Invented by Vikram Chandrasekhar, Yongseok Park, Shan Jin, Pranav Madadi, Eric Johnson, Jianzhong Zhang, Russell Ford, Samsung Electronics Co Ltd
Machine learning, a subset of artificial intelligence, has revolutionized the way businesses analyze data and make informed decisions. It involves the development of algorithms that enable computers to learn from and make predictions or take actions based on large amounts of data. This technology has proven to be particularly effective in identifying patterns and trends that are not easily detectable by humans.
Root cause analysis, on the other hand, is a systematic approach used to identify the underlying causes of problems or failures. It aims to address the root cause rather than just treating the symptoms, which can lead to more effective and long-lasting solutions. By understanding the root cause of a problem, businesses can prevent similar issues from occurring in the future.
The combination of machine learning and root cause analysis has proven to be a powerful tool for businesses across various sectors. In manufacturing, for example, machine learning algorithms can analyze large volumes of sensor data to identify patterns that may indicate the root cause of equipment failures. This enables businesses to proactively address potential issues and minimize downtime.
In the healthcare industry, machine learning algorithms can analyze patient data to identify patterns that may indicate the root cause of diseases or adverse events. This can help healthcare providers develop personalized treatment plans and improve patient outcomes.
The market for machine learning and root cause analysis is also growing in the financial sector. Machine learning algorithms can analyze large amounts of financial data to identify patterns that may indicate fraudulent activities or market trends. This enables financial institutions to detect and prevent fraud, as well as make more informed investment decisions.
The market for machine learning and root cause analysis is expected to continue growing in the coming years. According to a report by MarketsandMarkets, the global machine learning market is projected to reach $8.81 billion by 2022, growing at a compound annual growth rate of 44.1% from 2017 to 2022. This growth is driven by the increasing adoption of machine learning across various industries, as well as advancements in technology and the availability of large amounts of data.
However, there are also challenges that need to be addressed in order to fully realize the potential of machine learning and root cause analysis. One of the main challenges is the availability of high-quality and relevant data. Machine learning algorithms rely on large amounts of data to learn and make accurate predictions. Therefore, businesses need to ensure that they have access to clean and relevant data in order to achieve meaningful results.
Another challenge is the interpretability of machine learning algorithms. While these algorithms can identify patterns and make predictions, they often lack the ability to explain how they arrived at a particular conclusion. This can be a concern, especially in industries where decisions have significant consequences, such as healthcare or finance. Efforts are being made to develop more interpretable machine learning models to address this challenge.
In conclusion, the market for machine learning and root cause analysis is growing rapidly, driven by the increasing demand for advanced analytics and the need to identify and address the underlying causes of problems in various industries. While there are challenges that need to be addressed, the potential benefits of this technology are immense. As businesses continue to embrace machine learning and root cause analysis, we can expect to see further advancements and innovations in this field.
The Samsung Electronics Co Ltd invention works as follows
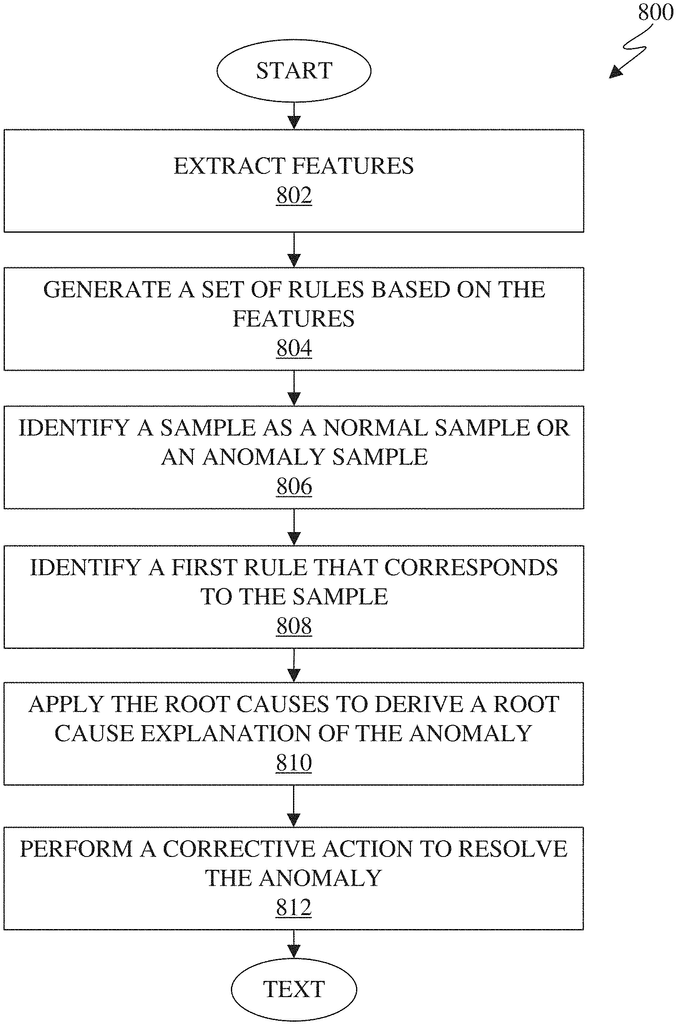
A method of discovering and diagnosing anomalies in networks.” The method involves receiving alarm data and key performance indicator data. The method extracts features from samples obtained after discretizing KPI and alarm data. The method generates a set rules based upon the features. The method includes identifying whether a sample is a normal or anomaly sample. After identifying the anomaly, the method identifies a first set of rules that are applicable to the sample. The first rule includes symptoms and root cause explanations for the anomaly. The method also includes determining the root cause of the anomaly by applying the root causes and taking corrective actions based on that explanation.
Background for Machine learning and root cause analysis:
Recently the number of wireless communication subscribers, such as those on a cellular system, has exceeded five billion, and it continues to grow rapidly. Due to the increasing popularity of mobile data devices such as tablets and ‘note pads’, smart phones, and other mobile data products among consumers and business, wireless data traffic demand is growing rapidly. “computers, netbooks, eBook readers, machine type devices, etc.
The explosive growth of mobile data traffic poses significant challenges to mobile network operators due to their limited bandwidth and infrastructure. Changes in network conditions, such as higher levels of radio frequency interference, can negatively impact user experience. For example, increased stalling when streaming media content. To improve user experience, providers of service must quickly discover anomalies and uncover their root causes, then take remedial actions. In general, cellular networks require significant human and time resources to detect and fix network anomalies. It leads to prolonged network outages, and a diminished user experience.
This disclosure provides machine learning-based root cause analysis.
In one embodiment, a device for discovering and diagnosing anomalies in a network is provided. The apparatus includes both a communication interface as well as a processor. The communication interface can receive alarm data and key performance indicators (KPIs). The processor is designed to extract features from samples obtained after discretizing KPI data and alarm data. The processor is set up to create a rule set based on features. A portion of samples that meet the rules are anomalies. Based on the KPI and alarm data, the processor can identify a sample as either a normal or anomaly sample. The processor, upon identifying the anomaly, is configured to determine a first rule corresponding to the sample. This first rule indicates the symptoms and root cause of the anomaly in the sample. The processor will identify and apply the root causes in order to derive the root cause explanation for the anomaly. This is based on the KPIs which are related to the symptoms of the anomaly. The processor is set up to take a corrective measure to resolve an anomaly in accordance with the first rule.
In another embodiment, there is a method. The method involves receiving KPI and alarm data. The method extracts features from samples obtained after discretizing KPI and alarm data. The method generates a set rules based upon the features. A portion of the samples which satisfy the rules are anomalies. The method identifies a sample either as a normal or anomaly sample. The method identifies a first rule corresponding to the sample in response to identifying it as an anomaly sample. The first rule identifies the symptoms and root cause of any anomaly in the sample. The method involves applying root causes in order to derive an explanation for the anomaly using KPIs linked to symptoms and root reasons of the anomaly. The method involves performing a correction to resolve the anomaly in accordance with the first rule.
The following figures, descriptions and claims will reveal other technical features to a person skilled in the arts.
It may be helpful to define certain terms and phrases that are used in this patent document before beginning the DETAILED DESCRIPTION. The term “couple” is used. The term ‘couple’ and its derivatives refers to any communication, direct or indirect, between two or more components. The terms “transmit” and “receive” are used interchangeably. ?receive,? The terms’receive,’ Both direct and indirect communication are included in the terms?include? Include and include? The terms ‘include’ and ‘comprise? The term?include’ and derivatives thereof mean to include without limitation. The word?or? The term?or? is inclusive and means both. The phrase “associated with” is used. As well as derivatives of the term, it means to include, to be contained in, to interconnect with or to contain, to couple with or to connect with, to be communicable, to cooperate with or to be near, to be proximate, to be bound to or to be with, to have, to have a property, to have a relation to or to be with. The term “controller” is used. The term ‘controller’ refers to any device, system, or component thereof that controls at lease one operation. A controller can be implemented as hardware, software or firmware. Functionality associated with a controller can be distributed or centralized, locally or remotely. The phrase “at least one” is used. When used in conjunction with a list, it means that different combinations can be made of any of the items listed, but only one may be required. As an example, “at least one: A, C, and B?” Includes any of the combinations A, B, and C. Also, includes A and B. A and C. B and C. And A and B.
Moreover, the functions described below may be supported or implemented by one or several computer programs. Each of these computer programs is composed from computer-readable program code, and each is embodied on a computer-readable medium. The terms “application” and “program? The terms?application? Refer to one or more computer program, software component, set of instructions, procedures or functions, objects, classes or instances, related data or a part thereof, adapted for implementation into a suitable computer-readable program code. The phrase “computer readable code” is used. The phrase “computer readable program code” includes all types of computer code including source code and executable code. The phrase “computer-readable medium” is used. Any type of medium that can be accessed by a PC, including a CD, DVD, or hard drive. A “non-transitory” medium. A computer-readable medium does not include wired, wireless or optical communication links that transmit transitory electrical signals or other signals. Non-transitory computer-readable media includes media that can permanently store data and media that can store data and then overwrite it, such as an optical disc or erasable memory devices.
The patent document contains definitions for certain other words and phrases. The ordinary person with knowledge of the art will understand that, in most cases, these definitions are applicable to both past and future uses.
FIGS. The various embodiments described in this document, as well as FIGS. 1-8 discussed below, are only intended to be used for illustration and not to limit the scope. The principles of this disclosure can be used in any wireless communication system that is suitable.
Data traffic has increased ever since the deployment of 4G communications systems. In order to meet the growing demand for wireless data, there have been efforts made to improve 5G or pre-5G communications systems. The 5G or Pre-5G communication system can also be called a “Beyond4G Network”. Or a “Post LTE System.
The 5G communication system will be implemented at higher frequencies (mmWave), e.g. 60 GHz, to achieve higher data rates. In 5G communication systems, beamforming, Massive Multiple-Input Multiple-Output (MIMO), Full Dimensional MIMO, array antennas, analog beam-forming, large-scale antenna techniques, and Full Dimensional MIMO can all be used to reduce propagation loss.
In 5G communication systems, the development of system network improvements is underway based on advanced small-cells, cloud Radio Access Networks, ultra-dense network, device-to-device communication (D2D), wireless backhaul (RANs), moving network, cooperative communications, Coordinated Multi-Points, reception-end interference cancelation and similar. Hybrid QAM and FSK Modulation (FQAM), sliding window superposition (SWSC), non-orthogonal Multiple Access (NOMA), sparse code multiple (SCMA) and filter bank multiple carrier (FBMC) have all been developed as advanced coding modulation technologies (ACMs) in the 5G system.
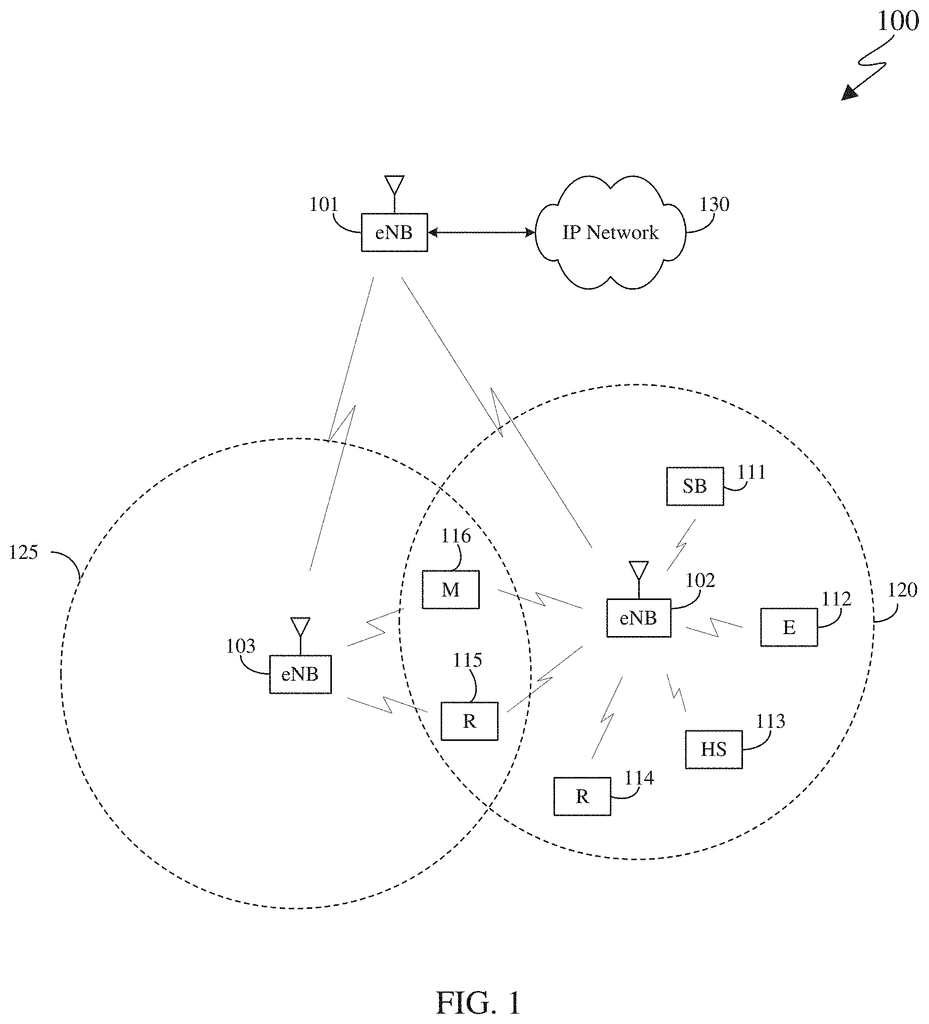
FIG. “FIG. In FIG. 1, the wireless network 100 is shown as an example. The figure 1 is merely for illustration purposes. “This disclosure could include other embodiments of wireless network 100.
The wireless network 100 consists of an eNodeB 101, an ENB 102 and an ENB 103. The eNB 102 communicates with the eNB 103. The eNB 101 communicates also with at least one Internet Protocol network (IP network) 130, such the Internet, a proprietary IP or data network. In some embodiments, the wireless 100 network includes a server which maintains the eNBs.
Depending on the type of network, base station is used. BS or ‘Base Station’ can refer to any component (or collection of components) configured to provide wireless access to a network, such as a transmit point (TP), transmit-receive point (TRP), an enhanced base station (eNodeB or gNB), femtocells, macrocells, WiFi access points and other devices that are wirelessly enabled. Any component or collection of components that is configured to provide wireless network access, including a transmit point, transmit-receive points (TRP), enhanced base stations (eNodeB, eNB, or gNB), macrocells, femtocells, WiFi access points (AP), and other wirelessly capable devices. Base stations can provide wireless access according to one or more wireless protocols. For example, 5G 3GPP’s New Radio Interface/Access, LTE, LTE-A, High Speed Packet Access, Wi-Fi 802.11a/b/g/n/ac etc. To make things easier, we will use the terms ‘BS’ and?TRP? In this patent document, the terms?BS? In this patent document, the terms?TRP? The term “user equipment” can also vary depending on the type of network. Depending on the network type, the term ‘user equipment? Any component, such as “mobile station”,? ?subscriber station,? ?remote terminal,? ?wireless terminal,? ?receive point,? or ?user device.? The terms ‘user equipment’ and?UE? In this patent document, the terms?user equipment? In this patent document,?UE? and?UE? are used to refer to wireless remote equipment that wirelessly connects to a BS.
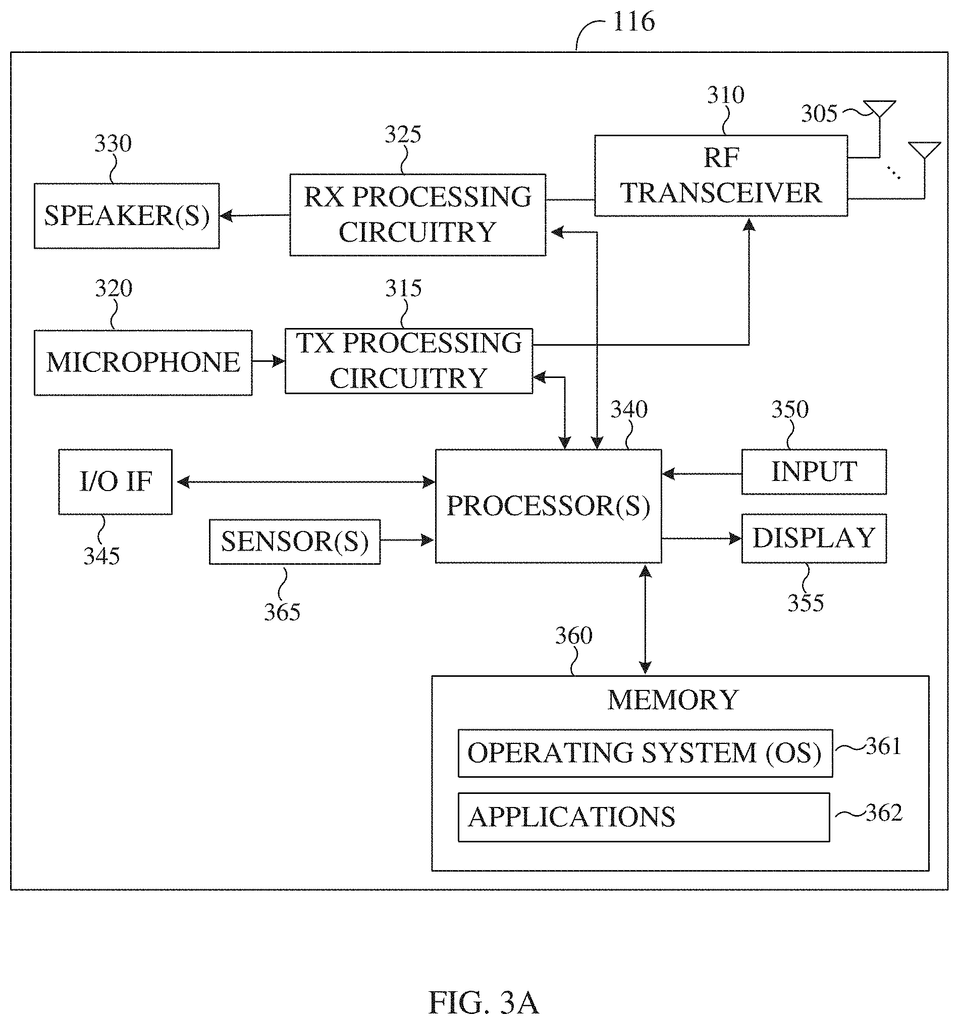
The eNB 102 is a wireless access point to the network for a plurality of UEs within the coverage area 120. The first group of UEs consists of a UE 111 which can be found in a small enterprise (SB); a UE 112, located within an enterprise (E); a UE 113 located within a WiFi hotspot(HS); a UE 114 located inside a residence (R); a UE 115 located inside a residence (R); a UE 116 which could be a mobile (M) device such as a cell-phone, wireless laptop The eNB 103 offers wireless broadband access to network 130 within a coverage zone 125. The UE 115, and UE 116 are part of the second group of UEs. “In some embodiments, the eNBs may use 5G, LTE, LTE-A or WiMAX to communicate with the UEs 111 – 116.
The dots on the map show the approximate coverage area 120 and 125. They are only shown in a circular shape for illustration and explanation purposes. The coverage areas of eNBs such as 120 and 125 may be irregular in shape, depending on the configuration of eNBs or variations in radio environment caused by natural and manmade obstructions.
As described below in greater detail, cellular networks require significant human time and effort to detect and fix various network anomalies. Human intervention can lead to prolonged network outages, and a diminished user experience. The present disclosure provides analytics that automate the detection and diagnosis of network anomalies. “For example, embodiments describe a method of discovering anomalies in networks and identifying the root causes using machine learning.
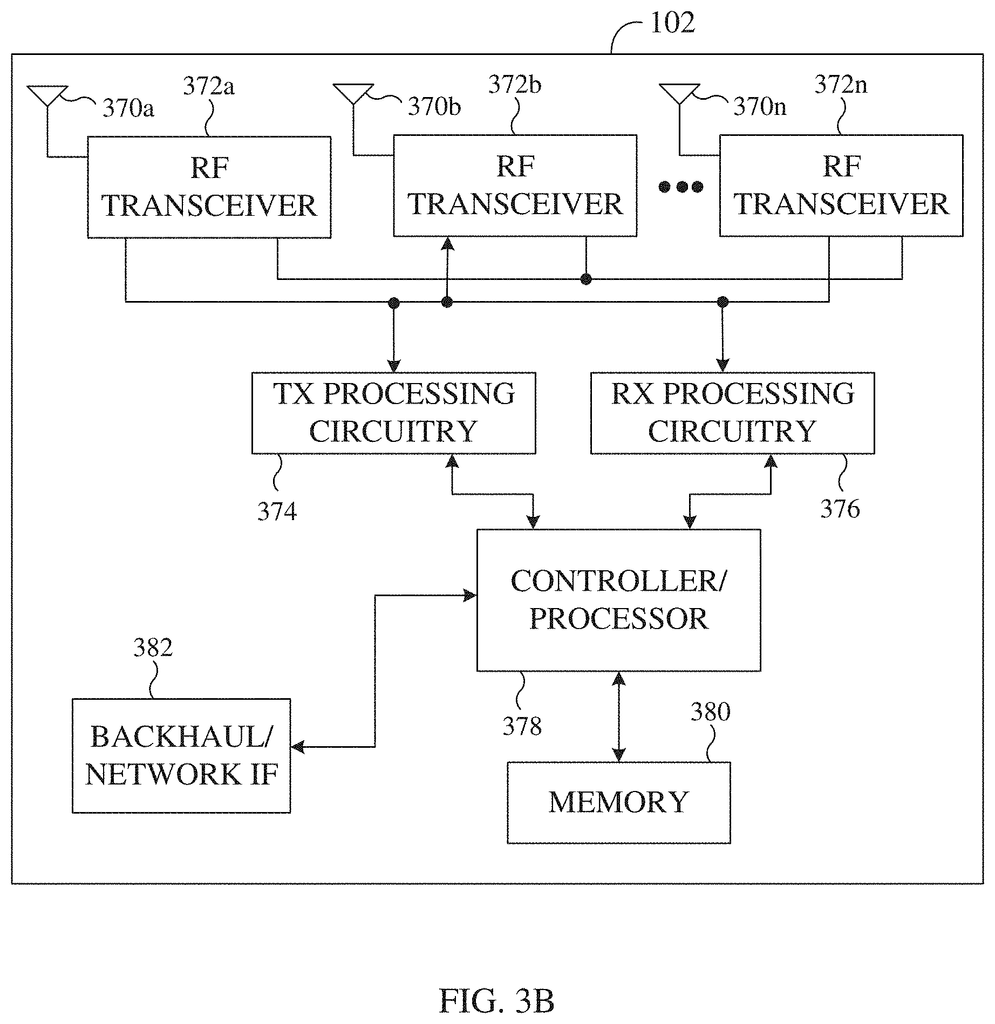
Although FIG. “Although FIG. 1. The wireless network 100, for example, could consist of any number eNBs with any number UEs. The eNB 101 can also communicate directly with a number of UEs, providing them with wireless broadband network access. Similarly, the eNB 102 and 103 could also communicate directly with network 130 to provide UEs direct wireless broadband network access. eNBs 101, 102 and/or 103 can also provide access to additional or alternative external networks such as telephone networks external or data networks. The eNB 101, 102, and 103 can also transmit data to a server, including alarms, key performance indicators (KPIs), and other information about the network’s status. The server can diagnose and detect problems in the network and provide instructions on what corrective action to take based on detected and diagnosed problems.
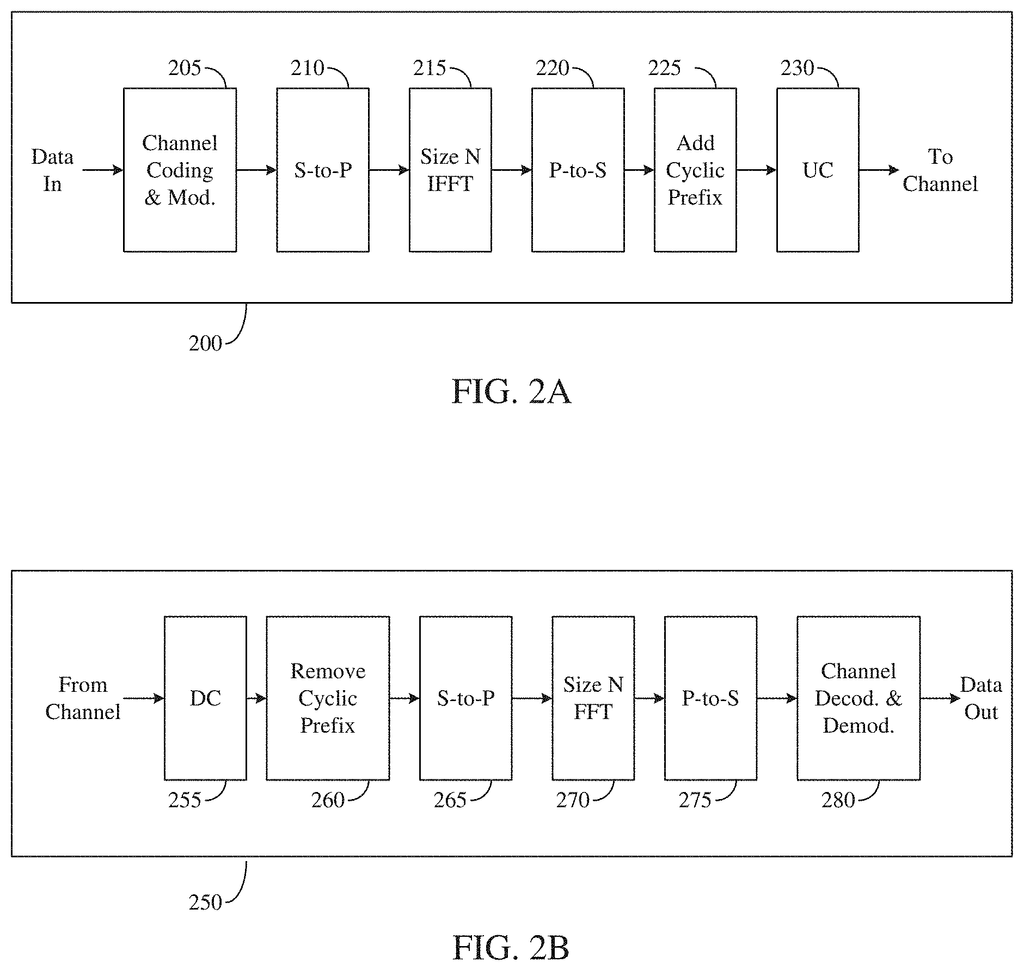
FIGS. The following 2A and 2B are examples of wireless transmit and receive pathways according to the disclosure. In the description below, a transmitting path 200 can be described in terms of being implemented within an eNB. It is understood, however, that the receive route 250 can be implemented as an eNB while the transmit route 200 can be implemented as a UE.
Click here to view the patent on Google Patents.