Invented by David H. Sitrick, Russell T. Fling, OL Security LLC
In today’s digital age, content distribution has become more complex than ever before. With the rise of streaming services, online platforms, and digital media, protecting the distribution of content has become a top priority for content creators and distributors. To address this concern, a market for a system and method for securing the distribution of content selected to be protected by an appliance-specific basis, with defined usage rights and/or conditions, has emerged.
This innovative system and method provide content creators and distributors with a comprehensive solution to safeguard their valuable content. By utilizing an appliance-specific basis, the system ensures that only authorized devices can access and distribute the protected content. This means that unauthorized devices, such as pirated streaming boxes or unauthorized streaming services, will be unable to access the content, thus reducing the risk of piracy and unauthorized distribution.
One of the key features of this system is the ability to define specific usage rights and conditions for the protected content. Content creators can set limitations on how the content can be used, ensuring that it is not misused or distributed inappropriately. For example, they can restrict the number of devices that can access the content, limit the number of times it can be viewed or downloaded, or even set an expiration date for the content. These defined usage rights and conditions provide content creators with greater control over their content and help protect their intellectual property.
Moreover, this system offers a secure distribution channel for content. By using encryption and other security measures, the system ensures that the content remains protected throughout the distribution process. This means that even if the content is intercepted or accessed by unauthorized individuals, it will be rendered useless without the necessary decryption keys. This level of security gives content creators and distributors peace of mind, knowing that their content is safe from unauthorized access or distribution.
The market for this system and method is rapidly growing as content creators and distributors recognize the importance of protecting their intellectual property. With the increasing prevalence of digital piracy and unauthorized distribution, it has become essential for content creators to implement robust security measures. This system provides a comprehensive solution that addresses these concerns and offers a secure and controlled distribution channel for protected content.
In conclusion, the market for a system and method for securing the distribution of content selected to be protected by an appliance-specific basis, with defined usage rights and/or conditions, is a valuable asset for content creators and distributors. This innovative solution offers enhanced security, control, and peace of mind, ensuring that valuable content remains protected from unauthorized access or distribution. As the digital landscape continues to evolve, it is crucial for content creators to embrace such systems to safeguard their intellectual property and maintain control over their content distribution.
The OL Security LLC invention works as follows
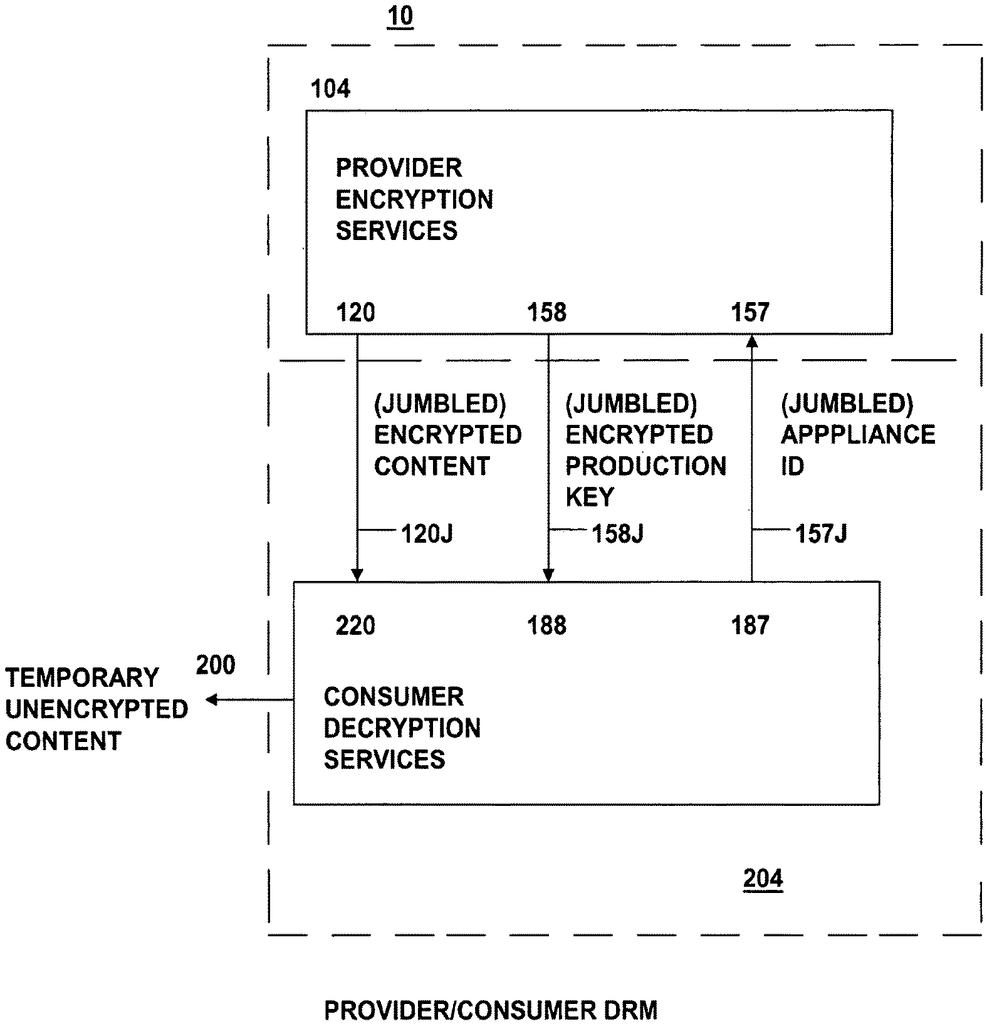
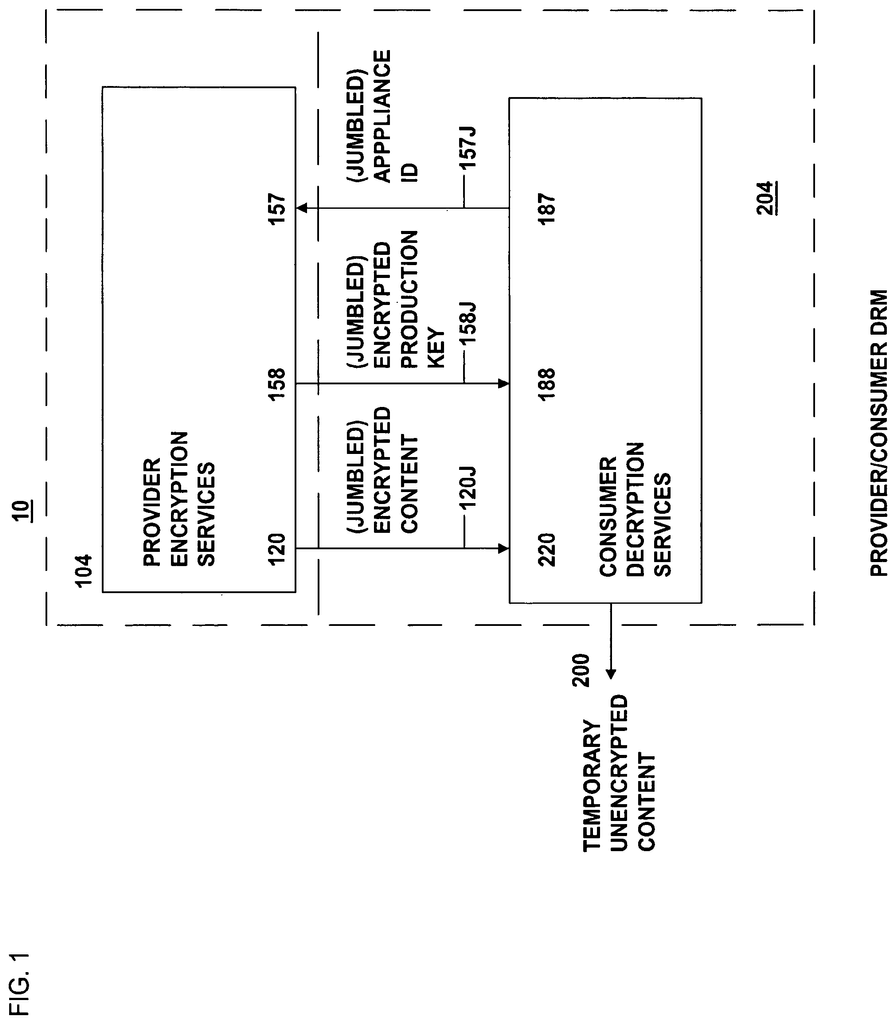
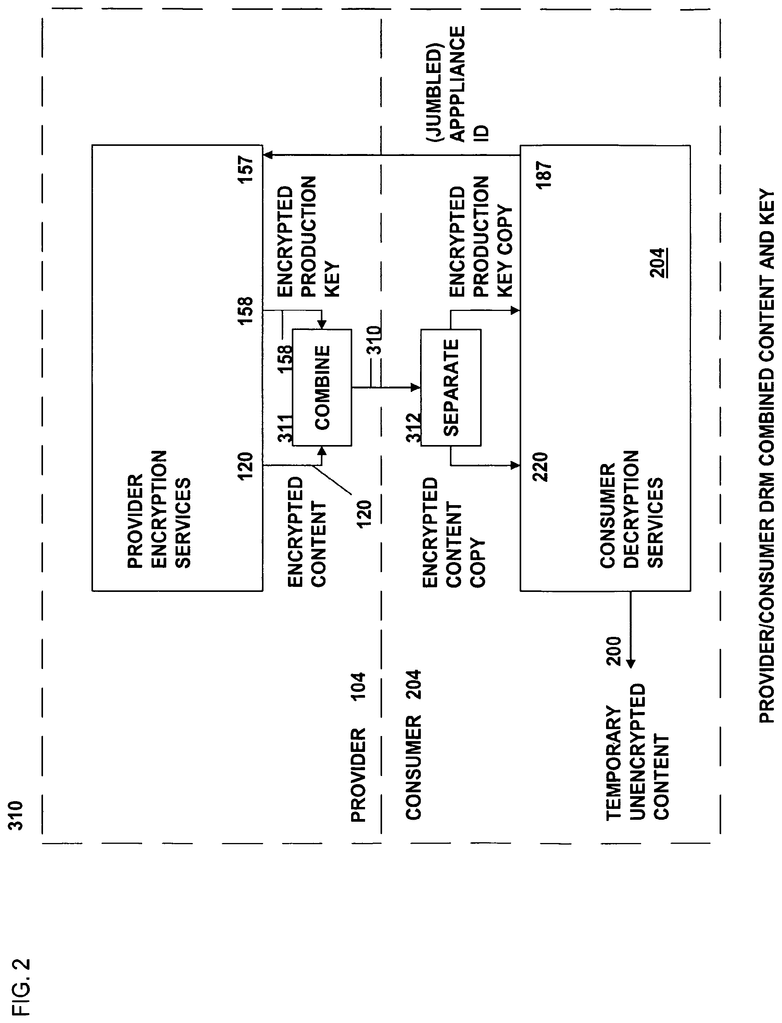
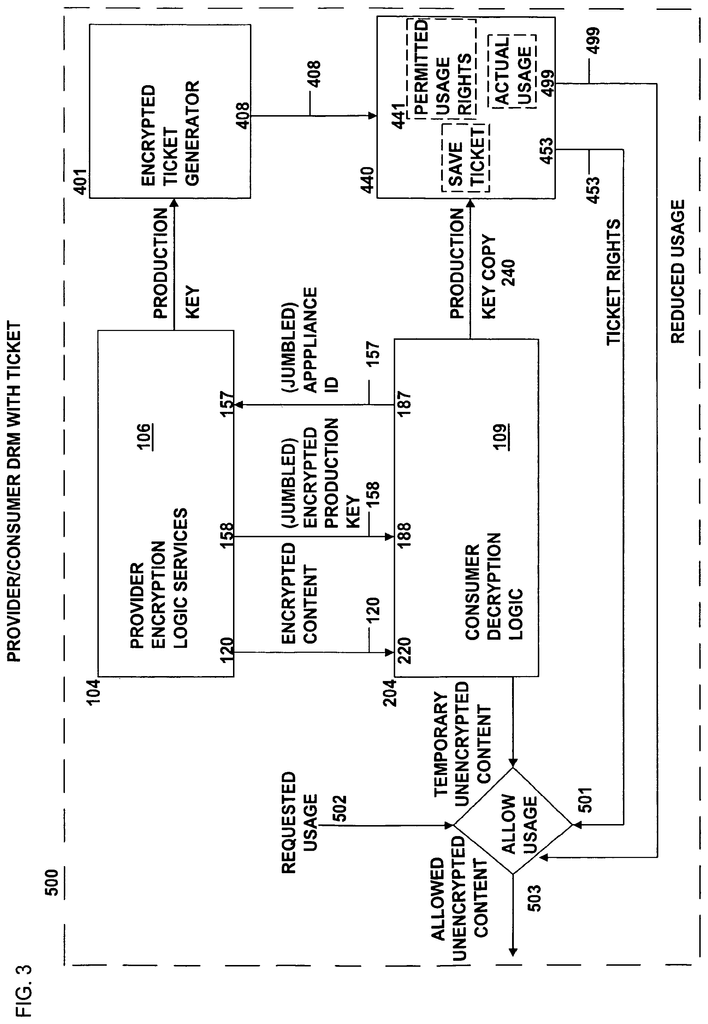
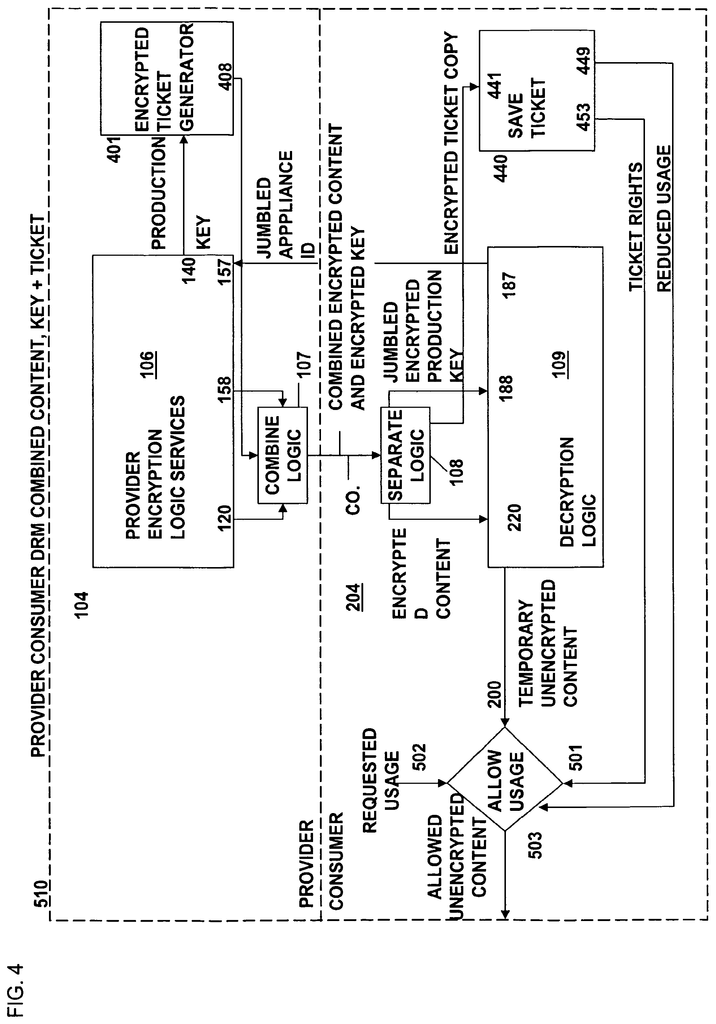
The present invention is a data rights management system, more specifically a secured system, and methodology, as well as apparatus and methodologies for production and consumer systems, for securely using protected electronic content files (protected data), and it also relates controlled distribution and regulating usage, according to usage rights (associated to the respective contents to control usage), either restricted to one specific recipient device, or to multiple specific recipient devices, or to usage on any authorized recipient without restriction, to control the use of respective content as a software application, exporting and
Background for System and method for securing distribution of content selected to be protected by an appliance-specific basis, with defined permitted usage rights associated for the selected content”.
There is a need for a controlled distribution of digital file in order to protect proprietary ownership rights, non-copyrighted work and other rights such as trade secrets and business proprietary.
Up to now, users have been confused and frustrated by the complexity of existing techniques used to provide secure communication (or distribution) of protected data files. The so-called electronic files are often not secure and fail to be used in areas that require it.
In the case of distribution data files of text, images and electronic sheet music we have developed a number formats to secure transmit and restrict, as well as selectively allow for viewing and/or print of electronic data files. Sibelius, a music composition software company (which offers a product called “Scorch”) and Finale/Make Music, Inc. offer proprietary systems. Finale/Make Music, Inc., a company that provides its own proprietary tools, and Sibelius (which offers a?Scorch? In addition, a number of encryption schemes for the transfer of audio files have been developed. Apple Computer, Inc. provides a number of schemes on its iTunes website, as well as similar ones from other companies. PGP, Inc., (Pretty Good Privacy, Inc.) offers both free and commercial-grade products that implement data encryption techniques for RSA encryption on files that represent data content or application file. Adobe Acrobat (?PDF? Many Adobe Acrobat,?PDF? Windows XP, from Microsoft, Inc., also offers options for the encryption of files.
Secure Distribution” usually involves encryption or proprietary converters of some sort. Many options are available. For those who are familiar with the subject, encryption, hash functions and other one-way functions as well as symmetric and nonsymmetric encryption, will be no surprise. For a general introduction, read Applied Cryptography by Bruce Schneier’s Chapter 2, Protocol Building Blocks. Also, refer to Section 2.3 regarding One-Way Functions. The present invention does not restrict itself to any particular type of encryption and is compatible with all that fit the specific design requirements of an embodiment.
The specific meaning of the terminology used in this patent specification will be that which is defined there.
The notion of an one-way function, is fundamental to public-key encryption. One-way functions, while not themselves protocols, are fundamental building blocks.
It is relatively easy to reverse one-way functions, but they are significantly more difficult to compute. It is relatively easy to calculate f(x) given x, but it is difficult to reverse f(x).
A trap-door function is a type of one-way one-way functions that has a secret trapdoor. In one direction, it is easy to calculate. But in the opposite direction, it’s hard. If you know the secret, it is easy to compute the function the other way. It is easy to calculate f(x), given x. But it is hard to compute the function x when given f (x). There is a secret information y that makes it easy to compute x given f(x), y and f(x).
The one-way hash functions can be called many things, including message digest, fingerprints, cryptographic checksums, message integrity checks (MIC) and manipulation detection codes (MDC). The one-way hash function is a key component of modern cryptography and another building block in many protocols.
Hash functions have been around for a very long time in computer science. A hash function can be mathematical or not. It takes a variable length input string, called a preimage, and converts it into a fixed length (generally shorter) output string, called a hashvalue.
The point is to create a value to indicate whether the candidate pre-image will likely be the same as a real pre-image. Since hash functions are often many-to-1, they cannot be used to determine with certainty whether two strings are identical, but can be used to obtain a reasonable level of accuracy.
A one-way hash is a function that only works in one direction. It is easy for a user to calculate a value by analyzing a preimage. However, it is difficult to create a preimage that hashes a specific value. A good one-way function is also collision free: It’s hard to create two pre-images that have the same hash value.
The hash functions can be made public. There is no need to keep the process secret. A one-way hash functions security is in its one-wayness. The output does not depend on the input. On average, a single bit change to the pre-image will affect half the bits of the hash value. It is computationally impossible to find a preimage that hashes the same value as a given hash value.
A hash value can be viewed as a fingerprinting of files. To verify that someone else has a file you have, ask them for the hash value. It is very likely that the person who sends you a hash value that matches yours has that file. A one-way function without a secret key is usually used so that anyone can check the hash. Message Authentication Codes can be used if only the recipient should be able verify the hash.
A Message Authentication code (MAC), or data authentication code (DAC), consists of a hash function that is one-way with a secret key. The hash value depends on both the preimage and the secret key. It is the same theory as hash functions except that only the person with the key has the ability to verify the hash value. A MAC is created from a hash function, or a block-encryption algorithm. There are also dedicated MACS.
Whitefield Diffie & Martin Hellman described public-key cryptography in 1976, using two keys: one public, and the other private. The private key is difficult to determine from the public key. “Anyone with a public key can encrypt messages, but only the person who has the private key is able to decrypt them.
Mathematically speaking, the process is built on trap-door functions that are one-way. The easy way is to use encryption. The instructions for encryption are a public key. Anyone can encrypt messages. Decryption, on the other hand, is a difficult task. It is best to make it so difficult that even supercomputers and people with years of experience could not decrypt the message. The private key is the secret or trap-door. “With that secret, encryption is as simple as decryption.
To send a message by using public-key encryption:
(1) Both parties have agreed on a public key cryptosystem.
(2) Party 2 receives a public key from Party 1.
(3) Party 2 encrypts and sends to Party 1 a message encrypted with Party 1’s Public Key.
Click here to view the patent on Google Patents.