Invented by William D. Meadow, Locatorx Inc
The market for URL labels is driven by several factors. First and foremost, the increasing use of the internet has led to a growing demand for URL labels. As more businesses and individuals create websites and web applications, the need for URL labels to identify and locate these resources has grown.
Secondly, the increasing use of mobile devices has also contributed to the growth of the URL label market. With more people accessing the internet on their smartphones and tablets, the need for URL labels that are easy to read and navigate on smaller screens has become more important.
Thirdly, the growth of e-commerce has also contributed to the growth of the URL label market. As more businesses move online, the need for URL labels that are easy to remember and share has become more important.
The market for URL labels is highly competitive, with a large number of companies offering URL label services. Some of the key players in the market include Google, Bitly, TinyURL, and Ow.ly. These companies offer a range of URL label services, including shortening long URLs, tracking clicks on URLs, and customizing URLs with branding and other features.
Despite the competition, there is still room for growth in the URL label market. As more businesses and individuals come online, the demand for URL labels will continue to grow. Additionally, as new technologies such as augmented reality and the internet of things become more prevalent, the need for URL labels to identify and locate resources in these new environments will also grow.
In conclusion, the market for URL labels is a rapidly growing and highly competitive market. As the internet continues to play an increasingly important role in our daily lives, the demand for URL labels will continue to grow. With new technologies and innovations on the horizon, the future of the URL label market looks bright.
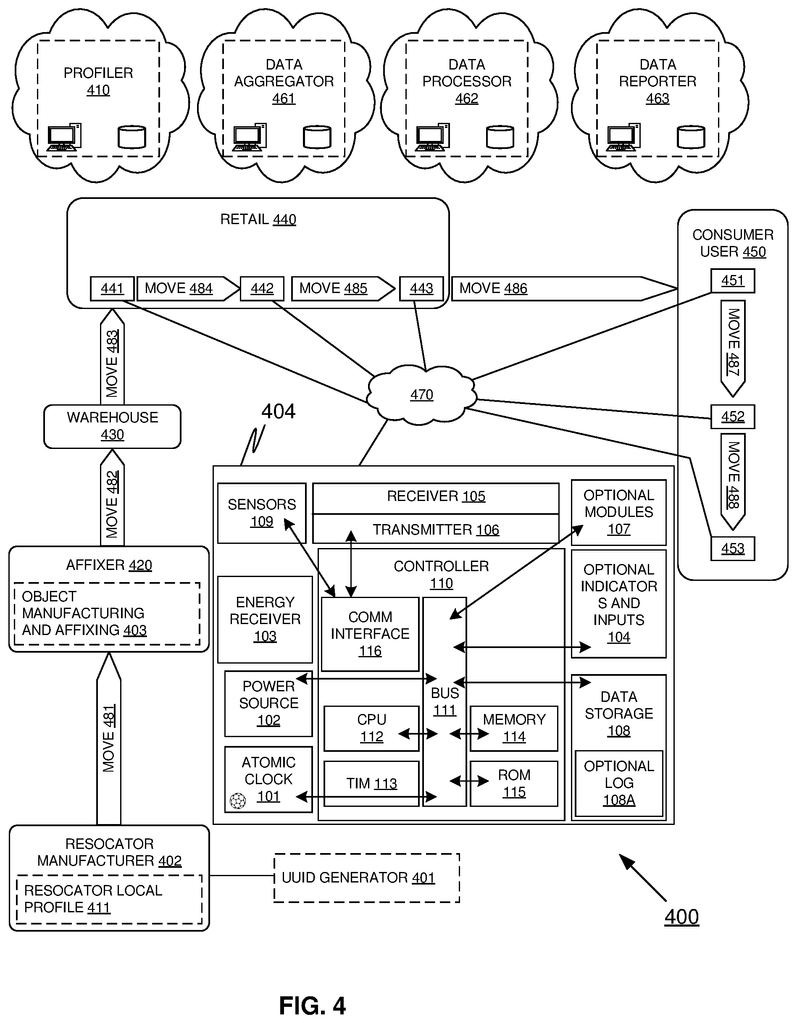
The Locatorx Inc invention works as follows
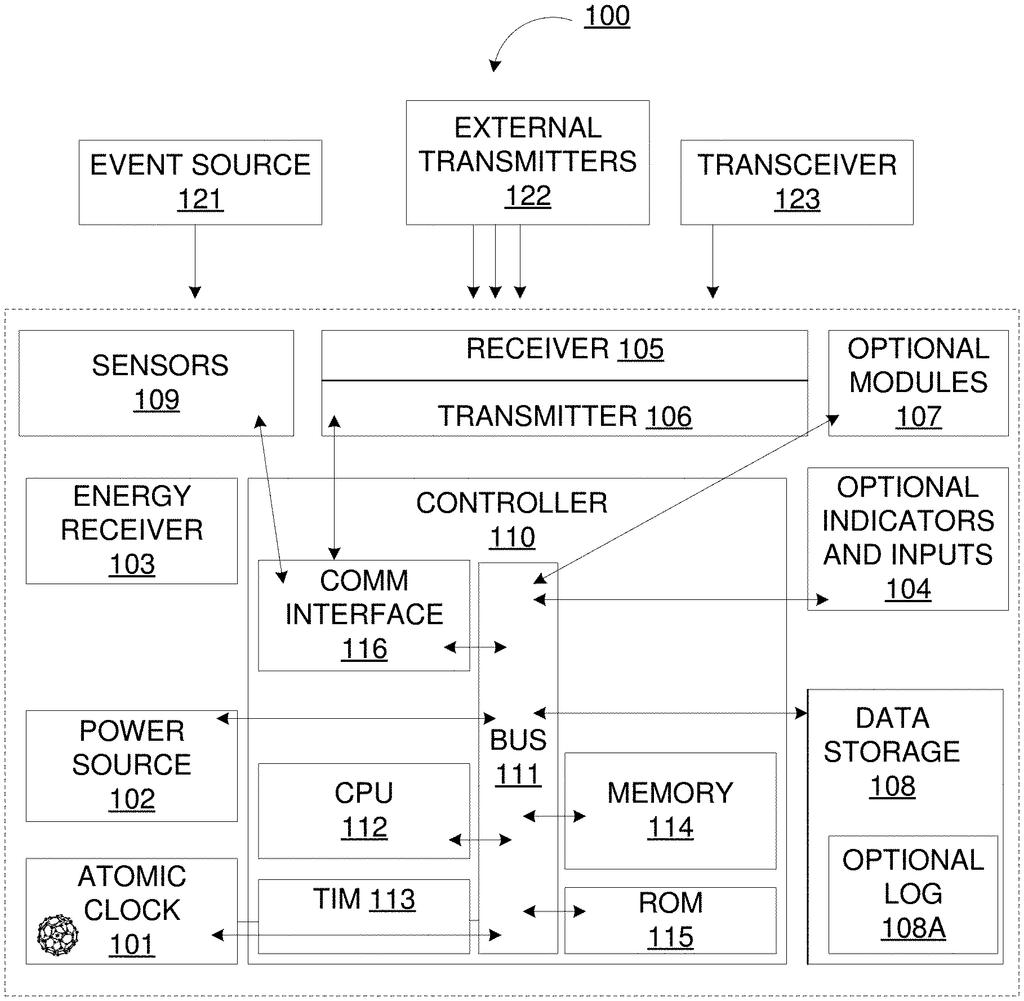
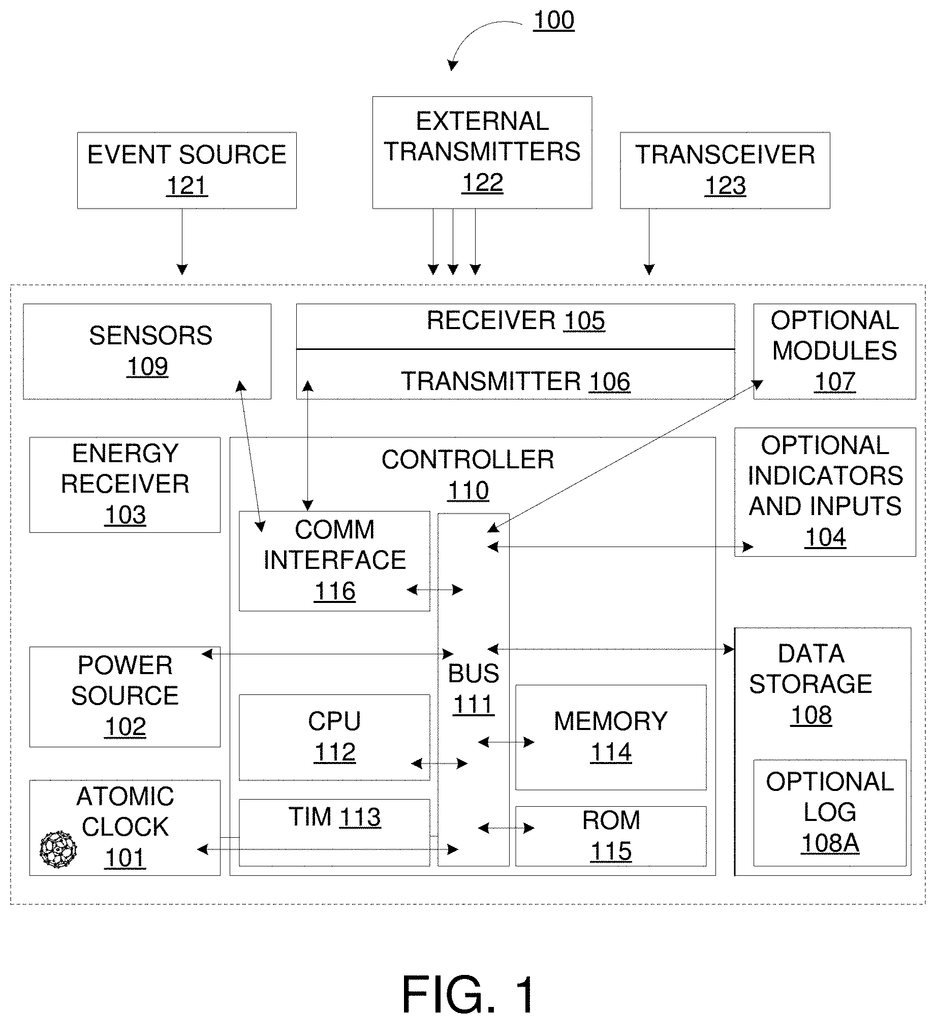
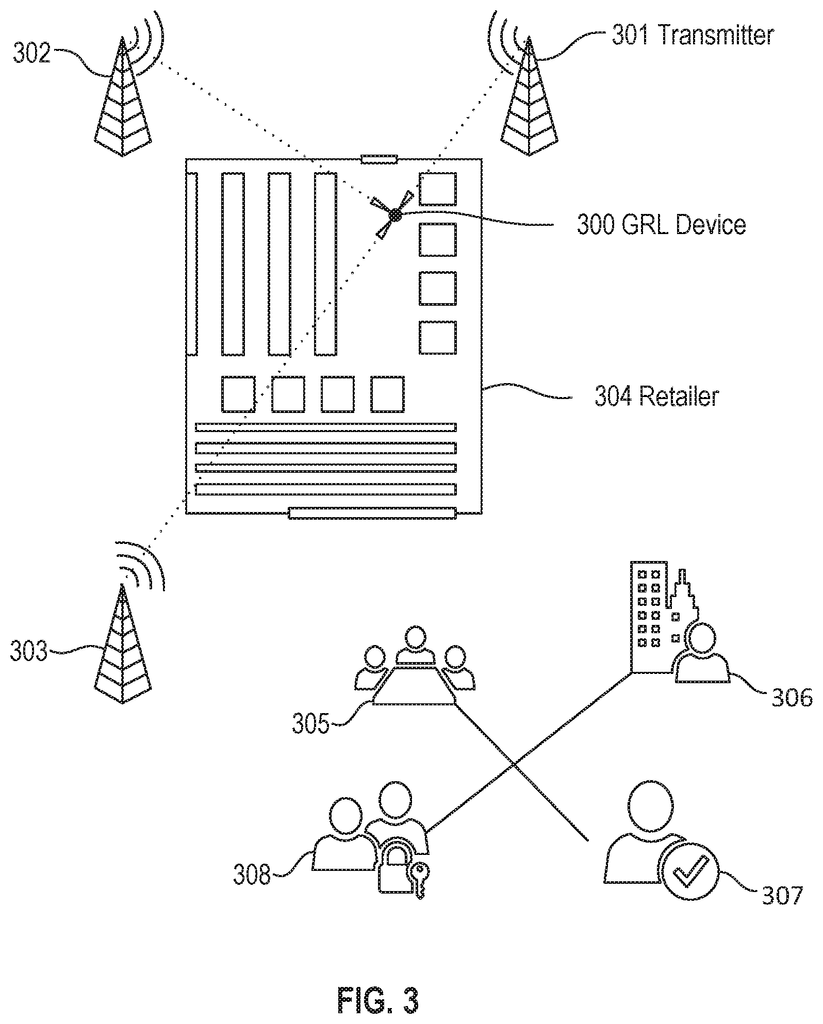
The present disclosure relates methods and apparatus that create a Definable Blockchain within a Chip, along with other components, which can receive, process, and communicate information in order to locate, identify, and track physical Assets, as well as data contained therein. The present disclosure focuses on a Definable Blockchain that can be inserted in product labels or packaging and can communicate via Bluetooth to a Smartphone or other Authenticated Radio Sources to update the Definable Blockchain.
Background for Global resource locator label
A simple analysis of recent news shows that it is very helpful to know who is in a defined area, such as a border or a secure area, in order to combat terrorism. Until now, there has been no efficient and cost-effective way to gather such information. A person can travel freely within the boundaries of a Spatial Domain once they are admitted. It is also difficult to determine who an individual admitted to a Spatial domain has been in close proximity with.
It is well known that passports are used to gain entry within a country’s border. It is also known that a security badge containing an image of the user can be used to gain entry to a restricted area. It is difficult to determine where and when a person with a passport or security badge traveled within the defined boundaries. It’s also difficult to determine who a person has come into contact while within the defined boundaries.
Location-based technology is another area that has grown in popularity over the last decade. Many applications now include location-based functionality. Smartphones, for example, include a geolocation feature if they are unable to receive GPS signals. Some of these applications for Smartphones rely on this ability as described in U.S. Pat. No. 5,945,948.? The Smartphone alone is not reliable or secure for tracking an asset.
Radio-frequency (RFID), is an example wireless data transfer for automatically identifying and tracking tags on objects. RFID devices were viewed by many as an alternative to barcodes, because RFID tags allowed a reader to wirelessly query the tag and then have the tag send back the information stored on the semiconductor chip in the tag. RFID tags can be used by readers within close proximity to transmit pre-stored data, but they are usually limited to communication inside a home or building.
ISO/IEC 20244″ specifies how data is stored in barcodes and/or RFID tags and then digitally signed. The standard’s purpose is to provide a method that can be used by services and data carriers to verify data integrity and originality in offline applications. ISO/IEC 20248 can also be referred as a ‘DigSig’. This is a digital signature that has a low bit count. ISO/IEC 20248 is also an interoperable and effective method for exchanging data messages between Internet of Things (IoT) and Machine to Machine [M2M] Services. Intelligent agents within these services can authenticate data message and detect data tampering. There are still some limitations in RFID technology implementations and frameworks which have made it difficult to add value. One of these is that RFIDs cannot self-locate.
Bluetooth Smart, a new version of Bluetooth that is designed to reduce power consumption and costs while maintaining communication capabilities comparable to the traditional Bluetooth protocol, has been adopted as a data transmission protocol.
Bluetooth can be viewed as a standard wireless technology for exchanging data across short distances using short-wavelength radio waves (using the ISM band between 2.4 and 2.485 GHz), from mobile and fixed devices, and building Personal Area Networks (PANs). Bluetooth is managed by the Bluetooth Special Interest Group, which includes more than 25,000 companies from the fields of telecommunications, computing, networking and consumer electronics. This level of adoption may allow billions of devices to support Bluetooth Low Energy, which can enable a variety of device types and useful apps. It may become more desirable to track Bluetooth-enabled devices as Bluetooth usage increases. It could also be helpful to have functionality on other Bluetooth devices in order to find missing items.
The Internet of Things (IoT) is experiencing a rapid growth in the market due to the convergence of various technologies that allow low-cost, low-power transmission of data among ‘things. The Internet of Things is generally seen as a network of physical ‘things’. These objects are embedded with electronic components, software, sensors and network connectivity that allow them to collect and share data. It allows objects that are embedded with electronics, software, sensors, and network connectivity to be sensed remotely and controlled across existing networks, resulting in increased efficiency, accuracy, and economic benefits. The embedded computer system of each thing allows it to be uniquely identified, but also allow the device to interact with existing Internet infrastructure. There is no reliable or miniature method to locate IoT “things”. “There is no reliable method by which the IoT?things?
Location Based Services+” is the capability to open or close specific data objects using location and/or timing as (controls or triggers) and/or as part of complex cryptographic keys or hashing system and the data that they allow access to. Today, location-based services are used in everything from smart weapons to control systems. These services are used billions of times every day, and they may be the most widely used application-layer framework for computing today. The location data provided is not authenticated. “In the age of IoT, it is risky to ask or tell an IoT device that they should take action or report data if they do not know their actual location.
There are many strategies and technologies that can be used to locate objects inside. The Global Positioning System, which is a satellite-based system, loses power inside due to signal attenuation from construction materials. This affects the coverage required for receivers of at least four satellites. The multiple reflections on surfaces also cause uncontrollable error due to multi-path propagation. The same effects degrade all solutions that use electromagnetic waves to locate indoors, from indoor transmitters and indoor receivers. To compensate for this problem, physical and mathematical methods were applied.
Indoor positioning systems (IPS) are used to locate people or objects inside a building by using radio waves, magnetic field, acoustic signal, or any other sensory data collected from mobile devices. There are a number of commercial systems available, but no standard exists for an IPS. The system design must consider that three independent measurements will be needed to find an unambiguous location (see trilateration).
Indoor Positioning Systems utilize different technologies. These include distance measurements to nearby anchor points (nodes that have known positions, such as Wi-Fi access point), magnetic positioning and dead reckoning. The systems can either locate mobile devices or tags, or they can provide the ambient location and environmental context that devices need to be sensed. Localized IPSs have led to design fragmentation. Systems use a variety of optical, radio or even acoustic technology. To determine precise location, the system must use highly accurate clocks in order to calculate TDOA Time Delay Of Arrival. This is similar to how GPS satellites provide this information to ground units for processing and determining location.
No. No. Watters, et. al. 5,982,324 Another problem is that the clock on a typical cellular mobile terminal may not be accurate and have a tendency of drifting, which is commonly known as clock-drift. The terminal may not be able to make accurate time measurements. This results in an incorrect time and location determination. The drift error increases the longer you use the mobile terminal clock.
As referenced in US2014/0375505A1, TV signals can generate a location for a receiver was taught by U.S. Patent. No. No. The art includes the use of DTV for location, customizing the DTV signal and the hybridization between DTV broadcast location technology with other network or mobile-based technologies.
U.S. Pat. No. Stilp, and others, in 7,440,762, provide examples of infrastructure-based systems (or network-based systems) for determining the locations of Wireless mobile units. Maloney et. al. describe the use of collateral data to enhance or even enable location determination for further applications of infrastructure-based systems. No. No. Nos. Nos.
U.S. Pat. No. No. 6,201,499 describes a method of estimating the formation of hyperbolas based on the TDOA calculation between three or more receiving sensor. The intersection of two or three independently generated hyperbolas from three or four receiving sensors is used to estimate the transmitter location. In Statistical Theory of Passive Location Systems, the methods for determining RF transmitter location based on arrival time differences are described in more detail. Don J. Torrieri, IEEE Transactions on Aerospace and Electronic Systems Vol. AE, 5-20, No. March 1984, pages 183-198) which is expressly incorporated herein by reference.” “(183-198)” which is explicitly incorporated by reference.
Alongside the advent of large numbers of simple hackable computer (aka IoT Devices), has created well-deserved concerns which have slowed down or impeded adoption of technology in environments where it can provide useful services.
Our disclosure will explain how we will implement the required security framework using open source and customized development in our apparatus. We will also provide new methods for resolving concerns and providing a trusted environment for machines that can improve our lives. We share the history of some solutions deployed in this M2M/IoT era.
Security counterfeiting: There’s a major global counterfeiting issue that disrupts normal commerce and free exchange of products. Imitating something is commonly accepted as counterfeiting. Counterfeit goods are counterfeit replicas of real products. Counterfeit goods are sometimes produced to exploit the higher value of the imitation. “The word counterfeit is often used to describe both the forgeries and imitations of currency and documents as well as clothing, handbags and shoes, pharmaceuticals and aviation and automobile parts as watches, software, artwork, toys, movies, and electronic (both parts and completed products).
Security Authentication, as a term is commonly used to describe the goal of providing authentication. It is the process of verifying the truthfulness of an attribute claimed by an entity to be true. In contrast to identification, which is the act of declaring or indicating an assertion purporting to attest to a person’s or thing?s identity, the authentication process actually confirms that identity. While a vendor may sell branded products, he or she might not have proof that each step of the supply chain has been authenticated. Documentation or external affirmations are another type of authentication. The rules of evidence in criminal courts often require that the chain of custody be established. It can be done by a written log of evidence or testimony from the detectives and forensic staff who handled it.
Security Packaging is generally understood to be a technique for minimizing counterfeiting. Security printing and authentication seals can be used to indicate that a package or its contents are genuine. The packages can also include anti-theft measures, such as RFID tags or electronic article surveillance tags. These devices can be detected or activated by exit devices and require special tools to deactivate.
Click here to view the patent on Google Patents.