Invented by Antonio J. Espinosa, Shashi Sastry, Vincent Bemmel, Sameer Merchant, Corlina Inc
Hardware systems are the backbone of any organization’s IT infrastructure. They include servers, routers, switches, and other devices that are used to store and process data. These systems are vulnerable to cyber-attacks, which can result in data theft, system downtime, and financial losses.
To address these security concerns, companies are investing in systems and methods that enable and verify the trustworthiness of their hardware systems. These systems and methods use various techniques to ensure that the hardware systems are secure and trustworthy.
One of the most popular techniques used in these systems is the use of hardware security modules (HSMs). HSMs are specialized hardware devices that are designed to secure and protect cryptographic keys and other sensitive data. They provide a secure environment for storing and processing sensitive data, and they are tamper-resistant, making them difficult to hack.
Another technique used in these systems is the use of trusted platform modules (TPMs). TPMs are hardware devices that are integrated into the motherboard of a computer or other hardware system. They provide a secure environment for storing and processing sensitive data, and they are tamper-resistant, making them difficult to hack.
In addition to these techniques, companies are also investing in systems and methods that enable and verify the trustworthiness of their hardware systems through the use of software. These systems use various software tools to monitor and detect any suspicious activity on the hardware systems. They also use machine learning algorithms to detect and prevent cyber-attacks.
The market for system and method for enabling and verifying the trustworthiness of hardware systems is expected to grow significantly in the coming years. According to a report by MarketsandMarkets, the global market for hardware security modules is expected to grow from $1.1 billion in 2020 to $1.8 billion by 2025, at a CAGR of 10.6% during the forecast period.
The increasing adoption of cloud computing, the growing number of cyber-attacks, and the increasing demand for secure and trustworthy hardware systems are some of the factors driving the growth of this market. Companies are investing heavily in these systems and methods to ensure the security and trustworthiness of their hardware systems, and this trend is expected to continue in the coming years.
In conclusion, the market for system and method for enabling and verifying the trustworthiness of hardware systems is growing rapidly. Companies are investing in these systems and methods to ensure the security and trustworthiness of their hardware systems, and this trend is expected to continue in the coming years. With the increasing number of cyber-attacks and data breaches, it has become essential to ensure the security and trustworthiness of hardware systems, and these systems and methods provide an effective solution to this problem.
The Corlina Inc invention works as follows
The TaaS server first establishes a baseline characteristics profile for the IoT System. This allows the software agent to collect system data that is indicative of different characteristics of the IoT System. TaaS server creates an initial baseline characteristics profile of the IoT System. This allows the TaaS Server to compare the received data with the baseline characteristics profiles in order to identify discrepancies. These discrepancies can be due to desirable software updates. In this case, the discrepancies could be integrated into baseline characteristics profiles, or they may be the result of the IoT being unintentionally compromised.
Background for System and Method for Enabling and Verifying the Trustworthiness of Hardware Systems
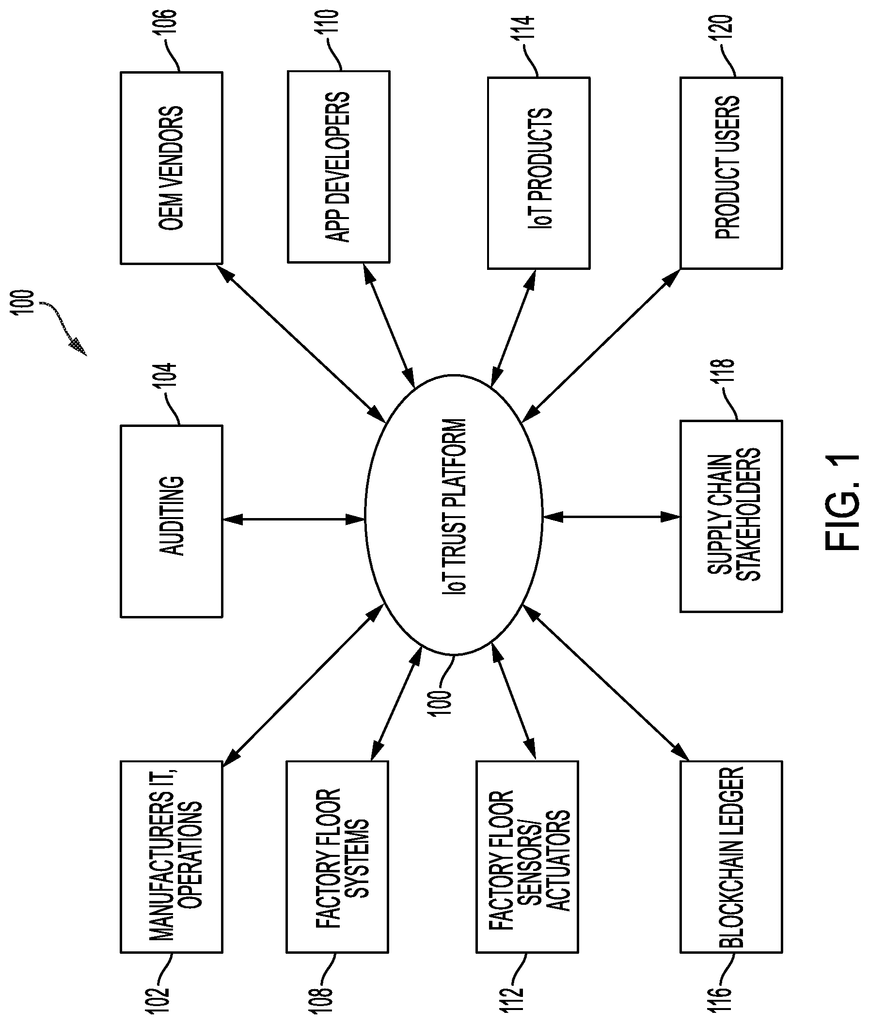
The Internet-of-Things has introduced a paradigm of distributed sensor and actuators embedded in industrial systems and connected via an IoT industrial network. This includes a high level of embedded sensors that provide real-time visibility of factory system behavior. Modern systems can scale up to fully automated, self aware, just-in-time factories.
The current trend of manufacturing automation and data sharing is sometimes referred to by the terms Industrie 4.0, or Factory of the Future. Industrie 4.0 is a digital transformation that leverages four key stages: visibility, predictability, transparency and adaptability. “Real-time visibility is a key step in the evolution of self-aware Industrial IoT systems (IIoT).
The network is a crucial part of modern manufacturing. These networks are often put under greater stress in modern factory applications, as they must support higher loads that have a direct impact on the performance of operations.
The degree of trustworthiness of the IIoT can be defined as “the level of confidence that one has in the system’s ability to perform as expected, even when faced with environmental disruptions, errors by humans, and system faults or attacks.” To earn the trust of users, systems are made trustworthy. The IIoT’s trustworthiness can be expressed by a combination characteristics such as security, safety and reliability. The process of establishing and tracking IIoT reliability can be used to track the trustworthiness as individual IIoT products progress through their manufacturing process, and into normal usage in an industrial manufacturing setting.
The key problem with conventional systems is the lack of a consistent framework for validating and establishing trust in IIoT devices. Anomalies in the manufacturing process can negatively affect the effectiveness of a process and/or the integrity or manufactured products.
The development, manufacture, installation, and operation of an IIoT (e.g. encompassing one IIoT device, manufacturing processes/machines, factories, etc.) usually involves multiple organizations. At any time during a device’s lifespan, the OS and application software installed on it can be compromised. “Any component of the device can be replaced during its installation or operation stages.
There is no intuitive, common gauge that can be used to determine the level of trustworthiness for an IIoT product. A gauge of this kind could give manufacturers or products confidence that they are meeting operational standards. There is currently no way to track a device as it moves between the factory floor and its deployment site, which can be anywhere in the world. Even if the trustworthiness of a device could be certified in the manufacturing phase there are currently no consistent methods for verifying its authenticity during the lifetime of the product.
The invention relates to computer-implemented methods for determining the trustworthiness of an Internet of Things system in a networked setting. The method can be embodied in various ways, including: receiving system data from an IoT agent via a networked communication interface; generating a baseline characteristic profile using one or multiple processors; storing the profile in a storage device that is accessible to one or several processors; receiving updated system information from the IoT agent; and determining if the updated data indicates the IoT has been compromised.
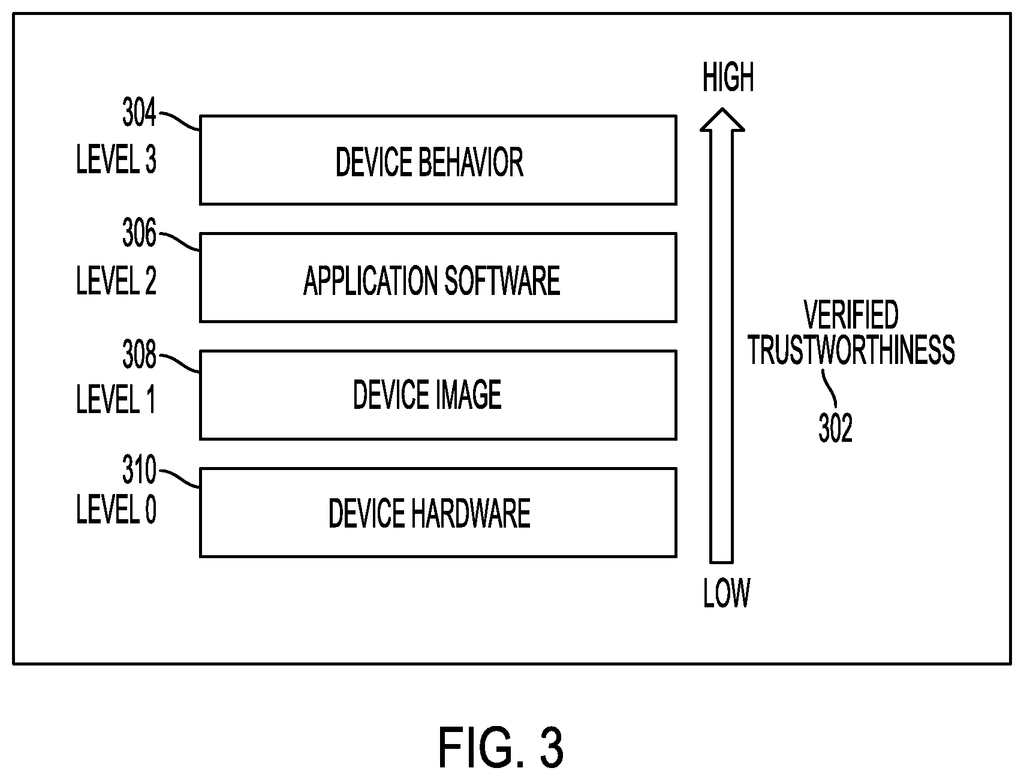
In certain embodiments, system data may include one or more of the following: system hardware data, system image data, application data and system behavior data. In certain embodiments, a portion or all of the system data can be derived from the firmware of an IoT system. The storage system can also be implemented as a ledger on the blockchain.
The method can also include steps to update the baseline characteristics by replacing a part of the baseline characteristic profile with a part of the updated data. The method can also be characterized by sending an alert when the trust metric indicates the IoT is compromised. In certain embodiments of the method, generating the baseline characteristic profile includes generating at least a part of the system data. Comparing the updated data to the baseline characteristic profile involves: generating hash from the updated data and comparing it against the baseline character profile.
Certain embodiments relate to a system that determines trust of an Internet of Things system (IoT system) within a networked setting. The system can include a communication device in communication with an IoT via a networked environment. The communication interface may be configured to receive artifacts harvested from the IoT by a software installed on the IoT. The one or multiple processors can be configured to generate a baseline characteristic profile based on at least part of the system data, store the baseline profile in the storage device, receive updated system information indicative of artifacts that have been harvested from the IoT System via the communication interface, and then determine whether updated data indicates the IoT System is compromised.
In certain embodiments, system data may include one or more of the following: system hardware data, system image data, application data and system behavior data. At least a part of the system data can be retrieved from the firmware of the IoT systems. In some embodiments, a storage system can be embodied in a blockchain ledger. The one or more processors can be configured to update the baseline characteristics by replacing a minimum portion of baseline characteristics with a minimum portion of updated system data. Certain embodiments can further be configured to generate an alert when the trust metric indicates the IoT is compromised. In certain embodiments generating the baseline characteristic profile includes generating at least a part of the system data. Comparing the updated data to the baseline characteristics profiles comprises: generating hash from the updated data and comparing it against the baseline profile.
The baseline characteristics profiles are stored in a storage device that is accessible to one or more processors. They are also received from the software agents installed on IoT systems.
In certain embodiments, system data may include one or more of the following: system hardware data, system image data, application data and system behavior data. The storage system can also be a ledger. In certain embodiments the executable portions on the non-transitory, computer-readable storage medium can be configured so that, when executed by the processor, they cause the processor replace at least part of the baseline characteristics profile, with at least some of the updated data. In certain embodiments those executable parts may also be configured to cause a processor to generate an alarm when the trust metric indicates the IoT is compromised. “Generating the baseline characteristic profile can include generating at least a part of the system data. Comparing the updated data to the baseline characteristics profiles may also involve generating a hash based on that updated data.
Since IIoT systems (e.g., a device, a group of devices, a manufacturing process/machinery/line, a factory, a warehouse, a security monitoring system, and/or the like) play a vital role in remote monitoring and control of industrial processes, warehouse management processes, logistics processes, and/or the like it is critical to verify the operational integrity of such systems at all times. The embodiments of the invention monitor IIoT/IoT systems behavior continuously to ensure that they are not compromised while operating. Users of these systems can be assured that the data they generate is trustworthy because IIoT/IoT system integrity is maintained.
Various embodiments overcome inherent challenges in a networking environment to maintain high levels of assurance that a specific networked system is uncompromised. There are many ways that an IoT/IIoT system (e.g. devices, collections, or the like) can be compromised in today’s complex IoT/IIoT environment. Individual devices or systems can be compromised physically, e.g. when individuals with malicious intentions, or who do not have the necessary knowledge to interact securely with devices, manipulate them (e.g. replacing parts, changing the user-definable features of devices, connecting other devices to the communication ports, etc.). Other devices connected to the device through a network may not be able to detect these changes made to the device by the user. Other trusted individuals may be able to see the changes being made, but they may not recognize their impact, may not even know what device is being changed, or may simply not notice the changes.
Devices and other systems can also be compromised electronically, for instance when unauthorized software (e.g. spyware, keytrackers, viruses and/or similar software) is installed on the device, when unauthorized remote changes are made to the device, etc. These changes can be detected by trusted networks, but they are unable to determine whether or not the changes were authorized. These changes can be difficult to see by humans, so even those with physical access may not know if the device is compromised.
Various embodiments provide systems and method for overcoming this difficulty in determining if a system has been compromised. They utilize characteristics of systems unique to computerized networks to monitor and determine the level of trustworthiness. As an example, since various hardware components are associated with electronic signatures that can be detected by other networked devices (e.g. MAC addresses, timing signs, user settings and/or similar characteristics), and electronic/software components also have unique characteristics that are detectable through networked devices (e.g. license key codes and software version numbers) various embodiments could track one or more characteristics to determine if a system is compromised.
Embodiments” of the present invention include, among others, the following methods and systems during the lifetime of an IoT/IIoT System:
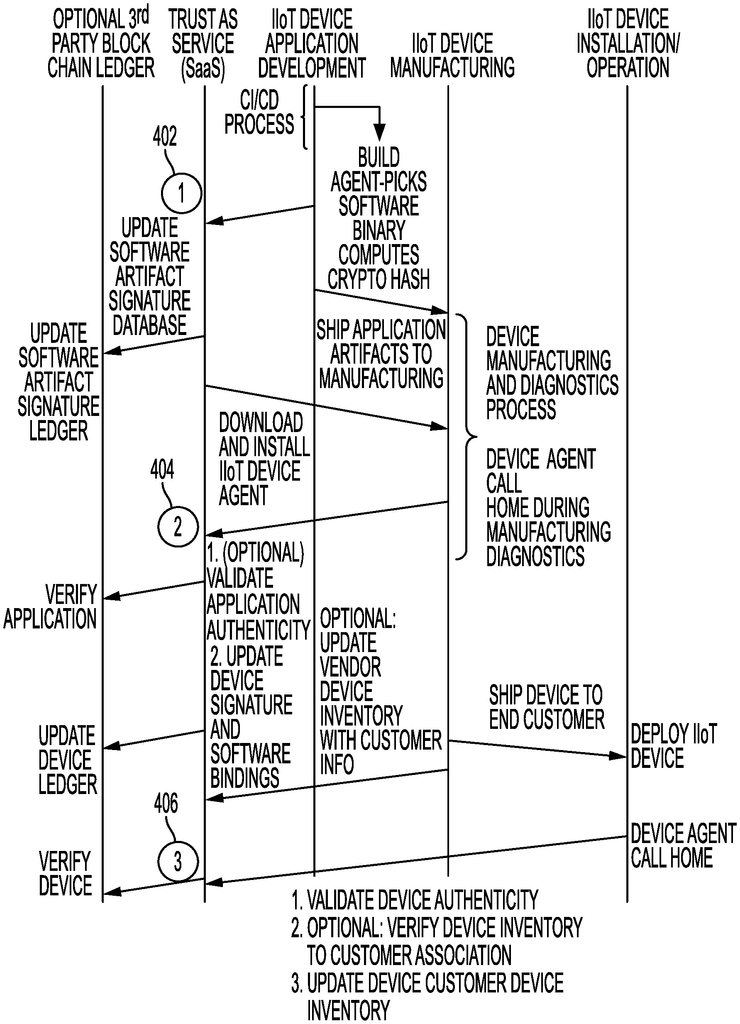
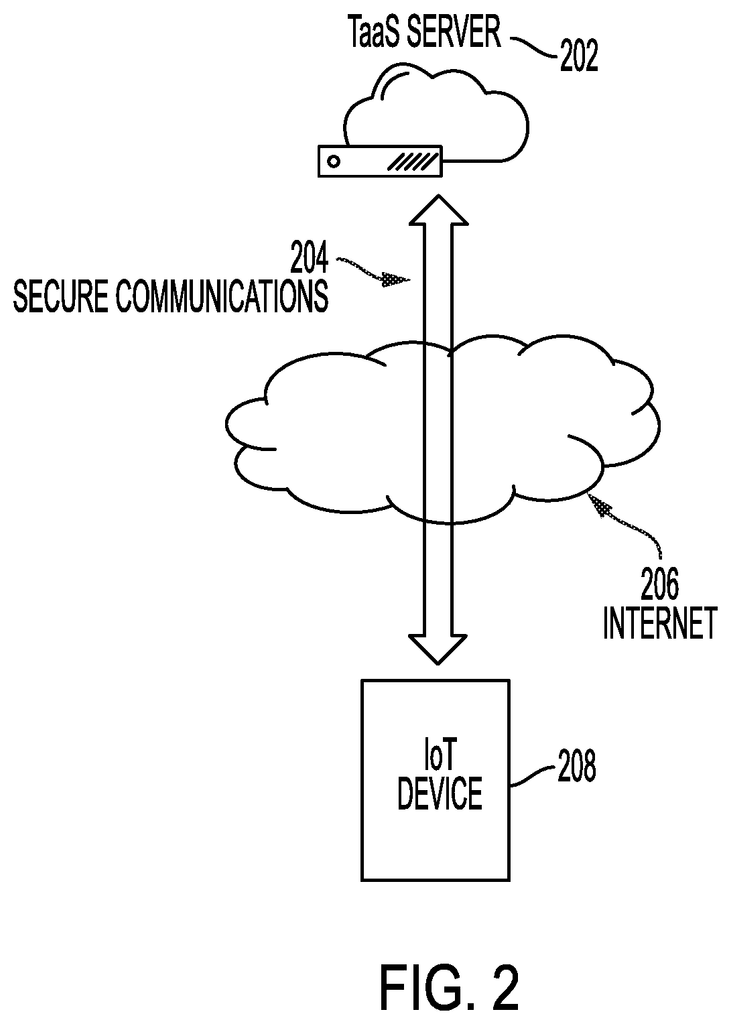
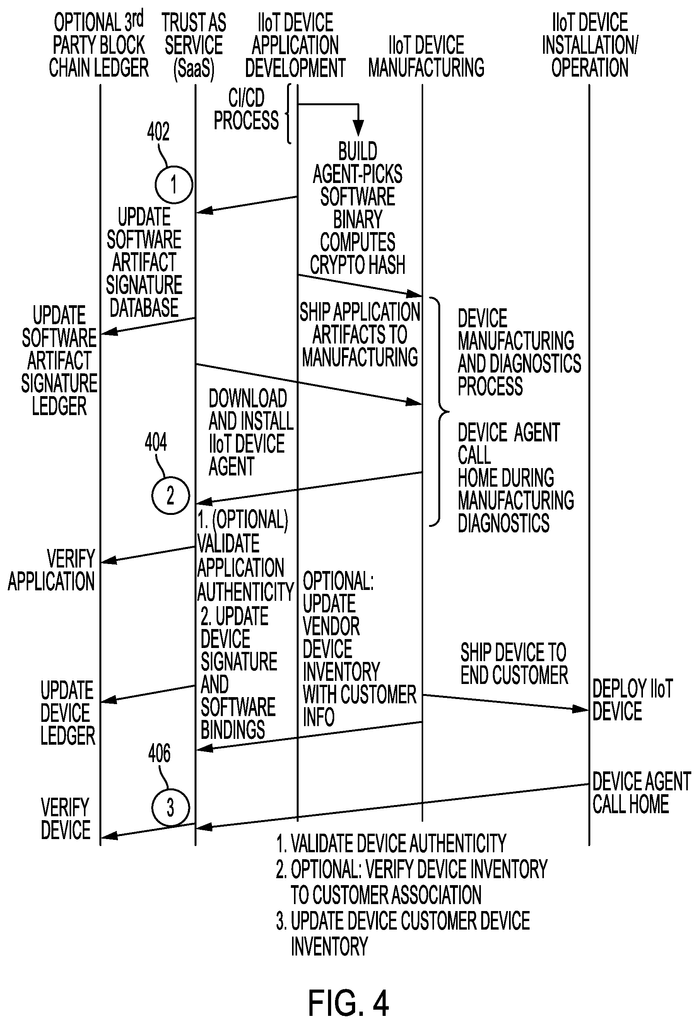
The Trust as a Service, according to embodiments of this invention, establishes a IoT/IIoT System Trust at any point during a system?s life cycle regardless of its location. The system also offers the option of establishing trust using a third-party ledger (e.g. a blockchain ledger like IBM’s Hyperledger or an IOTA managed ledger). Authentication of the IoT/IIoT and any installed software is possible at any time. Software agents installed on IoT/IIoT systems provide vital device data and operational statistics. This information can be used by the TaaS (e.g. a TaaS Server) to determine what level of trust should be given to a specific system.
Some embodiments of the invention provide: “Trust as a service” “Some embodiments of the present invention thus provide:?Trust as a Service?
Click here to view the patent on Google Patents.