Invented by Jin KOCSIS, Yifu Wu, Gihan Janith Mendis IMBULGODA LIYANGAHAWATTE, University of Akron
A blockchain-empowered crowdsourced computing system is a decentralized network of computers that work together to solve complex computational problems. These systems are powered by blockchain technology, which ensures that the network is secure, transparent, and tamper-proof.
The market for blockchain-empowered crowdsourced computing systems is growing rapidly, and it is expected to reach $9.2 billion by 2025. This growth is being driven by the increasing demand for computing power, as well as the need for more secure and transparent computing systems.
One of the key benefits of blockchain-empowered crowdsourced computing systems is that they are highly scalable. This means that they can easily handle large volumes of data and computational tasks, making them ideal for use in industries such as finance, healthcare, and logistics.
Another benefit of these systems is that they are highly secure. Because they are powered by blockchain technology, they are resistant to hacking and other forms of cyber attacks. This makes them ideal for use in industries where data security is of the utmost importance.
In addition to these benefits, blockchain-empowered crowdsourced computing systems are also highly transparent. Because the blockchain is a public ledger, all transactions and computations are visible to everyone on the network. This ensures that there is no room for fraud or manipulation, making these systems ideal for use in industries where transparency is essential.
Overall, the market for blockchain-empowered crowdsourced computing systems is poised for significant growth in the coming years. As more industries recognize the benefits of these systems, we can expect to see increased adoption and innovation in this space.
The University of Akron invention works as follows
In various embodiments, this invention is directed towards a decentralized, secure method of developing machine learning model using blockchain smart contracts and homomorphic cryptography. This secure, decentralized, and privacy-preserving computing systems incentivizes sharing private data, or at least sharing the resultant machine learning model from the analysis private data. The method in various embodiments uses a homomorphic-encryption (HE)-based interface to ensure privacy and security of shared learning models while minimising computation overhead.
Background for Blockchain-empowered crowdsourced computing system
Big data analytics is a valuable tool that can be used for many applications. It is difficult to implement big-data analytics due to the large amounts of data that must be acquired and the computing power required to process the data. Many of these challenges can be addressed by using a dominant cloud vendor. However, while commercial cloud vendors offer valuable platforms for big-data analytics, there are some downsides, including a lack in transparency, security and privacy. Cloud servers are also a barrier to applying big data analytics where computing power is distributed.
The present invention, in one or more embodiments is directed towards a secure and decentralized computing system for developing machine-learning models. The system uses blockchain smart contracts that are executed on a blockchain platform that is networked and has the capability to run scripts, i.e. a programming language for programs that are written to automate the execution of tasks. It also provides a user-interface at some or all nodes of the network. Blockchain smart contracts are used to create a decentralized and secure computing system, which preserves privacy and encourages public sharing of computing power. The system also encourages the sharing or analysis of private information, and the resulting machine learning models. This system uses blockchain smart contracts, decentralized learning and software defined network techniques. It can be implemented in many different fields such as cognitive communication in deep space/near-space exploration, next-generation vendor independent data sharing and analyses, mobile cloud-sensing, and critical infrastructure monitoring.
One or more embodiments of the present invention provides a method for developing machine learning models through a decentralized and secure computing system, the method comprising the steps of: establishing a peer to peer (P2P) network running on a blockchain platform and including a plurality of nodes capable of acting as any one of an application initiator node, a computing contributor node, and a verification contributor node; wherein the application initiator node: defines a task for generating a machine learning model, the task being defined through a blockchain smart contract, and broadcasts the task to P2P network via the blockchain smart contract such that the plurality of nodes receive the task and assist in the task as either computing contributor nodes or verification contributor nodes; wherein each computing contributor node: employs contributor-available data to generate a private model for achieving the task, encrypts the private model, and provides the encrypted private model for access by verification contributor nodes; wherein each verification contributor node: accesses the encrypted private model, tests the private model to determine if it achieves the task, and informs the application initiator node if a private model satisfies the task. The method may also include decentralized storage that can be accessed by computing contributor nodes and verification contributors.
In some embodiments, an application initiator node may provide data or an initial model of machine learning or both data and a model of machine learning to decentralized storage so that computing contributors or verification contributors or both computing and verification contributors can access it.
In one or more embodiments, homomorphic encryption is used to encrypt the private model. In some of these implementations, the private models are encrypted using substantially homomorphic cryptography. In one or several of these embodiments a public and secret key is generated by the application initiater or the blockchain smart contracts and/or the blockchain platform, as directed by application initiator. Said public key allows encryption of testing documentation in the same way as the private models so that the model can be tested in cipherspace. In some embodiments, the secret keys may be used to decrypt private models.
In one or more embodiments, the present invention is directed to a method for developing machine learning models through a decentralized and secure computing system, the method comprising the steps of: establishing a peer to peer (P2P) network running on a blockchain platform and including a plurality of nodes capable of acting as any one of an application initiator node, a computing contributor node, and a verification contributor node and decentralized storage accessible by said plurality of nodes; wherein one of said plurality of nodes elects to act as an application initiator node, prepares a blockchain smart contract on said blockchain platform, said blockchain smart contract defining a task for generating a machine learning model, the criteria for selecting one or more nodes of said a plurality of nodes to act as verification contributor nodes, the criteria for verifying completion of the task, and the criteria for triggering a transfer event, said task being broadcasts the to the P2P network via the blockchain smart contract such that the plurality of nodes receive the task; wherein said application initiator node generates a public key available to all of the nodes on said P2P network and a secret key available only to said application initiator node; wherein each node receiving the tasks elects whether to assist with the task by acting as a computing contributor node, with the proviso that at least one of said plurality of nodes elects to act as a computing contributor node; wherein each of said plurality of nodes acting as a computing contributor node employs contributor-available data to generate a private model for achieving the task, and stores the encrypted private model on the decentralized storage; wherein one or more of said plurality of nodes is selected to act as a verification contributor node according to the terms of the smart contract; wherein each verification contributor node accesses the encrypted private model, tests the private model according to the criteria set forth in the smart contract to determine if it achieves the task, and informs the blockchain smart contract on said blockchain platform if the private model satisfies the task; and wherein said blockchain smart contract on said blockchain platform determines whether the criteria for triggering a transfer event have been met, and if they have been met then allows said application initiator node to access and decrypt said private model.
In one or more embodiments, homomorphic encryption is used to encrypt the private model. In some embodiments, the model is encoded using homomorphic encryption. In some of these embodiments the public key allows encryption of test documents in the same way as the private models so that the model can be tested in cipherspace. In some embodiments, a secret key can be used to decrypt a private model.
The following is a detailed explanation of the disclosure to assist those in the know in implementing the present disclosure. The embodiments described in this document may be modified and varied by those of ordinary skill without departing the spirit or scope the disclosure. All technical and scientific words used herein, unless otherwise defined, have the same meaning that is commonly understood by a person of ordinary skill in this art. The terminology used to describe the disclosure in this document is intended only to describe particular embodiments and not as a limitation of the disclosure.
The following terms could have different meanings, unless otherwise specified. The terms “comprising” are used in this document. ?to comprise? The terms?to include? and?to comprise’ do not exclude that there may be additional elements or steps to the ones listed in the claim. The terms ‘a,’ ‘an? ?an? The use of?an? The use of the word ‘before’ an element or feature doesn?t exclude the possibility of multiple elements or features, except when the context makes it clear. The term “means” is also used. The term?means? is used in many claims, but this does not mean that they are all the same.
The reader should read all publications, patent applications and patents mentioned in this document and consider them as part of the text. The only reason why the document, reference or patent application cited in this article is not repeated is for conciseness. If there is a conflict, the current disclosure will prevail, including the definitions. “All technical and scientific terminology used herein has the same meaning.
Furthermore, any compositions or method provided herein may be combined with any or all of the other compositions or methods.” It does not matter that certain features, components, or elements are mentioned in multiple dependent claims. At least some of those features, components, or elements may be used together.
To address the challenges of implementing big data analytics, as described in the Background section above, we provide a secure and decentralized computing system for developing machine-learning models. The system uses blockchain smart contracts, which are programs that run on blockchain platforms and can execute scripts (i.e. a programming language for automating tasks). Blockchain smart contracts are used to create a decentralized and secure computing system, which preserves privacy and encourages public sharing of computing intelligence and power. The system also encourages the sharing or analysis of private information, and the resulting machine learning models. This system uses blockchain smart contracts, decentralized learning and software defined network techniques. It can be implemented in many different fields such as cognitive communication in deep space/near-space exploration, next-generation vendor independent data sharing and analyses, mobile cloud-sensing, and critical infrastructure monitoring.
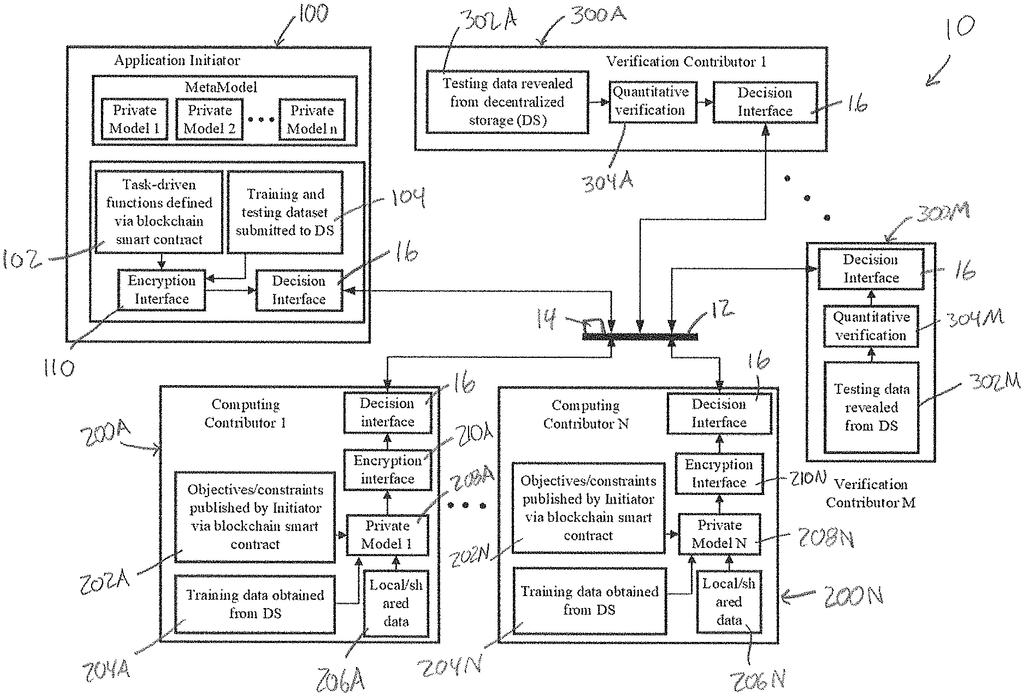
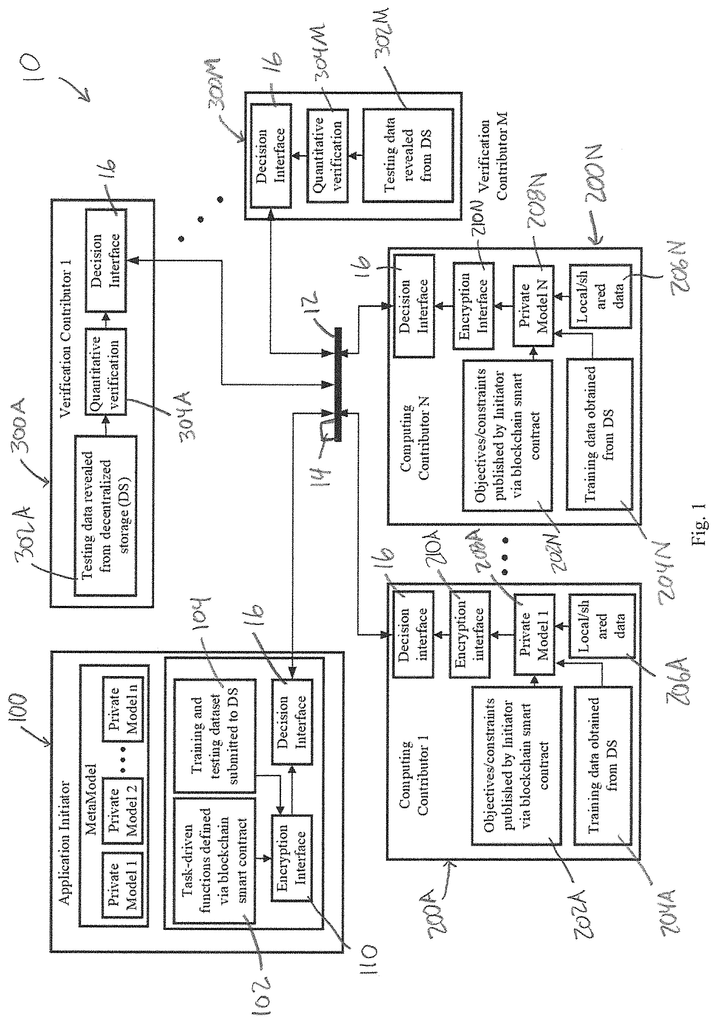
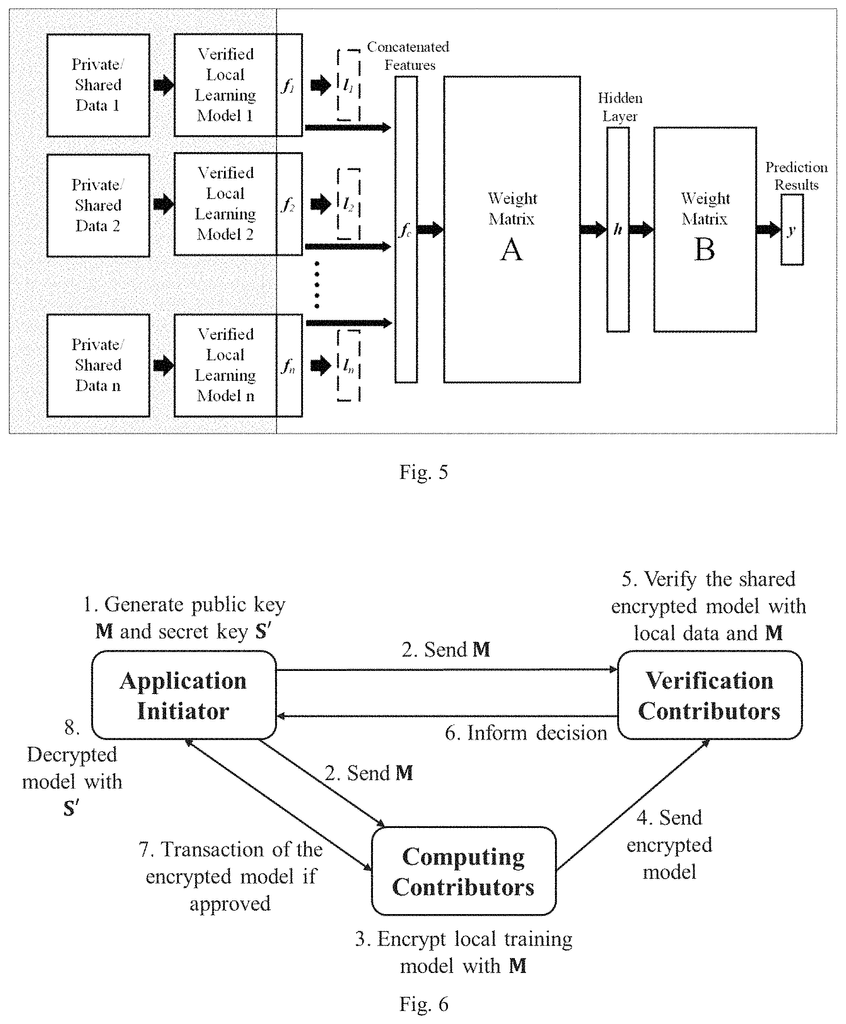
In FIG. In FIG. 1, a decentralized, secure computing system is shown. It has been designated with the number 10 and allows for the development of machine learning models according to various embodiments. A peer-to-peer network 12 with a plurality nodes is included in the system. Nodes can be involved in developing machine learning models as either application initiators or computing contributors. The application initiater acts at application initiator 100. In FIG., there is at least one computing participant. The computing participants act on computing contributor nodes. There are two computing contributors in FIG. 1, a computing node 200A, and a second computing node 200N. This indicates that there may be n computing contributors. At least one verification contributer is present, and they act on the verification nodes shown in FIG. There are two verification contributors in FIG. 1, a 300A and 300M. This indicates that there may be as many m computing contributors. “All nodes in peer-to-peer network 12 including application initiator nodes, computing contributors, 200A, 200N and verification contributors, 300A,300M communicate with each other and the smart contract through the blockchain platform.
The application initiator 100 initiates a participation request in developing a model of machine learning by initiating smart contracts on the Blockchain platform. The smart contract specifies the performance targets for a machine-learning model that will be developed by implementing the system 10. The smart contract will define the compensation for participating nodes as well as other criteria to implement the system 10. The nodes that accept the task will become computing contributors, nodes 220 and 200N. They will process the data they have available and generate a private model locally using the computing power and the data at their disposal. This private model is then shared with nodes chosen by the smart contract programming to be verification contributors, nodes 300A and 300M. The verification contributor nodes, 300A, and 300M, analyze the private models to determine which ones, if any satisfy the performance criteria set forth in the blockchain smart contracts. The verification contributor nodes inform the application initiator via the smart contract that runs on the blockchain platform if they determine a certain private model meets the target performance criteria. If all the conditions of the smart contracts are met, the verified private models will be made available to application initiator and the compensation will be paid to computing contributor and verification contributor nodes in accordance with the terms of the contract. The system is able to share private data without causing security issues, as private data can be kept local and private.
The term “node” is used in this document. “As used herein, the term ‘node(s)’ is to be understood as referring to peer-to-peer (P2P), where computers are connected and referred to as ‘peers’ All nodes are responsible for providing network services. The services are decentralized, and the nodes provide and consume them. Reciprocity is used as an incentive to participate. The core characteristics of blockchain are that P2P networks have inherent resilience, are de-centralized and open to all. Nodes are the computing hardware and communication software required to perform the actions for each participant/node in the system. It includes peer-to-peer networking, as well as the creation and sharing of machine learning model. In certain embodiments, a P2P network can be selected from among a TCP/IP, software-defined network or other networking infrastructures. In some embodiments, the P2P is a software-defined network (SDN) to realize resilient peer-topeer (P2P), networking infrastructure which enables flexible configurations. A person of ordinary skill will be able select the hardware and software necessary to form a network node without excessive experimentation.
In some embodiments, these nodes may implement the big.LITTLE architecture (ARM Holdings, (Cambrideshire, UK)), which combines energy-efficient cores like ARM Cortex-A53, and Cortex A55 with high performance cores such as ARMCortex-A57, CortexA72, CortexA73, and ARMCortexA75. In some embodiments, the nodes will implement the big.LITTLE (ARM Holdings (Cambrideshire)) architecture, which combines energy-efficient cores (ARM Cortex A53 and Cortex A55) with high-performance cores (ARM Cortex A57, Cortex A72, Cortex A73, and Cortex A75). In some embodiments a Qualcomm Snapdragon 835, which uses the big.LITTLE of an advanced version ARM Cortex A57 and Cortex A53, is used. It will be understood that Cortex A53-based Cores are used for simple tasks, and Cortex A57-based Cores are used to perform heavy tasks on mobile phones.
A node from the peer-to-peer network 12 becomes a application initiator 100 when it initiates a smartcontract on a Blockchain platform. The smart contract opens the door for other nodes to participate in developing a model of machine learning. As shown at 102, the application initiator 100 defines a task to generate a machine-learning model. The task is defined by a blockchain smartcontract. In certain embodiments, the application initiator 100 can provide data to be used by computing contributor nodes (200A-200N) in training their models and, if desired by them, testing those models. In certain embodiments, data can be included in the blockchain smart contract for computing contributor nodes to use during training or, if desired by testers of their private models. Some data sets may be too large to share through a blockchain smart contract. In these cases, sharing data via other means such as decentralized data storage is beneficial. In certain embodiments, the application initiater node 100 may provide an initial machine-learning model (or “initial model?”) “The computing contributor nodes (200A, 200N) can use the initial machine learning model (or?initial model?)
To securely transfer data, and computing models is a decentralized file storage and sharing mechanisms as shown in decentralized storage 14. Decentralized storage 14 receives data and computing models that are shared by nodes such as application initiator, computing contributor, and verification initiator. Decentralized storage 14 is provided with encryption keys to decrypt data or computing models. At encryption interface 110, in some embodiments when an application initiator provides data or a model, they are encrypted and uploaded to decentralized storage 14. Communication with peer-to-peer network 12 (and shown in FIG. “1 for each node of system 10.
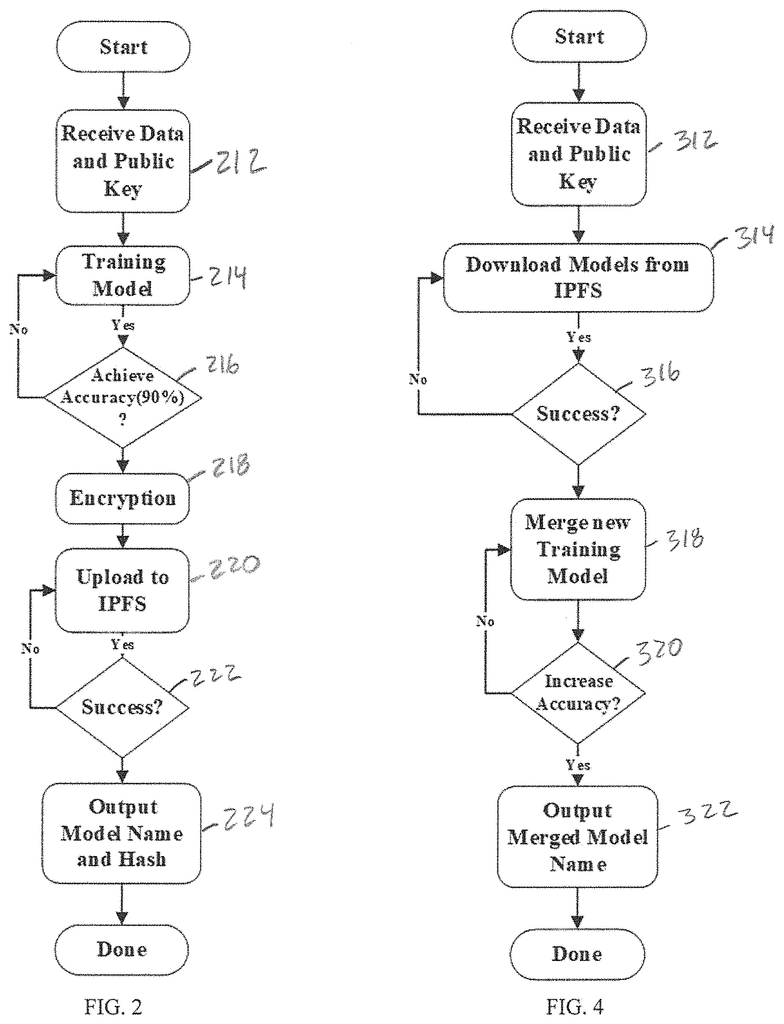
After initiating an intelligent contract on the Blockchain platform, the application initiater node 100 creates a public and secret key using homomorphic encryption technology. In some embodiments the public key is generated automatically by the smart contract. The public key allows the encryption of test documents in the same way as the private model, so that the model can be tested in cipherspace. It also enhances the privacy of the models generated by computing contributors. The computing contributors can also use the public key in order to encrypt their locally generated computing models before they are announced on the blockchain platform. As described below, the secret key can be used to enable the application initiator (with the name and hash value) to retrieve the private model that is satisfactory, which is stored in cipherspace. In some embodiments, both the computing and verification contributor nodes are provided with the public key to enable them to encrypt private models and test documents. In certain embodiments, both the public key as well as the secret key is delivered or sent automatically to the decentralized storage 14. Below, we will discuss more specific embodiments of the encryption process. This is particularly true with regard to FIG. 6.
Virtually, any decentralized storage system may be used.” In certain embodiments, the decentralized system can be used in conjunction with the blockchain platform that is being used to create the smart contract. In some embodiments an Interplanetary File System distributed file storage is used. IPFS, like blockchain, uses the peer-topeer network for sharing and storing hypermedia on the Internet.
The blockchain smart contract is a programming that defines the objectives and constraints for computing tasks. This includes the properties of the input data, expected outputs of tasks and verification criteria. The programming can also execute process steps in the system according to the smart contract. In certain embodiments, public-key technologies are used to control the visibility of variables in a blockchain smartcontract. Public-key cryptography is used in various embodiments to control the visibility of names and hash values for computing models that are transmitted via the blockchain smart contracts.
Click here to view the patent on Google Patents.