Invented by Lei Wang, Yan Chen, Xiuqiang Xu, Yiqun WU, Yi Wang, Huawei Technologies Co Ltd
One of the key factors contributing to the growth of this market is the rapid expansion of the global telecommunications industry. The increasing penetration of smartphones and internet connectivity has revolutionized the way people communicate, creating a massive demand for communication methods and apparatus that can handle large volumes of data and provide reliable connectivity.
Moreover, the rise of remote work and virtual collaboration has further fueled the need for advanced communication tools. With more companies adopting flexible work policies and teams spread across different locations, there is a growing requirement for communication methods and apparatus that can facilitate real-time communication, file sharing, and video conferencing.
Another significant driver of this market is the increasing adoption of cloud-based communication solutions. Cloud-based communication platforms offer scalability, flexibility, and cost-effectiveness, making them an attractive choice for businesses of all sizes. These platforms enable seamless integration with existing communication systems, allowing organizations to streamline their operations and enhance productivity.
Furthermore, the market for communication methods and apparatus is witnessing a surge in demand due to the growing popularity of unified communication and collaboration (UC&C) solutions. UC&C solutions integrate various communication channels such as voice, video, messaging, and email into a single platform, providing users with a unified and consistent experience. This convergence of communication channels not only enhances productivity but also reduces costs and improves overall efficiency.
In addition to traditional communication methods, the market is also witnessing a rise in the adoption of emerging technologies such as artificial intelligence (AI) and Internet of Things (IoT). AI-powered communication tools can automate processes, analyze data, and provide personalized communication experiences. IoT devices, on the other hand, enable seamless connectivity between various devices, allowing for efficient communication and data exchange.
However, despite the immense growth potential, the market for communication methods and apparatus faces certain challenges. One of the major challenges is the increasing concerns over data privacy and security. With the rising number of cyber threats and data breaches, businesses and individuals are becoming more cautious about the security of their communication systems. Therefore, communication methods and apparatus that offer robust security features and encryption protocols are likely to gain a competitive edge in the market.
Moreover, the market is highly competitive, with numerous players offering a wide range of communication solutions. To stay ahead in this competitive landscape, companies need to focus on innovation, product differentiation, and customer-centric approaches. Additionally, partnerships and collaborations with other technology providers can help companies expand their product offerings and reach a wider customer base.
In conclusion, the market for communication methods and apparatus is witnessing significant growth due to the increasing demand for seamless and efficient communication solutions. The rise of remote work, cloud-based communication platforms, and emerging technologies are driving the market forward. However, data privacy and security concerns and intense competition pose challenges for companies operating in this market. To succeed, companies need to prioritize innovation, differentiation, and customer satisfaction.
The Huawei Technologies Co Ltd invention works as follows
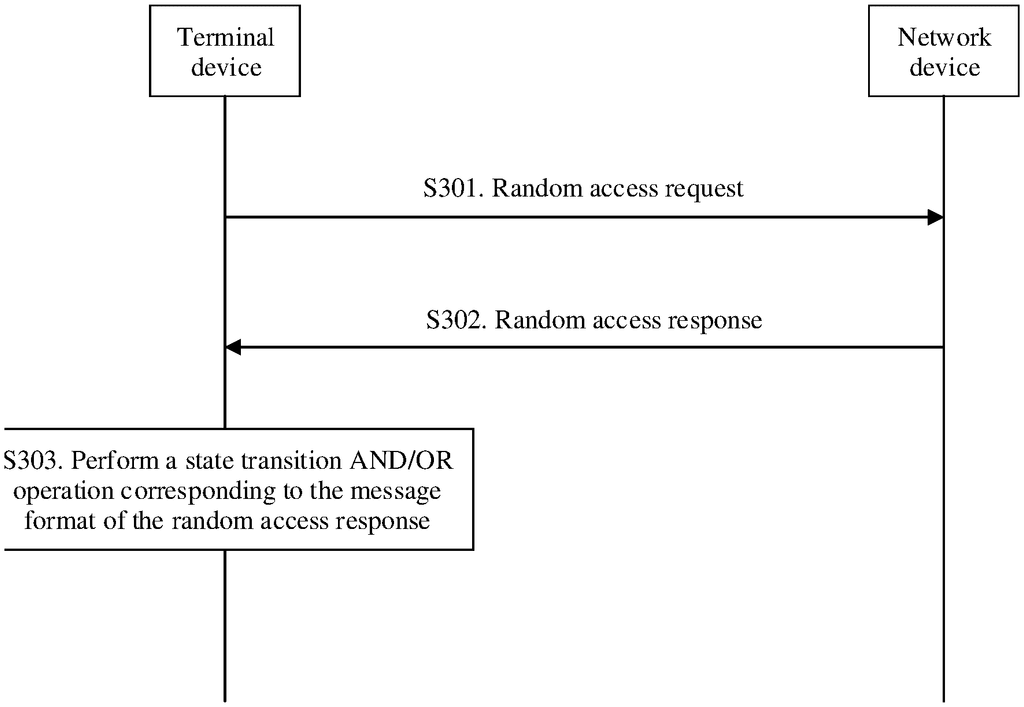
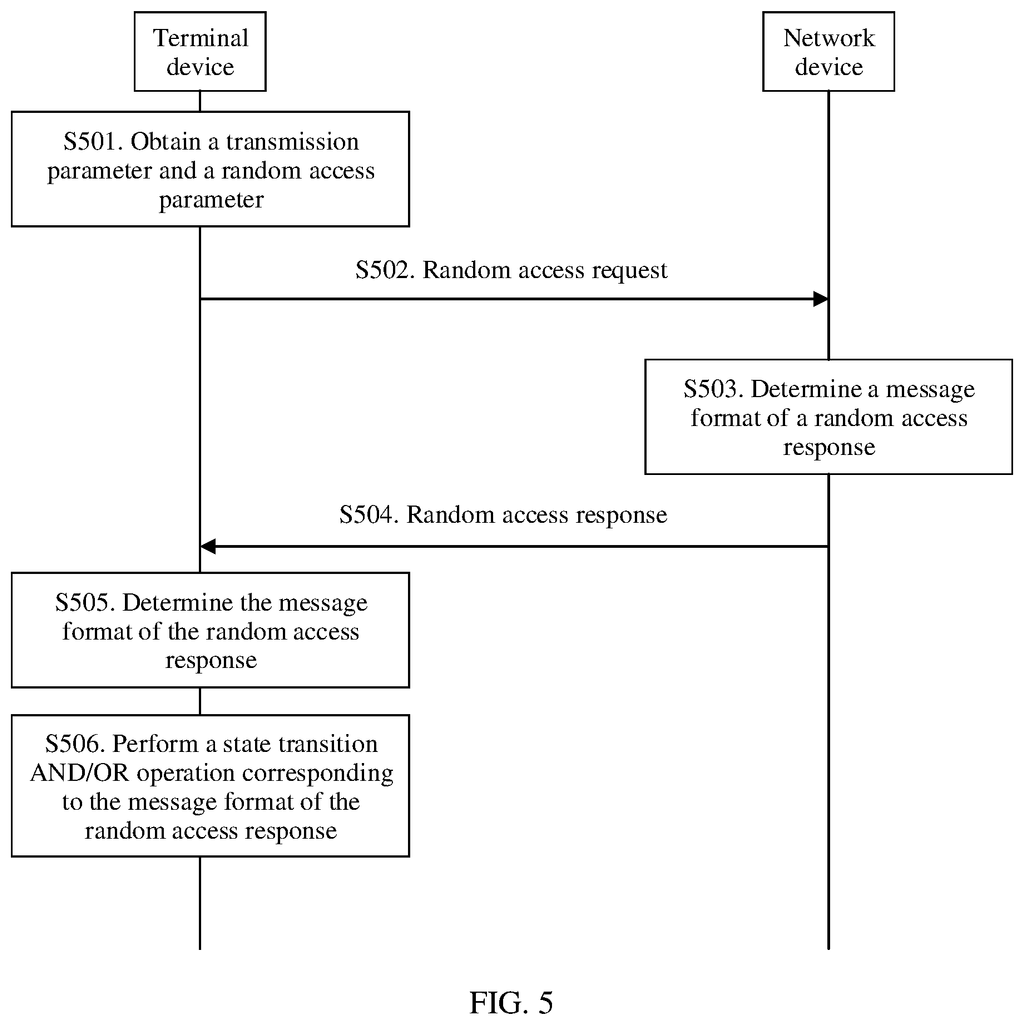
The method includes sending a random-access request by a terminal to a network device. This random-access request contains a random preamble as well as uplink data. Receiving a response from the network device by the terminal, and performing a state change AND/OR operation by the terminal, which corresponds to the message format of the response.
Background for Communication Method and Apparatus
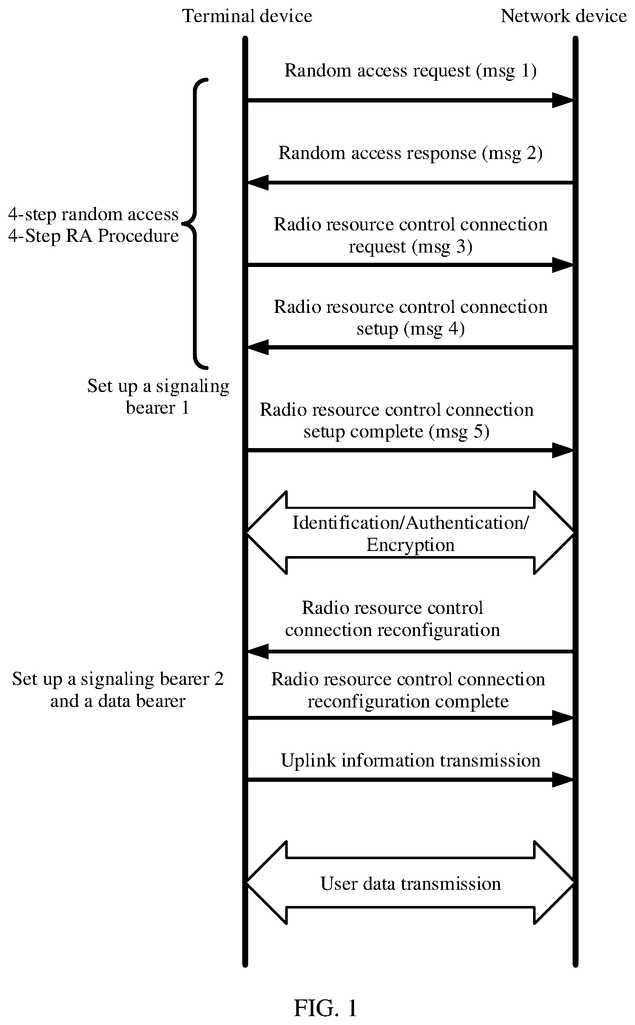
In a Long Term Evolution (LTE) communication system, the radio resource control (RRC), has generally two states: an active state and a passive state. In the next-generation wireless communication system, such as the fifth-generation mobile communication system (5G), an additional state is introduced, called inactive. Both a terminal and a network store the access stratum context information (AS context) of a RRC connection from the connected state in the inactive state. In order to restore the original connection when the terminal device switches between the inactive and connected states, it is necessary to perform a random access process. The terminal device can send data to a network device after entering the connected state. FIG. FIG.1 is a diagrammatic representation of the random access procedure used in the LTE network. The terminal device switches from an idle state to a connected state by four interactions, then sends the data. “In the inactive state there is no solution to how the terminal device communicates with the network.
This application provides a method of communication and a communications device to implement data communication between an inactive terminal device and the network side.
The first aspect of the application provides a communication technique that includes a terminal device sending a random request to a device on a network, wherein the random request contains a random preamble, user data and control information. Furthermore, the terminal receives a response from the device and performs a state change AND/OR operation in accordance with the message format. In the first instance, the terminal in an inactive state adds both the connection identifier as well as the authentication identifier in order to implement data communication between a terminal device and network. The network device will discard the user data if it does not receive the authentication or connection identifier. In this case, the current data communication initiated from the terminal device is invalid data communications, or in other words data communication between terminal device and network device fails.
In an implementation, performing a state-transition AND/OR operation by the device corresponds to a message form of the response. This includes: switching by the device to a connected status based upon the response, maintaining the device in an inactive mode and adjusting the uplink time based upon the response, maintaining the device in an inactive mode based upon the response, in which data corresponding the response is sent successfully, maintaining the device in an inactive or idle state by switching by the device to a fourth format This implementation instructs the terminal device to perform state transition AND/OR operation based on random access responses of different message formats.
In another implementation, “the method also includes obtaining a transmission parameter by the terminal, where the parameter includes: at least one of these parameters: a time frequency resource used to send the control data and user data; a modulation scheme parameter and an encryption parameter; a cyclic length parameter and a signal reference parameter. The sending by a terminal, a random request to a device on a network includes sending the control data and user data by using the parameter.
In a further implementation, the method includes obtaining a randomly access parameter by the terminal device. The random access parameter comprises at least one parameter from the list below: a random preamble generation parameter with a time-frequency resource corresponding to it, a parameter for the random response window, a parameter related to the beam, a random preamble subset division mode, and a parameter for the backoff.
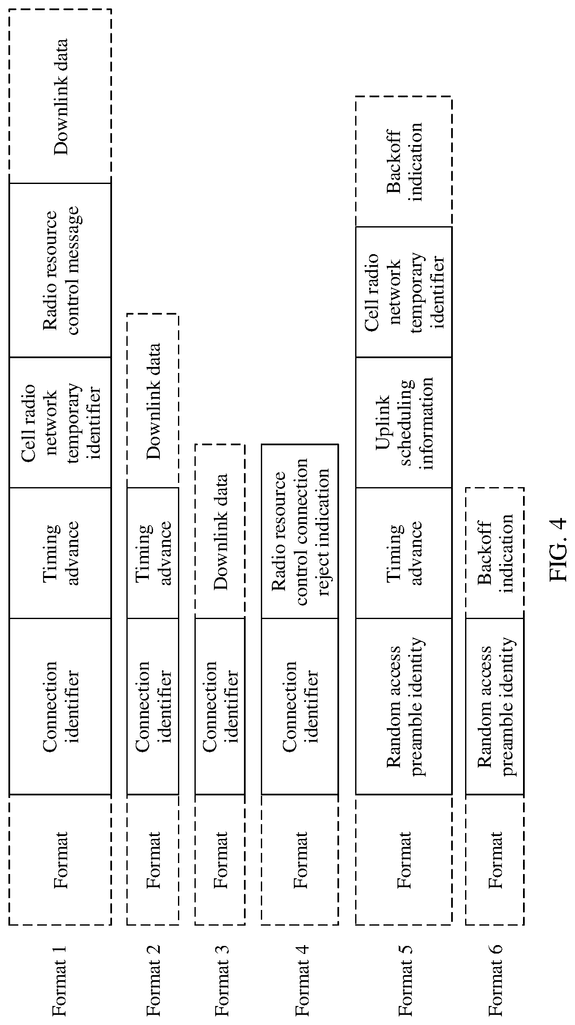
In a third implementation, the method includes the terminal device determining the message format for the random response by examining a message field within the random response. In this implementation, a message format is defined in the random response. The terminal device can then determine the message of the random response by referring to the message field.
In a third implementation, the method includes the following: Obtaining, by the Terminal Device, a Transport Block Size corresponding to he random access reply, and determining by the Terminal Device, the message formatting of the random response based upon the transport block. Each message format corresponds to ONE transport block, while different message formats corresponds to DIFFERENT transport block sizes. The terminal device can determine the message format for the random response using the transport block size that corresponds to the random response in this implementation. This will reduce signaling overheads.
In a third implementation, the terminal device receives downlink information that corresponds to the random response. The downlink information contains message format information for the random response. Based on this downlink information, the terminal device determines the message format for the random response. The message format for the random response is included in the downlink information. This allows the terminal to determine the format of the response by analyzing the message information.
In a third implementation, a terminal device determines, based on the time window that it receives the random response, the message format. Each message format corresponds to a different time window. In this implementation, a network device sends a random access reply in different time frames. The terminal device can determine the message format based on which time frame it receives the response.
According to a second part of this application, there is a method for communication that includes receiving, from a network device a random request sent by a device terminal, wherein the random request includes user data, a random preamble and control information. The terminal device is also in an inactive mode, while the control information contains at least an authentication identifier. In the second aspect of the invention, the network device is able to receive the random request from the terminal in an inactive state. The random request contains the connection identifier as well as the authentication identifier. This allows for data communication to be implemented between the terminal and the network. The network device will discard the user data if it does not receive the authentication or connection identifier. In this case, the current data communication initiated from the terminal device is invalid data communications, or in other words data communication between terminal device and network device fails.
In an implementation, the method also includes determining by the network device a message formatting of the random response based at least on one of the factors listed below: a result of detection of the random preamble; a result of decoding and parsing of the control data and user data; and a result of current network status. The message format for the random response is decided in this implementation based at least on the detection result of random access preamble and the decoding and interpreting result of control information and user data.
The network device can indicate the message formats of random response responses in one or more of the following ways: the random response response includes a field for a message, which is used to indicate a message, the network sends downlink information that includes the message, including a second downlink information that includes the message. The message field of the randomly selected response is displayed, and terminal devices can easily determine the format of that response. Alternatively, terminal devices can use the transport block sizes to determine the format, resulting in a small signaling overhead.
In a further implementation, receiving a random request by a network is performed by receiving a plurality random requests sent by terminal devices using different beams. The method also includes selecting by the device a random request from the plurality based on the specified signal quality conditions. Finally, sending a response by the device to the terminal includes sending the response that corresponds to the randomly selected request. This implementation allows the terminal device to send the plurality random requests using a plurality beams. The network device can then select a random request from the plurality that matches the specified signal quality condition.
The random response format in this implementation is one of: “With reference both to the first and second aspects, it is one of: the first format where a random response includes a number of fields, including a connect identifier; the second format where a random response includes a timing advance and connection identifier; the third format where a random response includes a link identifier; the fourth format where a random response includes a radio control connection rejection indication and the fifth format where a random response includes a The random access response can be in a variety of message formats. These message formats are associated with different state transition AND/OR operation.
In another implementation “with reference to the first and second aspects, in a terminal device in the inactive mode, the connection is used either to identify radio resource connection context information before switching from the connected to inactive states, or to identify the access stratum that is of radio resource connection context and is stored after the terminal device switches to inactive mode.” In this implementation the terminal device adds both the authentication identifier and connection identifier to a random request so that data can be communicated between the terminal and network.
In a third implementation, the network device uses the authentication identifier to perform identity verification on the terminal device.
With reference to the first aspect and the second aspect, in still another implementation, the control information may further include at least one of the following information: a data transmission reason and a switch-to-the-connected-state request.
According to a third feature of this application, there is a communication apparatus that can implement the above-mentioned method. The communications apparatus can be, for example, a chip such as a baseband or communications chip or device (such a terminal device). The method described above can be implemented using either software or hardware or by hardware that executes corresponding software.
In a possible implementation, the structure of the communication apparatus could include a processor and memory. The processor is designed to assist the apparatus with performing the corresponding function of the communication method. The memory, which is coupled to the processor and stores data and/or a program for the apparatus, is configured to store a program or instruction. The communications apparatus can include an optional communications interface configured to facilitate communication between the apparatuses and other network elements.
In another possible implementation of the communications apparatus, it may include a transmitting unit, a reception unit, and a processor unit. The sending unit, the receiving unit and the processing module are configured to perform a sending and receiving function respectively in the above method. The sending unit, for example, is configured send a randomly access request to a device on a network, where the random request includes control information and user data.
Click here to view the patent on Google Patents.