Invented by Subhedar; Sachin, Elbaz; Roger Michael, Htay; Aung, Ciena Corporation
**Revolutionizing Cybersecurity: Systems and Methods for Tracking, Predicting, and Mitigating Advanced Persistent Threat (APT) Attacks Using Virtual Currency Transaction Analysis**
**Introduction**
In the ever-evolving world of cybersecurity, Advanced Persistent Threats (APTs) have emerged as the most sophisticated and damaging forms of cyberattacks. Their stealth, persistence, and use of multi-vector tactics make them notoriously challenging to detect and mitigate before damage is done. What makes modern APTs especially insidious is their blending of tactics—leveraging vulnerabilities, taking advantage of human error, manipulating the media landscape, and increasingly, exploiting virtual currencies for anonymous transactions.
A recently patented system and method offers a transformative approach to cybersecurity: instead of waiting for signs of compromise, networks can now proactively *track*, *predict*, and *mitigate* APTs by harnessing datasets that include virtual currency transactions, network traffic patterns, and even social sentiment analysis. By tying together these diverse data streams, this invention marks a significant leap forward—empowering organizations to act *before* an APT manifests, and in some cases, eliminate the threat entirely.
In this blog, we will distill and expand upon this invention, illustrate its real-world applications, and analyze the enormous market potential it addresses. Whether you are a cybersecurity professional, executive, investor, or technologist, understanding how this technology works and the implications for your organization is critical.
—
**Restatement and Summary of the Invention**
At its core, the patented system offers a multi-pronged, proactive defense for networks against APT attacks:
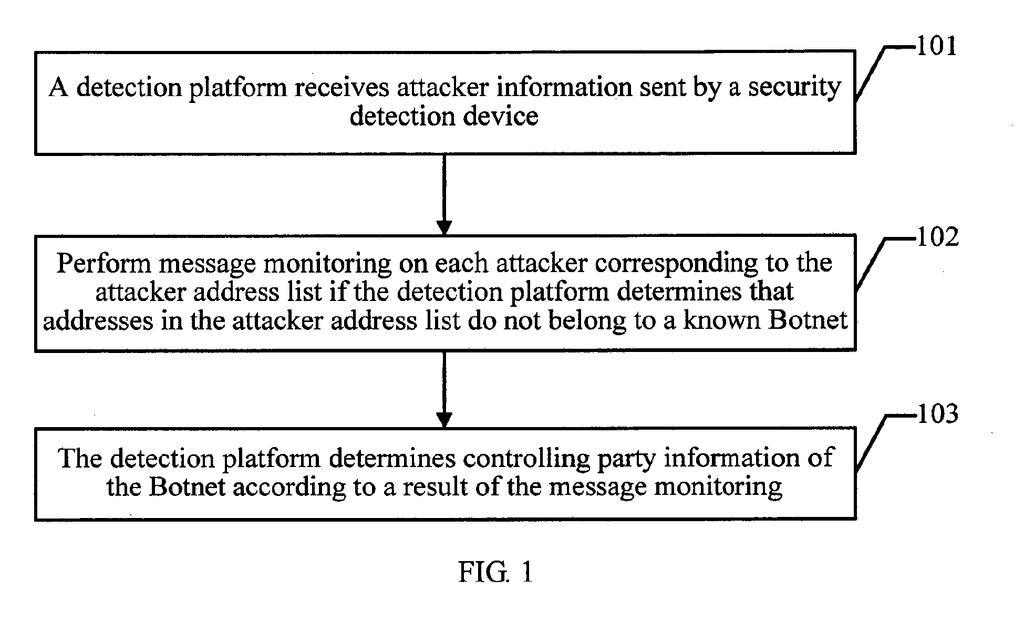
1. **Data Ingestion**: The system collects a wide range of data, crucially including virtual currency (cryptocurrency) transactions that are potentially associated with malicious activity, as well as Internet traffic patterns, and sentiment signals from social media, blogs, and news feeds.
2. **De-anonymization**: Using advanced techniques, the system can *de-anonymize* selected virtual currency transactions, tracing them back to the originating or receiving endpoints (often previously difficult, given the pseudo-anonymous nature of many cryptocurrencies).
3. **Correlation and Analysis**: Collected and de-anonymized data is correlated with one or more *subscribed entities*—organizations or individuals at risk—to determine the likelihood of an APT. This is quantified via a *threat index*.
4. **Actionable Intelligence and Mitigation**: If the threat index for an entity surpasses a threshold, the system can notify the entity in advance or trigger one or more mitigation actions automatically. These mitigations may include increasing network bandwidth, changing service priorities, or increasing monitoring within the network.
This process is designed to be real-time and dynamic, leveraging historical knowledge and current indicators to stay ahead of increasingly resourceful adversaries.
—
**Potential Applications Across Industries**
This technology’s reach is vast. Let’s look at key industries and use cases where predictive cyber defense is not just advantageous, but essential.
**1. Financial Services (Banks, Fintech Companies, Payment Processors)**
– **Risk**: Financial services firms face relentless threats, including ransomware, extortion attacks, and theft—often orchestrated via sophisticated APTs funded through virtual currencies.
– **Application**: By correlating suspect crypto transactions (e.g., ransom demands or infrastructure purchases occurring on the dark web) with anomalous traffic or suspicious social chatter about their brands, institutions can receive early warnings and preemptively boost security or network defenses before breaches occur.
**2. Critical Infrastructure (Energy, Utilities, Transportation)**
– **Risk**: Utilities are prime nation-state APT targets, as was seen in the NotPetya attacks and the compromise of power grids worldwide.
– **Application**: Real-time sentiment analysis combined with a spike in crypto transactions linked to infrastructure procurement can signal impending attacks—giving grid operators time to implement heightened access control and system isolation.
**3. Government Agencies and Defense**
– **Risk**: State actors target government entities for espionage, disruption, and extortion.
– **Application**: De-anonymizing payments to entities suspected of selling exploits, or identifying coordinated attacks before they launch (by analyzing sentiment and transaction flows) can foil efforts against sensitive targets.
**4. Healthcare and Life Sciences**
– **Risk**: Hospitals have been devastated by ransomware, endangering patient data and care.
– **Application**: Early detection of coordinated efforts or payments linked to ransomware operators enables hospitals to lock down systems or move critical data before attackers strike.
**5. Media, E-commerce, and Telecommunications**
– **Risk**: With reputational risk and high exposure to public sentiment, these sectors are APT magnets, particularly for ideologically driven attacks.
– **Application**: The hybrid sentiment-transaction approach can detect Goliath-scale DDoS recruitment or hacktivist-driven campaigns before websites or services are brought down.
**6. Managed Security Service Providers (MSSPs) and Cloud Providers**
– **Risk**: As security partners for dozens or thousands of businesses, their infrastructure is an appealing supply chain target.
– **Application**: Integrating this invention into their core platforms allows MSSPs to offer predictive breach protection as a value-added service.
—
**Technical and Business Advantages**
Unlike traditional systems that are reactive or limited to single data streams (only monitoring traffic, for example), this approach offers several unique advantages:
– **Proactive Threat Prediction**: By anticipating attacks using broad indicators—network, financial, social—companies can defend before being breached.
– **De-anonymization Capability**: The ability to relate virtual currency transactions to malicious activity and endpoints is a game-changer for catching attackers who exploit pseudonymity.
– **Automated, Dynamic Response**: The system can take action in real-time (e.g., allocate more bandwidth or isolate sensitive segments), reducing damage without human intervention.
– **Historical and Contextual Analysis**: The threat index incorporates lessons from past attacks, continually improving accuracy.
– **Seamless Integration**: Designed for deployment within Software-Defined Networking (SDN) environments and more traditional networks alike.
—
**Market Size Analysis: Total Addressable Market (TAM) and Serviceable Addressable Market (SAM)**
Estimating the market potential for proactive, predictive cyber defense platforms that utilize cryptocurrency monitoring and sentiment analysis involves examining several overlapping sectors:
**A. Global Cybersecurity Market**
– *Size*: According to MarketsandMarkets, the cybersecurity market is projected to reach [over $300 billion by 2027](https://www.marketsandmarkets.com/PressReleases/cyber-security.asp), up from around $220 billion in 2023.
– *Drivers*: Growth is driven by the proliferation of threat vectors (IoT, remote work, BYOD), escalating ransomware incidents, and increased regulatory scrutiny (e.g., GDPR, HIPAA).
**B. Cryptocurrency and Blockchain Analytics Market**
– *Size*: The global blockchain analysis market (which includes cryptocurrency monitoring for compliance, security, and forensics) was valued at over $300 million in 2021 and is projected to exceed $2 billion by 2028, with double-digit CAGR. (Source: [Fortune Business Insights](https://www.fortunebusinessinsights.com/blockchain-analytics-market-102316))
– *Relevance*: As more attacks include virtual currency components (e.g., ransomware paid in Bitcoin), tools that can de-anonymize or monitor such transactions are vital.
**C. Threat Intelligence Platforms and Managed Security Services**
– *Size*: The threat intelligence market alone was estimated at $12 billion in 2023 (Allied Market Research) and projected to reach $30 billion by 2030. Managed Security Services (MSS) are anticipated to cross $50 billion globally.
**D. Specific Industry Vulnerabilities**
– **Finance**: North American and European financial institutions each spend billions on cybersecurity annually.
– **Energy/Utilities**: Projected spending on cybersecurity for critical infrastructure to exceed $20 billion globally by 2026 (ABI Research).
– **Healthcare**: U.S. healthcare cybersecurity alone is projected at $125 billion cumulative spend through 2025.
**TAM Estimate:**
If we define TAM as all organizations globally requiring advanced APT mitigation—encompassing government, Fortune 500 enterprises, SMBs, critical infrastructure, healthcare, and financial sectors—the viable TAM for advanced proactive security solutions is conservatively in the hundreds of billions USD.
– **TAM (2024–2028)**: ~$300B–$400B
**SAM Estimate:**
Assuming the early adopters for this novel technology are large enterprises, critical infrastructure operators, major MSSPs, and heavily regulated industries representing ~10–20% of TAM, the near-term SAM is:
– **SAM (2024–2028, Early Adopters)**: $30B–$80B
As trust in predictive analytics and crypto-forensic correlations grows, SAM will edge closer to TAM.
—
**Competitive Landscape and Differentiation**
Existing cybersecurity tools often silo data streams—focusing on endpoint detection, traffic analysis, or dark web monitoring. While companies like Chainalysis and CipherTrace offer cryptocurrency tracing, and vendors like CrowdStrike and FireEye provide APT threat intelligence, *none* currently offer a holistic platform that:
– Ties crypto transaction attribution directly to network events and social sentiment.
– Calculates a dynamic, actionable threat index for specific entities.
– Automatically triggers network-level mitigations in an integrated SDN or hybrid environment.
By converging these capabilities, the invention’s platform is uniquely positioned at the intersection of cryptocurrency forensics, network management, and predictive threat analytics—a blue ocean opportunity.
—
**Implementation and Integration Considerations**
Adopting such a solution does not require a total overhaul of existing defenses, but rather, offers significant value as an augmentation layer—feeding into Security Operations Center (SOC) dashboards, SIEMs (Security Incident and Event Management), or SDN controllers capable of rapid, automated response.
Key integration points include:
– **Data Feeds**: Plug-in connectors for social media APIs, blockchain data (Bitcoin, Ethereum, Monero, etc.), Internet traffic logs, historic attack indicators.
– **De-anonymization Engines**: Modules that leverage heuristics, graph analyses, and KYC data from exchanges.
– **Threat Index Dashboard**: Visual interfaces to display risk levels and allow security teams to track changes in real time.
– **Mitigation Orchestration**: APIs to trigger network changes, alert SOC teams, or update firewall and routing rules.
—
**Regulatory and Compliance Implications**
With increasing national and international regulation regarding reporting of breaches, critical infrastructure protection, and privacy, proactive tools like these can help entities maintain compliance—by demonstrating due diligence, rapid incident response, and even providing forensic trails useful for law enforcement.
Privacy and compliance will be crucial: while de-anonymizing transactions for security purposes, the platform must respect privacy rights and operate within legal frameworks (e.g., GDPR, CCPA). Solutions must provide granularity in what is de-anonymized, retaining logs and offering clear auditability.
—
**Challenges and Risks**
Adoption will require buy-in not only from technical leaders but from risk managers and compliance officers. Challenges include:
– **False Positives**: Prediction requires careful balancing to avoid “alert fatigue.”
– **Resource Commitment**: Continuous monitoring of multiple streams can require significant compute investment, but cloud-based deployments can mitigate capital outlay.
– **Privacy and Legal Risks**: De-anonymization must be handled in accordance with laws, with opt-in or explicit authorization.
– **Evolving Adversary Techniques**: As defenses improve, attackers will attempt to bypass detection (e.g., via more sophisticated crypto mixers or encrypted messaging). Systems must evolve in tandem, integrating new forensics as techniques mature.
—
**Vision for the Future: AI-Driven Threat Anticipation**
By combining machine learning, big data analytics, and continuous learning loops, future versions of this platform can become more powerful still:
– **Cross-industry Intelligence Sharing**: Entities under similar attack can benefit from collective intelligence, further sharpening predictive power.
– **Automated Playbooks**: Beyond simple bandwidth increases or prioritization, orchestration could isolate affected subsystems, rollback vulnerable services, or initiate human countermeasures.
– **Integration with Law Enforcement and Regulators**: Help unmask attackers, recover funds, and prosecute criminals.
—
**Conclusion**
The convergence of network analytics, cryptocurrency forensics, and social sentiment monitoring has created a paradigm shift in APT defense. With cyberattacks growing not just in number but in sophistication, systems capable of *predicting* and *preempting* threats before they mature to full breaches are no longer a theoretical luxury—they are becoming a business and national security imperative.
The patented system described here moves us beyond reactive security. By identifying the earliest signals of attack—the purchase of infrastructure with crypto, the gathering of social momentum, the buildup of anomalous traffic—and correlating these signals in real-time, organizations can finally gain the upper hand. As the market for such platforms grows, first movers will not only be protected, but positioned for leadership in the emerging economics of trust and digital resilience.
For organizations serious about security in the age of APTs and cryptofinanced cybercrime, the message is clear: proactive, predictive, and automated defense is not just the future—it is here, now.
—
**Ready to Learn More or Implement Predictive APT Defense?**
As patent attorneys and technologists, we encourage those interested in licensing, integrating, or developing with this technology to reach out for a confidential discussion. The future of cybersecurity is predictive—don’t let your organization fall behind.
Click here and search US 20250165984 A1.