Invented by John A. Nix, Network 1 Technologies Inc, M2M and IoT Technologies LLC
UICCs are small, integrated circuits that are embedded in devices such as smartphones, tablets, and other electronic devices. They are used to store sensitive information such as credit card numbers, passwords, and other personal data. The use of UICCs in two-factor authentication is becoming more prevalent due to their ability to securely store and transmit data.
The market for network that supports two-factor authentication of modules with embedded UICCs is expected to grow at a significant rate over the next few years. This growth is driven by the increasing demand for enhanced security measures in various industries such as banking, healthcare, and government. The rise in cyber-attacks and data breaches has also contributed to the growth of this market.
The adoption of two-factor authentication using UICCs is also being driven by regulatory compliance requirements. Many industries are required to comply with regulations such as the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA). These regulations require the use of enhanced security measures to protect sensitive information and data.
The market for network that supports two-factor authentication of modules with embedded UICCs is also being driven by the increasing use of mobile devices. As more people use smartphones and tablets to access sensitive information and data, the need for enhanced security measures becomes more important. Two-factor authentication using UICCs provides an additional layer of security to protect against unauthorized access.
In conclusion, the market for network that supports two-factor authentication of modules with embedded UICCs is rapidly growing. This technology is becoming increasingly popular due to the need for enhanced security measures in today’s digital age. The adoption of two-factor authentication using UICCs is being driven by regulatory compliance requirements, the rise in cyber-attacks and data breaches, and the increasing use of mobile devices. As the demand for enhanced security measures continues to grow, the market for network that supports two-factor authentication of modules with embedded UICCs is expected to continue to grow at a significant rate.
The Network 1 Technologies Inc, M2M and IoT Technologies LLC invention works as follows
A network that has a number of servers can allow authentication from a module. The module must include an embedded universal integrated circuit chip card (eUICC). A network can send a network module identity, a first and second key K to an eUICC subscription manger. The second key K can also be encrypted using a symmetric key. The module can activate and receive the eUICC profile. The network can then authenticate the module user using a second factor and send the symmetric keys to it. The symmetric key can be used to decrypt the second key K encrypted by the module. The second key K can be used by the network to authenticate the module.
Background for Network that supports two-factor authentication of modules with embedded universally integrated circuit cards
Technical Field
The present methods, systems, and in particular, methods, systems, and protocols for a network that uses an embedded universal integrated card card (eUICC), are communications. The methods, systems, and protocols also support authentication of a user associated to the eUICC.
Description of Related Art.
The combination of machine-to-machine communications and low-cost sensors, Internet connections, and processors. M2M communications, as well as low-cost sensors, Internet connections and processors, is a promising area. M2M technology has many benefits. It allows remote monitoring and/or control for people, assets, or locations where manual monitoring isn’t economically feasible. Also, automated monitoring can reduce costs. Examples of M2M technologies include remote sensors, alarm systems and automobiles. Tracking devices for shipping containers and pallets, as well as health applications like remote monitoring of someone’s heartbeat or glucose levels, monitoring of field equipment, and security systems are some of the fastest-growing M2M markets. M2M applications can use either wireless or wired Internet connections. Both types of connections are growing rapidly. M2M applications can also be called “the Internet of things?
M2M communications allow remote control of actuators that are connected to M2M devices, such as turning on or off power switches, locking or unlocking doors, changing the speed of motors, and similar remote controls. An M2M device may use one or more sensor measurements to adjust or change an actuator. A M2M device can also be called a “wireless module”. Or simply a module. One example is that a room or building becomes too cold. An M2M device can report the temperature to a central server and instruct the M2M to activate heat or adjust a thermostat. The number of M2M communications that are economically viable is increasing as the cost of computer and networking hardware continues to drop.
Wireless networking technology can be used by many M2M applications. Wireless technologies, including wireless wide area networks and wireless local area networks, have seen rapid growth over the past 15-years. This is expected to continue. WiMax is a wireless local area network (LAN), which includes WiFi and 3GPP’s 3G Universal Mobile Telecommunications System (3G) and 4G Long-term Evolution (4G) LTE Advanced. The Institute of Electrical and Electronics Engineers (IEEE) 802.16 standard are both wireless LAN technologies. Wireless technologies combined with M2M communications offer new possibilities for M2M modules to be deployed in areas that are not suitable for fixed-wire Internet access. However, this also presents new problems that must be addressed.
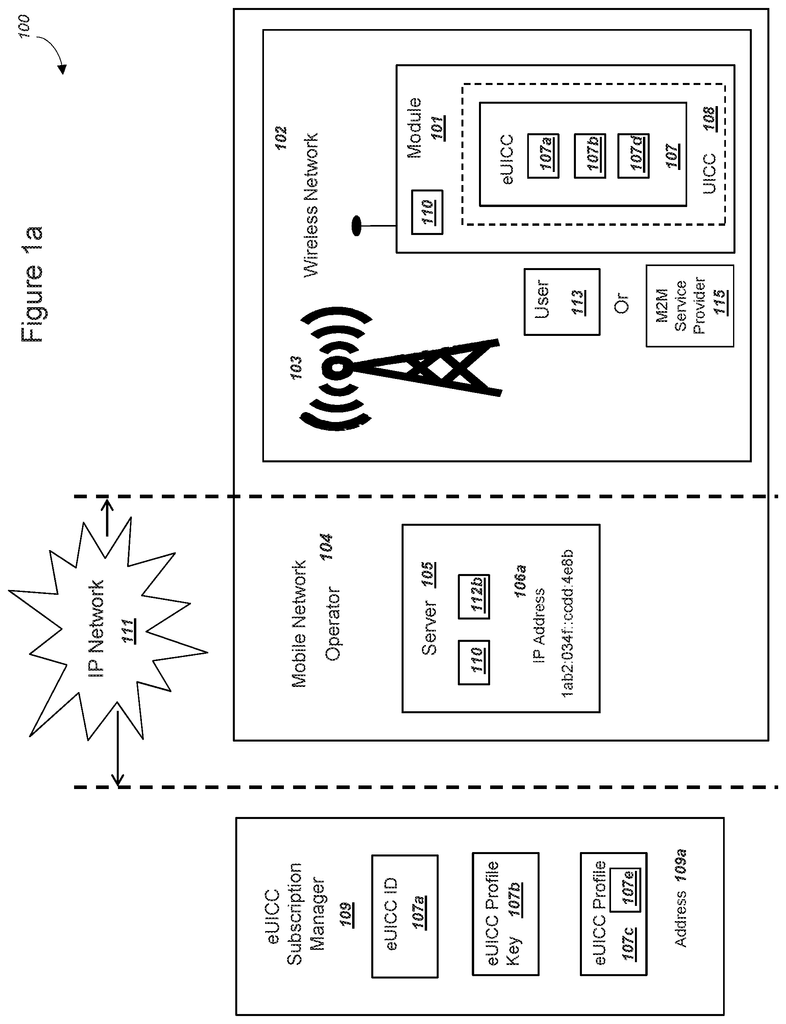
One class of problems when using M2M modules in traditional wireless networks is due to basic design considerations for wireless networks. Many wireless wide-area networking standards have been optimized for smart phones and mobile phones. The use of a subscriber identification module (SIM), within 2G networks, and a related universal embedded circuit card (UICC), for 3G and 4-G networks, as well as LTE networks has been a core component of traditional wireless technologies like 3GPP or ETSI. ETSI standards for physical UICCs include ETSI TR102 216. These cards were traditionally supplied by mobile network operators (MNOs) and include a pre-shared key K as well as a set parameters that allow a user equipment or mobile phone to connect to the MNO’s wireless network. These parameters can include an IMSI (identity), (iii), a list of frequencies that a mobile phone scans to locate a beacon signal from MNO, (iii), a preferred access listing of MNOs to allow roaming in areas where the MNI associated to the IMSI is unavailable, and (iv). many other related parameters. A UICC is a physical media card that can be used to replace or?swap-out a mobile phone’s SIM card. The physical card can be replaced or?swap out when the mobile phone’s location changes or if the subscriber has other preferences. Mobile handset distributors and mobile phone service providers can also physically insert or modify the appropriate UICC for mobile phones.
But, the rapid growth of?machine to machine?? Applications have created major challenges to the traditional method of using physical media like a UICC to transmit data and parameters to a MNO. There are several reasons why physical media, such as UICCs, may pose problems in M2M applications.
There are also other requirements for changing network credentials or preferred networks without having to physically change a UICC. This is one reason that the industry, ETSI, and 3GPP standard bodies, have considered an embedded UICC (also known as an “eUICC”). An eUICC allows the operation of an UICC to be essentially?virtualized?. This means that data and algorithms can be processed in software, and then distributed electronically (e.g., file transfer, file download). ETSI TS 103 3383 v12.1 outlines the technical benefits and considerations of using an eUICC for M2M applications. It is herein incorporated in its entirety. This published standard was first published in June 2013. It is primarily in the requirements phase. Many of the technical specifications required for the implementation and operation an eUICC are being defined in the future.
Although embedded eUICCs can help solve many issues related to managing and distributing physical media, such as a UICC or IMSI, there are still many challenges. There are many challenges that a eUICC still needs to overcome. These include the ability to electronically and securely transfer a new set MNO network access credentials (such an IMSI or network key K) from a module in a safe and efficient way. It is necessary for a module in order to securely obtain network access credentials. The art requires that the credentials obtained in an eUICC be compatible with the large installed and legacy network base K. This key K is used to authenticate and cipher data for a user device or mobile phone. An eUICC, which can be a successful solution to M2M application needs, could also work to solve the problems for regular mobile phones. For example, a smartphone or consumer phone could use an eUICC to avoid the complexity and costs of having to deal with a physical UICC.
There is a need in the art to share a pre-shared key K with a module operator without relying on physical distribution or electronic distribution through third parties. This includes encrypted forms. The art requires the encryption of data in an eUICC profile be controlled by the mobile operator. This is because the mobile operator may not have control over the release or distribution of profiles from an eUICC subscriber to a module with an eUICC. A pre-shared key K and network access credentials, as per eUICC standards discussed above in November 2013, are transmitted from an eUICC subscribe manager to a module. Pre-shared secret keys K are also known as key K and key Ki in 3G networks. The security of the electronically transferred pre-shared key K is not stronger than (i), the encryption used to transfer key K and (ii), the security and chain control for keys used in encrypting the communication channel that transfers key K to a cell phone or module. The communications channel used to transfer key K to a module or mobile network operator (MNO), is what makes the security of key K depend on. This is true even if the MNO is not able to control the channel. The MNO must be able to control and secure the electronic transfer of key K within an eUICC profile. However, copying and distribution of the profile is not under its control.
An additional reason a mobile operator might prefer that the key K be rotated or changed for each module or mobile phone over a longer period of time, such as many years, is to improve security. A single key K can be used for communications with any module or mobile phone for an extended period of time. This is especially true if there are large amounts of data that could be exposed to potential attackers for analysis. Side channel attacks on security keys have been published in recent publications. However, it is possible to rotate the key periodically. Conventional technology for UICCs and eUICCs doesn’t support this. In the future, the standard key length for K could increase from the current 128 bits, to an exemplary 256 bit. The only way to modify key K for a mobile phone or module using conventional technology, where key K is stored in physical media like a UICC card is to physically distribute a UICC card. This can lead to increased costs and business complexity. There is a need in the art to allow a module (including a mobile phone) and a MNO secure and efficiently to support a change of network access credentials. This includes a key for the module connecting with the MNO.
And there are other requirements in the art, as the above list is not meant as an exhaustive but rather to be illustrative.
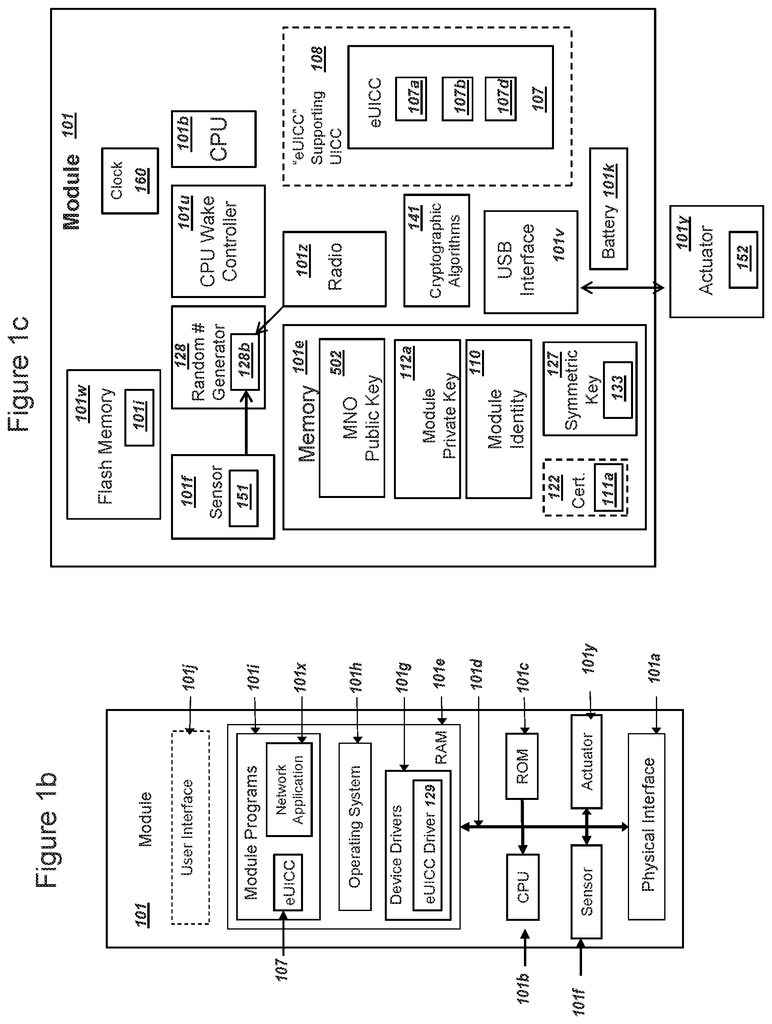
Methods, systems and protocols are available for secure and efficient communication using a modular to communicate with a server or a mobile operator network. The module supports?Machine-to-Machine? communications. The module can support?Machine to Machine? communications, also known under the name?the Internet of things’. These methods and systems can also be used to support other applications, such as mobile phones that connect to a wireless network. The wireless network can be associated or the radio access portion a mobile network operator. The present invention may include a mobile phone, such as a smartphone. It can also be called a mobile station, user equipment, or mobile device. The invention addresses the above-mentioned challenges in securing the deployment modules that can use an embedded universal integrated card card (eUICC), and/or PKI algorithms, keys.
The methods and systems described herein can be used to reduce the need to manually alter a module’s network access credentials. This allows the module to use new or different keys to authenticate and connect to a wireless network. An eUICC is a secure encryption or derivation of the key K that can be used to authenticate a user. This can increase the module’s usefulness and value for both the user and the mobile operator network. An eUICC may also include software and/or firmware components that can be?virtualized? The operation of a physical UICC in such a way that (i) data normally stored in a physical UICC are recorded in a file with encrypted encryption and (ii), the steps for using the file can all be done by an eUICC.
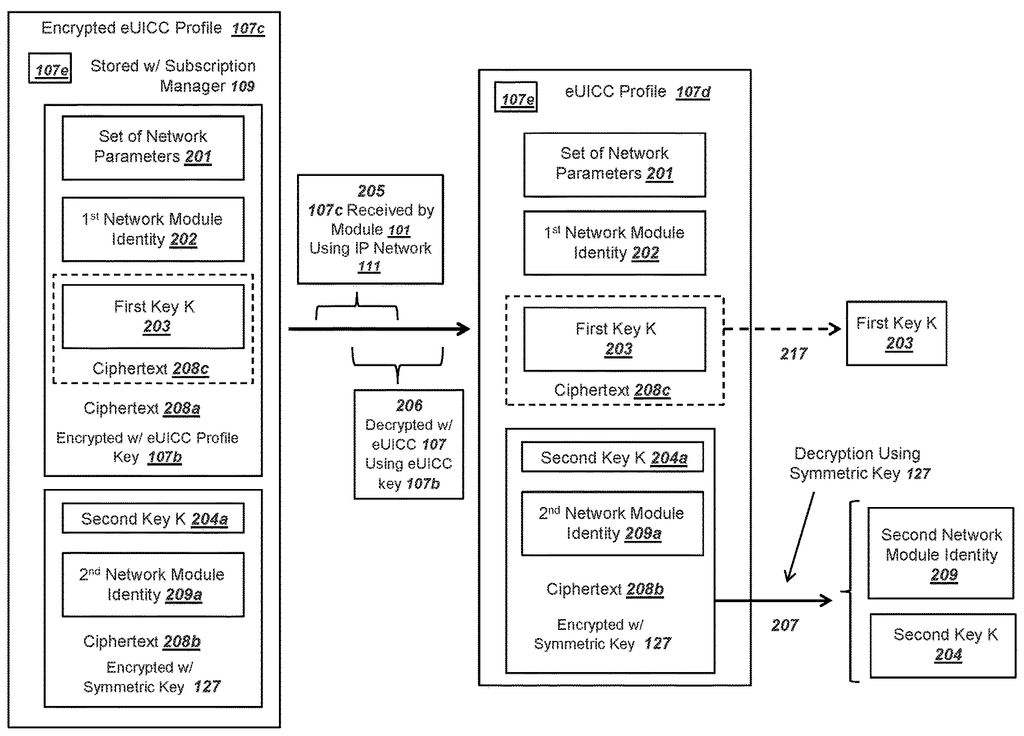
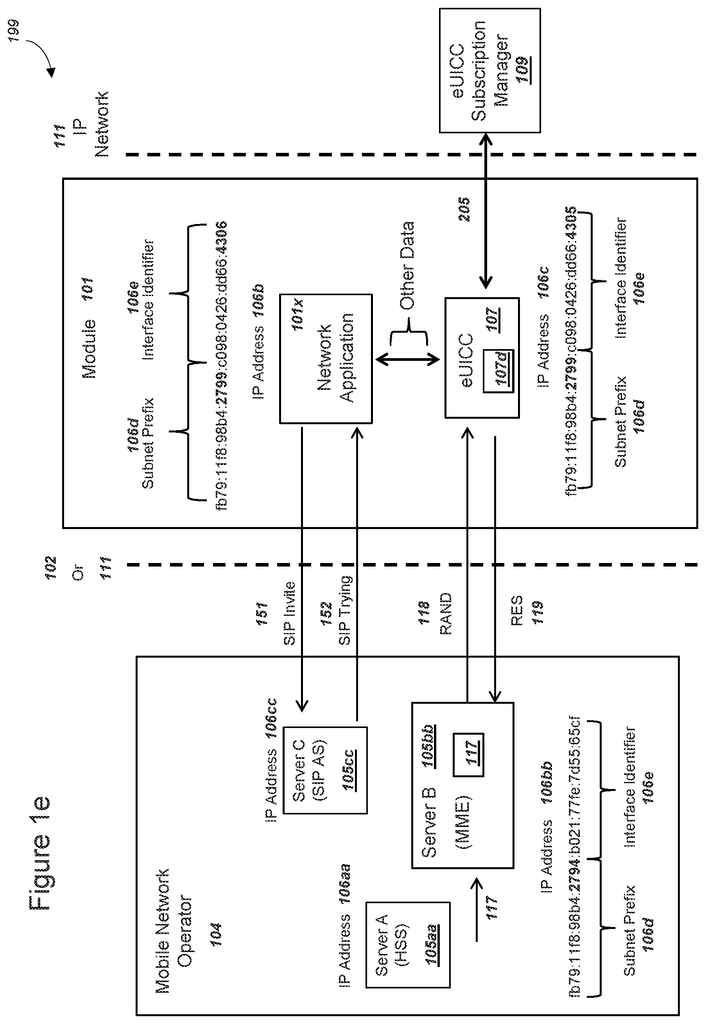
In a first embodiment, a network operator can process a list of data to be included in a profile for an eUICC. The profile data can be identical or similar to data in a physical UICC. This includes a set network parameters and a first keyK. A mobile operator can then send the data to an eUICC subscriber manager. An embedded universal integrated circuit chip card (eUICC) can be included in a module. An operating system can process the eUICC and store it in a nonvolatile storage. This ensures that the eUICC remains available even after the module has been powered down. An eUICC identity and profile key can be included in the eUICC eUICC eUICC eUICC eUICC eUICC eUICC eUICC ciphering algorithm. Before a user receives the module, a distributor or manufacturer could record the data. The module can communicate with a network app using the eUICC. The module has a radio and can connect to the network operator via a wireless network. The module can connect to a first network and send an eUICC identification and receive an encrypted profile. Additionally, the module can store the encrypted profile in a memory that is not volatile. The first network may be different from the wireless network used to create the profile. It could include a WiFi network, an LAN connection using a USB interface, or a public mobile network.
Continuing with the first embodiment, the module may receive an encrypted profile that includes a portion of the ciphertext as well as a second portion. The module can use the eUICC profile keys and the symmetric ciphering algorithm to decrypt the first part of ciphertext. The resulting plaintext can be decrypted using the eUICC profile key and the symmetric ciphering algorithm. A first authentication can be conducted by the mobile operator using the first module identity and first key K. In addition, the network operator can receive an attach message that includes an exemplary radio resource request message. The network can also send a random number as a first RAND value.
The module can transmit the RAND to the activated profile, continuing with the first embodiment. The eUICC has the ability to input the first RAND, the first key K and a cryptographic algorithm into a cryptographic algorithm to generate a response RES value. The eUICC could return the RES value back to the module and the module could forward it to the wireless network. The wireless network can compare the received and expected RESs (previously calculated using same first RAND key K) and if they match, the profile and module can be authenticated. Module and network can take additional steps to ensure that the module has at most limited access to an Internet network. A user can authenticate with the module by having access to the IP network. However, the mobile operator might not be able to control the distribution of the profile.
The first embodiment can be continued. A mobile network operator can verify or authenticate a user or M2M provider associated with the module. An authentication or verification process could include the user entering information on a web page using the IP connection established with network in paragraph above using first key K. Or, the user could call a call center and confirm identification information. The MNO could also authenticate or verify the identity a user associated to the module by visually inspecting the physical identification of the user, such as a driver’s license or passport. The MNO could then exchange data with an M2M provider to verify that the module has been authenticated with the first key K. The MNO could then authenticate the module with a second factor if the user or M2M service provider is involved. Authentication with the first factor required receiving the RES. The MNO can verify the identity of an entity associated to the module after successful authentication with the 2nd factor. However, this identity might not be known prior to the authentication with the 2nd factor because the distribution of the eUICC profile could be out of the control of the mobile operator.
The second embodiment can be continued by the mobile operator, who, after securing the second factor, can send the module a symmetric keys. A key ciphering algorithm can be used to encrypt the symmetric key. Or, the symmetric keys can be encrypted with a key ciphering algorithm. The module can decrypt the second part of ciphertext by using the symmetric encryption algorithm and the received key symmetric. The profile cannot be decrypted without the symmetric keys. Therefore, the mobile operator can keep control of the use of K in the profile. For example, the symmetric key will not be released until a user has completed authentication with the operator.
After decrypting the second part of ciphertext the module with eUICC is able to read a plaintext second module identity and second key, K. This can be stored in a protected, volatile memory. The module can be disconnected from the wireless network where the first session used the initial key K. It can then reconnect using the second module’s second network module ID and second key K. This includes sending the second network identity to the module, receiving a second RAND value and calculating a second RES using the second RAND, the second and second keys K and sending the second RES values. The module can then access the IP network and public Internet via the wireless network after the second authentication succeeds. Subsequent authentications can use the second network identity and the second K. In the case of a module that is a mobile phone, the user can be associated to a phone number and/or place/receive telephone calls following the second authentication.
Click here to view the patent on Google Patents.