Invented by Taylor Ettema, Huagang Xie, Palo Alto Networks Inc
Dynamic selection and generation of a virtual clone is a technique that allows for the creation of a virtual environment that mimics the real network. This virtual clone can be used to test and detonate suspicious content without risking damage to the actual network. By using a virtual clone, businesses and organizations can quickly and safely identify and neutralize potential threats.
The market for this technology is driven by the increasing sophistication of cyber attacks. Malicious actors are constantly developing new techniques and tools to evade detection and infiltrate networks. As a result, businesses and organizations are looking for more advanced and effective ways to protect themselves. The use of honey networks and virtual clones is becoming a popular solution.
Another factor driving the market is the increasing availability of cloud-based solutions. Cloud-based platforms offer a scalable and cost-effective way to deploy and manage honey networks and virtual clones. This makes the technology accessible to businesses of all sizes, from small startups to large enterprises.
The market for dynamic selection and generation of a virtual clone for detonation of suspicious content within a honey network is expected to continue to grow in the coming years. As cyber threats become more sophisticated and pervasive, businesses and organizations will increasingly turn to advanced technologies like honey networks and virtual clones to protect themselves. The availability of cloud-based solutions will also drive growth, making the technology more accessible and affordable for businesses of all sizes. Overall, the future looks bright for this rapidly evolving industry.
The Palo Alto Networks Inc invention works as follows
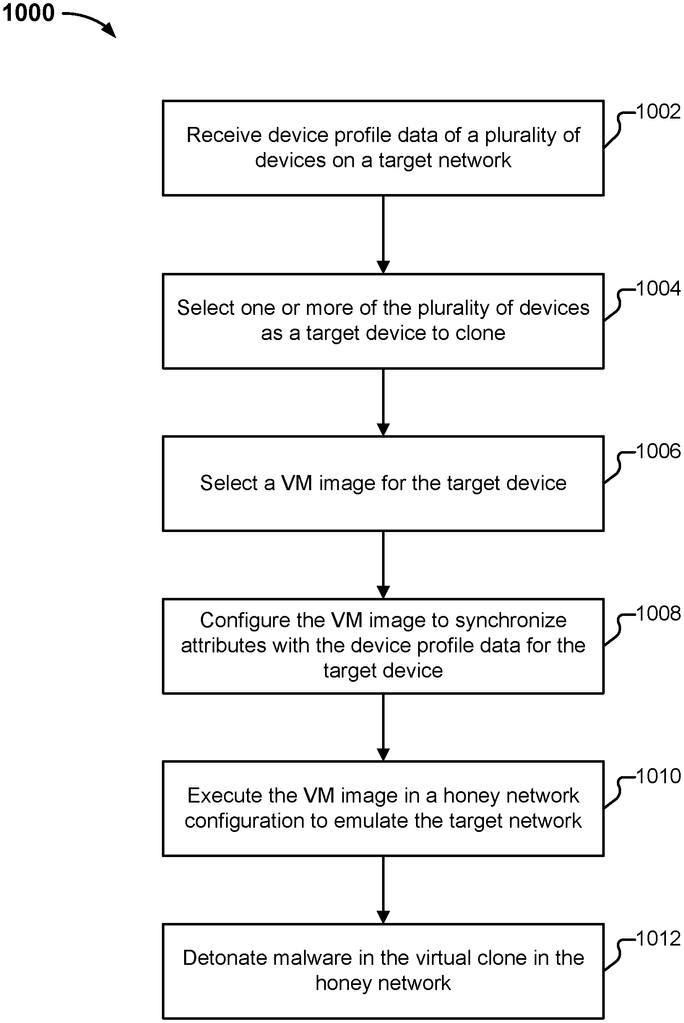
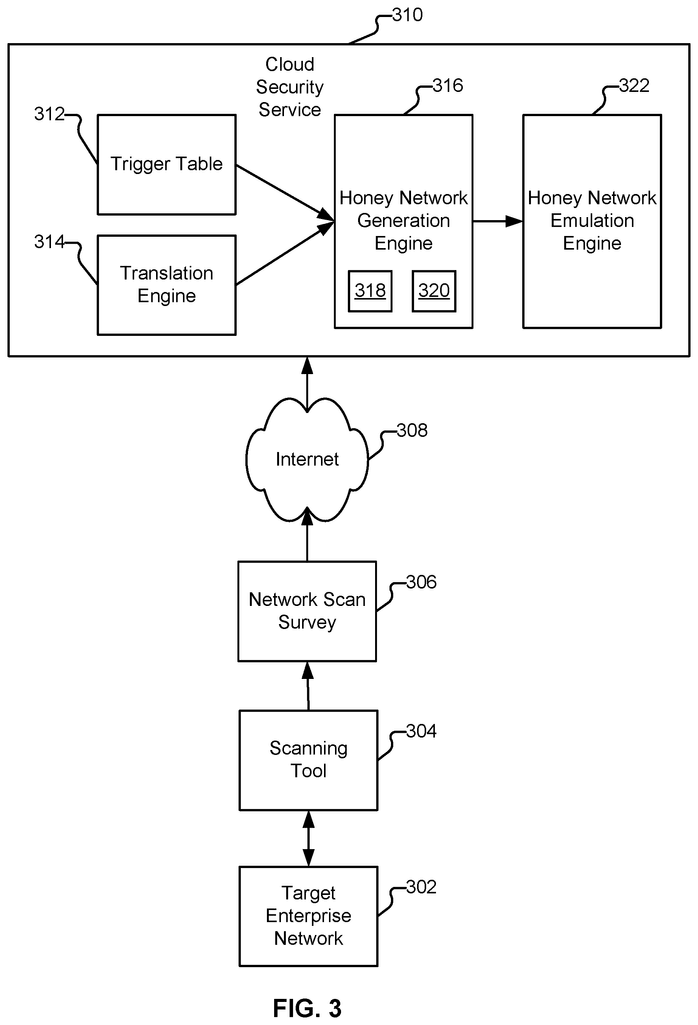
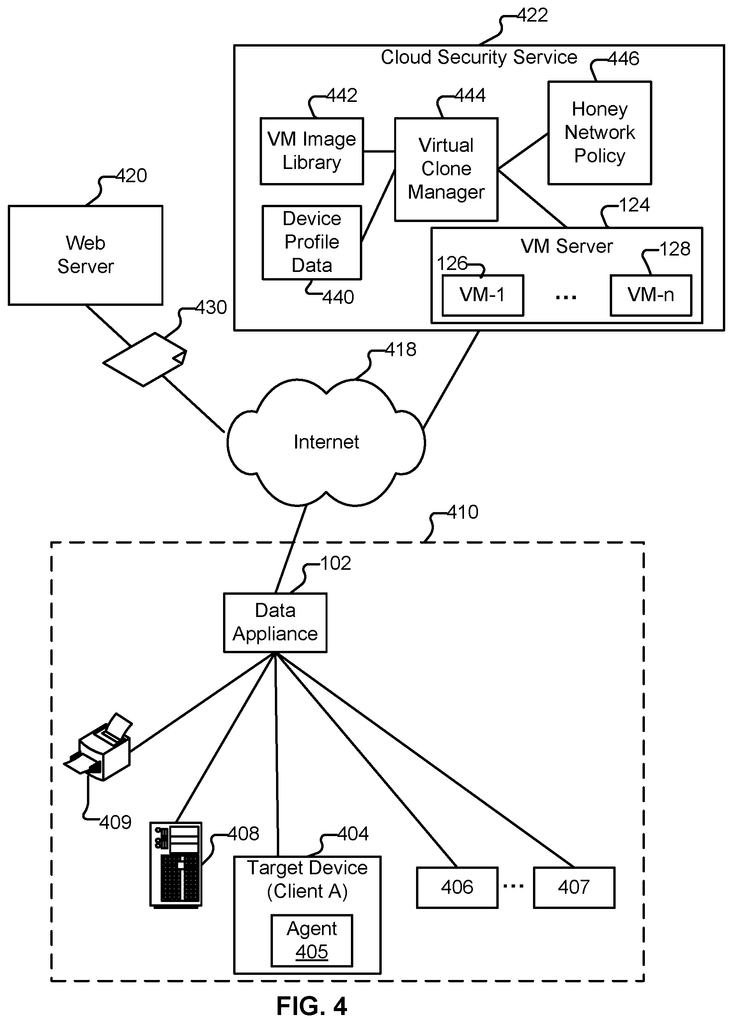
The disclosure includes techniques for dynamic selection of and generation of the detonation locations of suspicious content using a honey network. A system for dynamic selection of and generation of detonation locations of suspicious content using a honey-network includes a virtual machine instance manager, which manages a number of virtual clones that are executed in an instrumented VM, where the number of virtual clones corresponds to the honey network, which emulates a variety of devices on an enterprise network, and an intelligent malware detector, that detonates a sample of malware in at least one virtual clone executed in the instrumentaled
Background for Dynamic Selection and Generation of a Virtual Clone for Detonation Of Suspicious Content Within A Honey Network
A firewall protects networks against unauthorized access, while allowing
Authorized communications pass through the firewall. A firewall can be a single device, a group of devices or software that is installed on a computer or other device. It provides firewall functionality for network access. Firewalls can, for example, be integrated into the operating systems of devices, such as computers, smart phones or other types network-capable devices. Firewalls may also be installed as software in computer servers, gateways or network/routing appliances (e.g. network routers) or data appliances. Firewalls usually deny or allow network transmission based upon a set rules. These rules are sometimes referred to by the term policies. A firewall, for example, can filter traffic inbound by applying a series of rules or policy. A firewall can filter outbound traffic using a set or rules. “Firewalls are also capable of performing basic route functions.
Various techniques for synchronizing honey network configurations to reflect target network environments are disclosed. In certain embodiments, the system synchronizes a honey-network configuration to reflect a network environment target.
The invention may be implemented in many ways. It can be used as an apparatus, a process, a system, a composition, a product of computer programming, and/or a CPU, such as one that executes instructions stored on or provided by a memory connected to the processor. These implementations and any other form of the invention can be called techniques in this specification. The invention allows for the possibility of altering the order of steps in disclosed processes. A component, such as a processor and a memory, described as being capable of performing a task can be implemented either as a general component that is temporarily set up to perform the task at a particular time or as a specific component that was manufactured to do the task. The term “processor” is used herein. The term “processor” refers to any one or more devices, circuits and/or processing cores that are designed to process data such as computer program instruction.
Below is a detailed description of some embodiments of the invention, along with accompanying figures that illustrate its principles. Although the invention is described with these embodiments in mind, it is not limited to them. The claims limit the scope of the invention, and the invention includes many alternatives, modifications, and equivalents. The following description provides a detailed understanding of the invention. These details are given for example purposes only. The invention can be used according to the claims without any or all of these details. To be clear, the technical material related to the invention that is well-known has not been described in detail. This is done in order not to obscure the invention.
Advanced Firewalls of the Next Generation
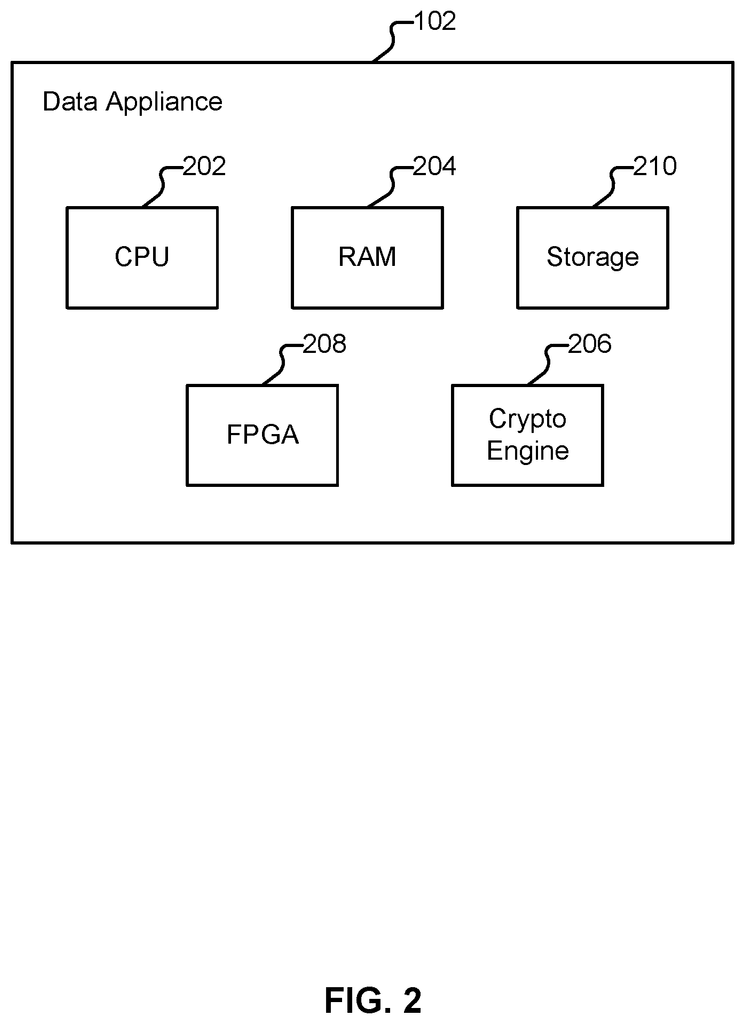
A firewall protects networks against unauthorized access, while allowing authorized communications to pass through it. A firewall can be a device, a group of devices or software that allows network access. A firewall can be integrated with operating systems, such as computers, smart phones or other network communication-capable devices. A firewall can also integrate into or be executed as software applications on different types of devices or security device, including computer servers, gateways and network/routing devices (e.g. network routers) or data appliances (e.g. security appliances or other special purpose devices). In some cases, special purpose hardware can be used to execute certain operations, such an ASIC or FPGA.
Firewalls are designed to deny or allow network transmission based upon a set rules. These rules are commonly referred to as policies (e.g. network policies or network security policy). A firewall, for example, can filter outbound traffic by applying a series of rules or policies that prevents unwanted traffic from reaching protected devices. Firewalls can also filter outbound traffic using a set or policies. These policies can include allow, block or monitor, notify, log and/or any other actions. Similar to a firewall, a firewall can filter intranet traffic and local network traffic using a similar set of rules.
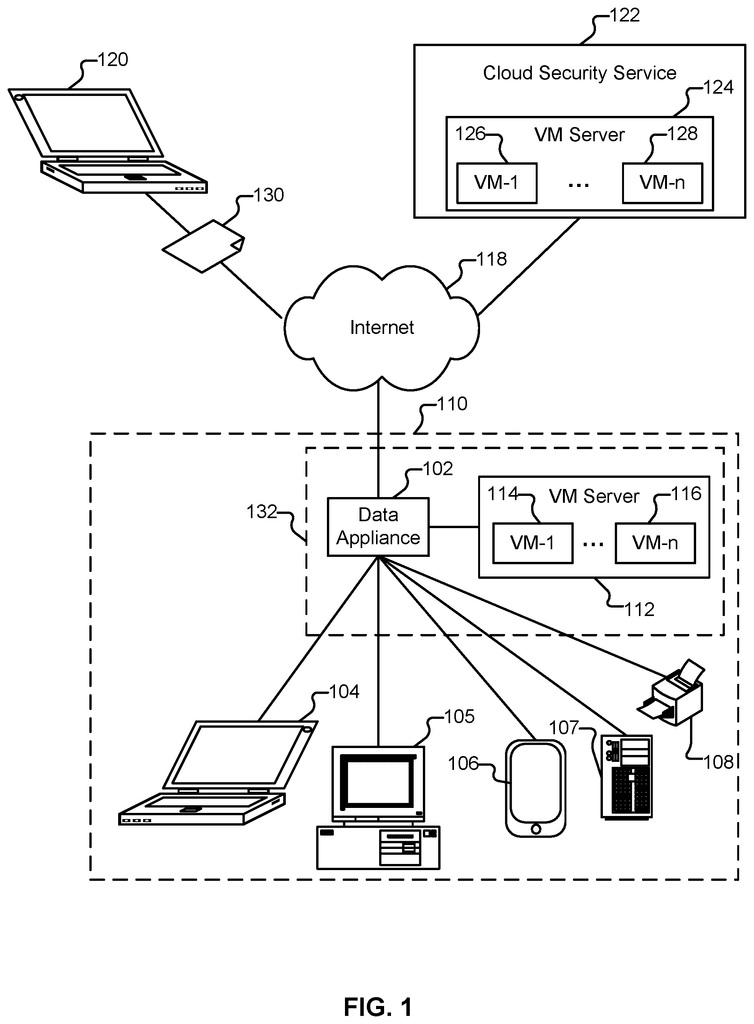
Security devices (e.g., security appliances, security gateways, security services, and/or other security devices) can perform various security operations (e.g., firewall, anti-malware, intrusion prevention/detection, proxy, and/or other security functions), networking functions (e.g., routing, Quality of Service (QoS), workload balancing of network related resources, and/or other networking functions), and/or other security and/or networking related operations. Routing can be done based on information such as IP address, port, destination, and protocol information.
A basic packet filtering firewall inspects network communication traffic and inspects individual packets. (e.g. packet filtering firewalls or first generation firewalls which are stateless packet filtering shields) Stateless packet filtering firewalls inspect individual packets and then apply rules based upon the packets.
Application firewalls can also perform layer filtering (e.g. using second-generation firewalls or application layer filtering firewalls that work at the application level of TCP/IP stack). Application firewalls and application layer filtering firewalls are generally able to identify certain protocols and applications (e.g. web browsing with HyperText Transfer Protocol, a Domain Name System request, a File Transfer Protocol file transfer (FTP), as well as various other types and protocols such Telnet, DHCP TCP, UDP and TFTP (GSS). Application firewalls can block unapproved protocols trying to communicate over a standard ports (e.g., an out-of-police protocol trying to get through by using a nonstandard port can be identified with application firewalls).
Stateful firewalls also have the ability to perform stateful packet inspection. This means that each packet is examined in the context of all packets related to that network transmission’s packet flow/packet flow. (e.g. stateful firewalls, third-generation firewalls). This firewall technique is commonly referred to as stateful packet inspection. It keeps records of all connections that pass through it and can determine whether a packet represents a new connection, part of an existing connection, invalid packet, or the start of a new one. The state of a connection, for example, can be used to trigger a policy rule.
Advanced firewalls, or the next-generation firewalls, can perform stateless and stateful application layer filtering and packet filtering. The next generation firewalls are capable of performing additional firewall techniques. Some firewalls, sometimes called advanced or next-generation firewalls, can identify content and users. Certain next-generation firewalls have the ability to automatically identify thousands of applications. Palo Alto Networks, Inc. sells examples of next-generation firewalls. (e.g., Palo Alto Networks’ PA Series firewalls).
Palo Alto Networks next-generation firewalls allow enterprises to control and identify applications, users, content, and IP addresses. They use a variety of identification technologies such as App-ID, User-ID, Content-ID, and File-ID. This allows for the real-time scanning of content and controls web surfing, data limits, and file transfer limitations. Instead of using traditional port-blocking firewalls, these identification technologies enable enterprises to secure allow application usage by using business-relevant concepts. Special purpose hardware, such as dedicated appliances, can provide better performance for application inspection than software that runs on general-purpose hardware. This is a good example of the special purpose hardware used for next generation firewalls.
Dynamic Analysis for Advanced Threats.
Security detection techniques face a significant challenge in identifying threats (e.g. malware), which is malicious programs that attempt to do malicious or unintended actions. A new zero-day threat or advanced threat such as an Advanced Persistent Threat is one example. This refers to programs that attempt to perform malicious or undesired actions. They often use external command and control (C&C), which monitors and extracts data from specific targets. Sometimes, these sophisticated adversaries also employ stealthy, persistent methods that can be evaded traditional security measures such as signature-based Malware detection measures.
In particular, modern attackers are using new and targeted variants of malware to avoid detection from traditional security solutions. Advanced security threats, such as advanced cyber-attacks, are using stealthy, persistent techniques to bypass traditional security measures. Modern security teams must reevaluate their assumptions that traditional antivirus and intrusion prevention systems are capable of defeating advanced security threats such as APTs.
To address this problem, we need to develop new and better techniques that can efficiently and effectively identify these advanced threats. Executing suspect files, e.g. malware samples, in a virtual environment (e.g. an instrumented virtual environments, also known as using a Sandbox Analysis of Malware Samples) and watching their behavior can help to quickly and accurately identify such malware, even if it hasn’t been previously detected and analyzed.
Once a file has been deemed malicious (e.g. a malware sample has been deemed to have been malware), protections can automatically be generated using, for instance, a cloud security system (e.g. implementing a dynamic security assessment of malware samples in an scalable cloud-based virtual environment to observe the behavior and exploits of potentially malicious software) and delivered to subscribers to the cloud security services (e.g. within minutes to hours of detection). These techniques can be used to foresee who/what was attacked, the application used in delivery, and any Uniform Resource Locator Addresses (URLs). The protections can then be automatically generated using a cloud security service. The cloud security service can identify unknown malware and exploits and execute them in a cloud-based, virtual environment. This is also known as an instrumented virtual environment, which Palo Alto Networks, Inc. provides. It allows for dynamic analysis to identify unknown threats and blocks them. One embodiment of the cloud security service creates and distributes protections in real-time to assist security teams with the challenges presented by advanced security threats. The cloud security service can extend the next-generation firewall platform to classify all traffic across multiple applications. In this example, it can perform a behavioral analysis without regard to ports or encryption. It also has full visibility into web traffic and email protocols (SMTP. IMAP. POP), FTP. SMB and/or other protocols. This allows for detection and dissemination of protections in close real-time to deal with advanced security threats.
However, skilled attackers can detect existing techniques for using an orchestrated virtual machine (VM), environment. This is because they may be able determine whether the malware is executing on the target host or target network environment. Existing sandbox methods for malware detection usually only install one version (e.g. applications or any other software) per instance of virtual machine. Another example is that some existing methods execute multiple virtual machines (VM) instances with different software settings (e.g. multiple VM instances can run simultaneously or sequentially in a VM environment). However, these approaches do not sync various attributes between a target host (or VM instances) and their respective software configurations. These approaches also fail to emulate other devices within the VM environment (e.g., a target host’s network printer, a file sharing/server, a DNS, email, proxy server, other clients, and/or devices in target network environment).
Even though VM environments are currently implemented to provide malware detection and security analysis, they typically analyze discrete events such as downloading of malware?a malware sample, and any subsequent activity in a stand alone sandbox. This is where a standalone sandbox is usually executing one or two VM instances using fixed configurations. These can be implemented using a cloud solution or appliance-based solution. Existing approaches, for example, only try to simulate a single host. Although they may allow access to the Internet, they do not allow local network communication in the target network. These approaches are limited in their ability to analyze the environment and allow for a short execution time, typically between 1 and 5 minutes using the VM instance. APT attacks, for example, are typically performed over a longer time by a skilled attacker. This attacker would usually be attempting a targeted attack (e.g. directing malware or communications to a target host). Such an attacker would often be able detect that the VM instance doesn’t have the expected attributes and/or previously observed attributes of the target host. Another example is that an attacker trying an APT attack targets a host within a target network. He/she expects to see other devices within the network environment that are in communication with the target hosts (e.g. logs and/or local configuration information on the target host, and/or network scans of devices in the target environment using Nmap and other network scanning tools).
Click here to view the patent on Google Patents.