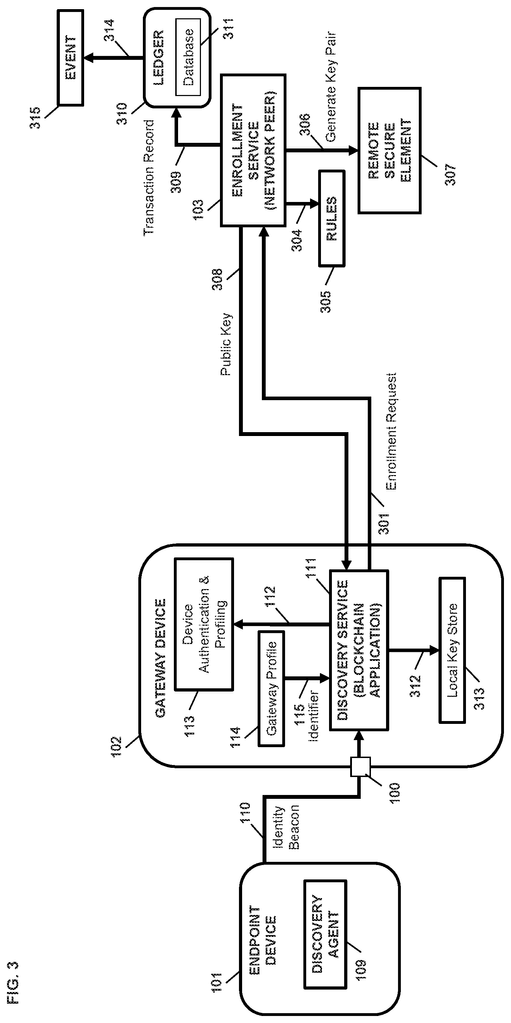
Blockchain Technology provides a decentralized method for data signing, signature verification and scalability based on public-key cryptography, to protect the ownership of digital assets, and transactions. There may not be a non-repudiable identity for devices in communications. The IoT device may not be registered with an authoritative proof of identity. Blockchain applications send transaction requests to the blockchain network. The peer processes the request by using a codechain (smart contract), updates the ledger and emits the block of transactions to integrate between systems.
Current approaches use different methods for device identification, discovery and registration. These methods require either user interaction on headless devices, i.e. devices that do not have an interactive user, or administrative actions in order to pre-register the device before authoritative discovery and identification. These methods include: (a) discovery using a network address (IP), and personalities (e.g. well-known service ports, application protocols specific query inspection). (a) pre-registration for device types to apply enrollment policies;
Other blockchain-based approaches provide for data-at rest protection, data signatures, and signatures between a client-server using a central broker and Representational state transfer (REST), APIs, to sign and validate data hashes. This use of keyless signing without relying upon PKI or certificates, is limited to data integrity message signing. The signature scheme is required to be renewed on a monthly basis.
Alternative approaches based upon a unique digital signature of the device, based on an immutable hardware configuration and algorithm processing requiring at least one user configurable paramater for filler code is not a viable option for headless devices, or scalability over millions of distributed IoT-devices.” The use of a private certificate based on the digital signature of the devices, as well as including the fingerprint in the public certificate issued for the devices, undermines privacy and anonymity and exposes them to hacker and reverse engineering attacks.
The disclosed methods of the disclosed system can, depending on implementation: (a) provide distributed control without requiring a centralized issuer for group and member key management; (b) require no centralized broker in adherence to the blockchain notion of decentralized control and PKI-based strong protection for digital assets, transactions, against data tampering; (c), offer privacy protection with no requirement to include a device fingerprint in the device certificate; (d), provide inferred trust relationships with a user’s device; (e The disclosed methods can, depending upon implementation: (a), provide distributed control with no centralized issuer required for group and member keys management; (b), require no centralized broker to adhere to the blockchain notion decentralized control with PKI based protection for digital assets against data tampering. (c), provide zero-touch provisioning without requiring a user configurable parameter to register a ‘headless device. (d) offer privacy with no requirement to include a ‘device fingerprint’ in the device certificate Endpoint devices require only an immutable device ID that doesn’t require preregistration before discovery and an associated gateway (for non IP endpoint devices) with a secure element either local or remotely to act as the root anchor of trust.
In an exemplary implementation, the disclosed method differentiates between device registration and device enrollment as separate workflows. Device enrollment is the initial assignment of a credential for a device based on the identity proofing by a secure component that acts as the root element of trust. The device enrollment process is necessary to add or join a device into a blockchain and permissioned domain. Device registration is adding an enrolled device to a service (i.e. a step after enrollment) such as a device management, policy, or update service. Device registration is necessary for onboarding devices into managed networks, assigning or transferring device ownership to device management services, and for remote administration, maintenance, and provisioning functions based on policy. As part of a device enrollment request, device enrollment and registration (for certificates-based enrollments) can be included. A device disenrollment may also include both device disenrollment (for certificate-based enrollment) and device deregistration as part of an integrated workflow.
Traditional IT threats models use a multilayer defense mindset that pivots around threat intelligence, grammar and expressions, as well as anomaly detection on the basis of deviations from baseline. IoT demands a paradigm change from detection to prevention, with an emphasis on safety. This requires anticipating risks, preemptive measures and application resilience to exploits.
Data transport over a Local Area Network or Wide Area Network requires an Internet Protocol address (IP), which can be assigned either statically or automatically by a network provider. Old brownfield devices may use point-topoint interfaces or link protocols, such as RS-422 and RS-485 (Highway Addressable Remote Transducer, HART), Modbus (Controller Area Network (CAN), Bus), Aeronautical Radio (ARINC), General-Purpose Input-Output (GPIO), and not have IP protocol stacks for networking.
The disclosed method can offer significant improvements in efficiency and effectiveness to retrofit legacy device for remote management and protection. Devices with non-IP addresses (hereinafter “non-IP” devices) Devices with limited resources (e.g. memory, battery powered etc.) Device management and device enrollment can be performed by discovering point-to-point and other connectivity options that are not available over IP networks. Devices that don’t have an IP address can be linked to a gateway IP device for management and identification. A connected IP gateway device can proxy data transfer between non-IP devices and IP networks (LAN/WAN), including firmware updates or device configuration. Device certificates are used to ensure confidentiality and integrity. Device management services can monitor the dynamic association of non IP devices with connected gateway devices. “Connected endpoints and gateways can participate as blockchain apps to initiate non IP or IP device discovery, associate authenticated transactions in the blockchain with network peers, and generate transaction records for device inventory and management throughout the device’s lifecycle.
The disclosed method can improve process efficiency and provide scalability by (a) automating registration of IP devices and non-IP during certificate-based enrollment, with configured policies services; (b), automating deregistration of IP devices and non IP devices during certificate-based revocation; (c), policy-based dynamic association with a plurality certificate authorities for certificate issue and revocation. Wherein the connector attributes may include the certificate cost and the term; (d) authentication endpoints and connected gateway devices to establish a
Any update of in-field devices that uses commonly used secure transport protocol, such as Transport Layer Security (TLS), or Internet Protocol Security(IPsec), will only ensure the confidentiality of data in transit by validating the sender (server), and optionally the recipient (client), in peer-topeer communications. No verification is made of the supply chain’s integrity. Updates to devices such as firmware, configuration updates and firewall rules. The flow path from the publisher to the distributor, via the provider. This flow path involves multiple store and forward silos. These delivery mechanisms do not provide high assurance packaging that is tamper-resistant across the entire supply chain. The disclosed method is a scalable, automated approach for incorporating supply chain provenance to ensure end-to-end confidentiality and integrity of data based on the use of innovative cryptographic methods and authoritative identity proofing by all entities in distribution chain.
The disclosed method of device identification, enrollment, registration and secure updates can be used for IP and non-IP endpoint devices as well as IP gateway devices. In the industry, endpoint devices are also known as sensors or edge devices, while gateway devices can also be called core devices.
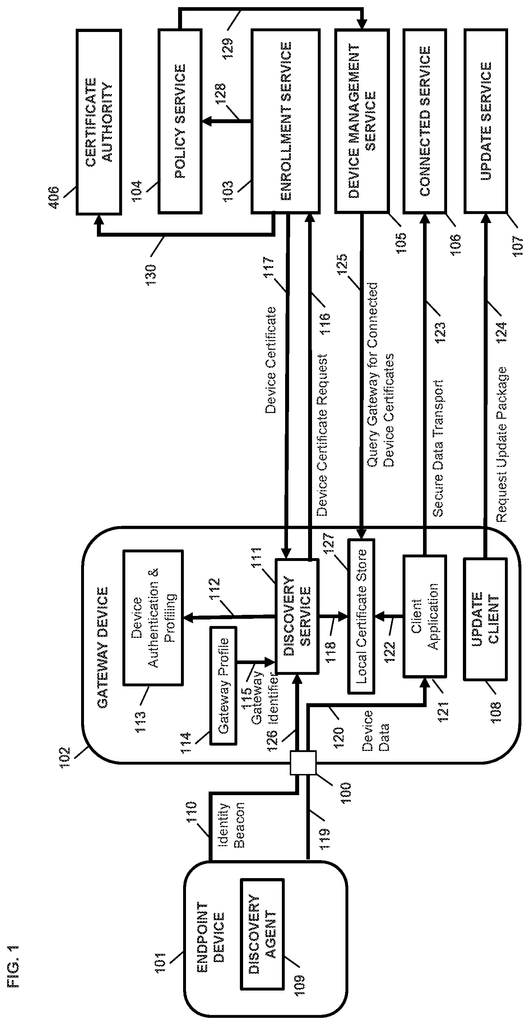
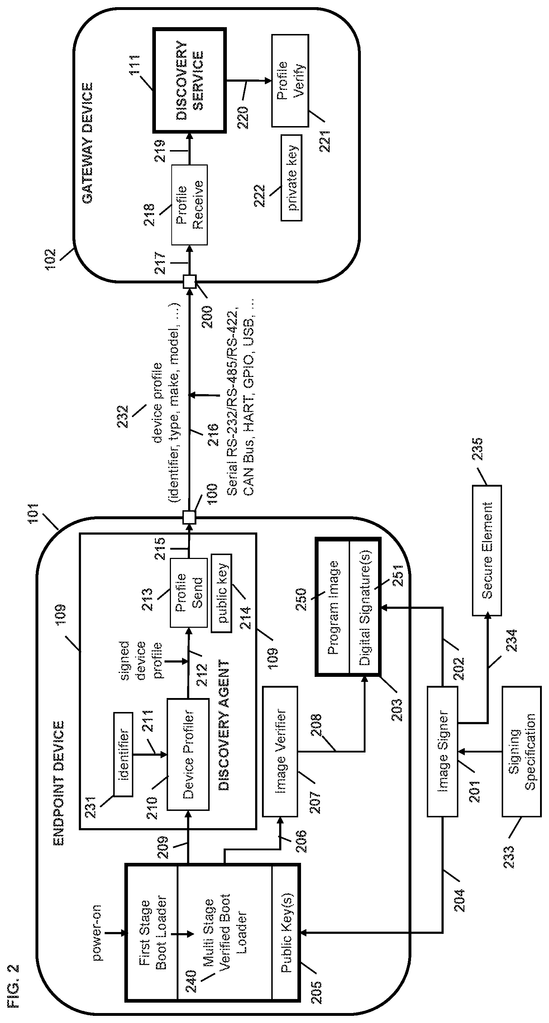
An example embodiment of the current disclosure provides a device identification method for enrolling and registering an endpoint device connected to a Gateway device. The method includes a multistage verified bootloader, a gateway device discovery service, an enrollment service and policy service. The method involves sending an authenticated endpoint device profile with an identity beacon from the discovery agent of the endpoint to the gateway discovery service. The discovery service verifies the authentication of the device and profile. It then generates a certificate request from the privacy certificate authority for the device. The discovery service sends the certificate request to the enrollment service. The method involves the enrollment service translating the received certificate request of the endpoint devices for a certificate authorities and then sending the translated certificate requests to the certificate authorities. The method comprises receiving, by an enrollment service, a certification for the device from the certificate authority, and then processing the certificate received by the service to represent a privacy authority. The enrollment service sends the certificate of the endpoint to the discovery service. It also sends a notification to the policy service about the registration of the endpoint. The method involves sending a directive by the policy service to add the device management service to the endpoint.
An example embodiment of the disclosure provides a deregistration method using an administration dashboard. This is done by using an enrollment service, policy service and device management service. A privileged and authenticated user can initiate the method from the administration dashboard. The enrollment service will then send a command to the certificate authority. The method comprises sending a notification to the policy service by the enrollment service of the revocation of a device certificate. The policy service sends a directive for the device to be removed to the device management services.
An example embodiment of the current disclosure provides a way to enroll endpoint devices using a discovery application on a gateway as a Blockchain application, and an enrollment service within the network as a peer of the blockchain network. The discovery service sends an enrollment request to the network’s enrollment service. The method may include the enrollment service receiving the enrollment request, and authenticating the device. The enrollment service generates a certificate for the endpoint based on orchestration guidelines established for a service network. The enrollment service sends the certificate of the endpoint device by way of the gateway device. The method involves recording, by an updating service, a log of requests for the endpoint devices as a record transaction in the local ledger and distributing blocks to blockchain peers so that a distributed ledger can reproduce device history.
An example embodiment of the disclosure provides a way to update a device registered using a development and release management system operated an update provider. An update service is operated by a publisher. A device update client and a device local secure element are also used. The method comprises building an update package on the development platform, which includes at least one firmware update, software update, configuration update and update script. The method involves signing the update package by the release system using a provider signature key. A first digital signature will be included in the package. The method involves encrypting the signed package by the release system using a public key of a certificate issued to the update publisher. The method involves sending the signed and encoded update package by the release system to the update service. The method involves requesting an update package by the device’s update client. The request may include the device manifest, at least the model number and the vendor identifier for the device, as well as a certificate. The update service prepares, on the basis of the received device manifest, a set signed update packages for a device according to the configured orchestration rule for the device. The method involves reencrypting by the service and resigning by the publisher using the publisher’s private key, signing by using the publisher’s signing key, and then encrypting using the public key for the device from the certificate. The update package includes a second digital signature. The update service sends the double-signed and encrypted update package from the device to the update client. The update client decrypts the encrypted package by using the device’s private key. The update client verifies the first and second signatures by using public keys of the certificate issued by the certificate authority for the update provider. In one embodiment, an update script is run on the device in order to apply the package update to the device.
An example embodiment of the current disclosure provides a way to update a device by using an update client as a Blockchain application on the device, an update server in a network acting as a peer of a Blockchain network, orchestration rules and a ledger. The update client sends a request to the network update service for a package of updates for the device. The update service receives the device request, and authenticates the device. The update service prepares a signed, encrypted update package using orchestration rules for a network network service. The update service sends the signed and encoded update package to device. The method involves recording, by an update service, the request log of the device in the ledger and distributing blocks to blockchain peers for a distributed ledger that reproduces the history of the device.
An exemplary implementation of the present disclosure demonstrates a method for securing data transfer between an endpoint, which does not have an IP, and a Gateway device connected to the endpoint using a Discovery Agent, a Discovery Service, an Enrollment Service, a Policy service, and Device Management service. The discovery agent sends an authenticated device profile and an identity beacon from the endpoint to the gateway. The discovery service verifies the authentication of the endpoint and device profiles. It then generates a certificate request from the privacy certificate authority for the endpoint to the enrollment service. The enrollment service processes the received certificate request to translate it for a certification authority. The method comprises sending a request for a certification for an endpoint device by the enrollment services to the certificate authorities, and receiving a certificate issued by the authority for the device by the enrollment services. The enrollment service processes the certificate received for the device in order to convert the certificate received for the device into a privacy certificate authority. The enrollment service sends the certificate of the endpoint device to the discovery service. The method involves sending a notification to a policy server by the enrollment service of the endpoint registration, and by the policy to a device service an instruction to add the device. The discovery service stores an endpoint device issued certificate in the local certificate store on the gateway device. “The method involves receiving data from/to an endpoint device by an application running on the gateway device and performing cryptographic functions on the data, using the certificate of the endpoint from the local store, to secure data transfer.
Click here to view the patent on Google Patents.